Intersection data generation method and federated model training method based on intersection data
A data set and data technology, applied in the field of data transmission, can solve problems such as user information leakage, and achieve the effect of solving leakage and improving data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
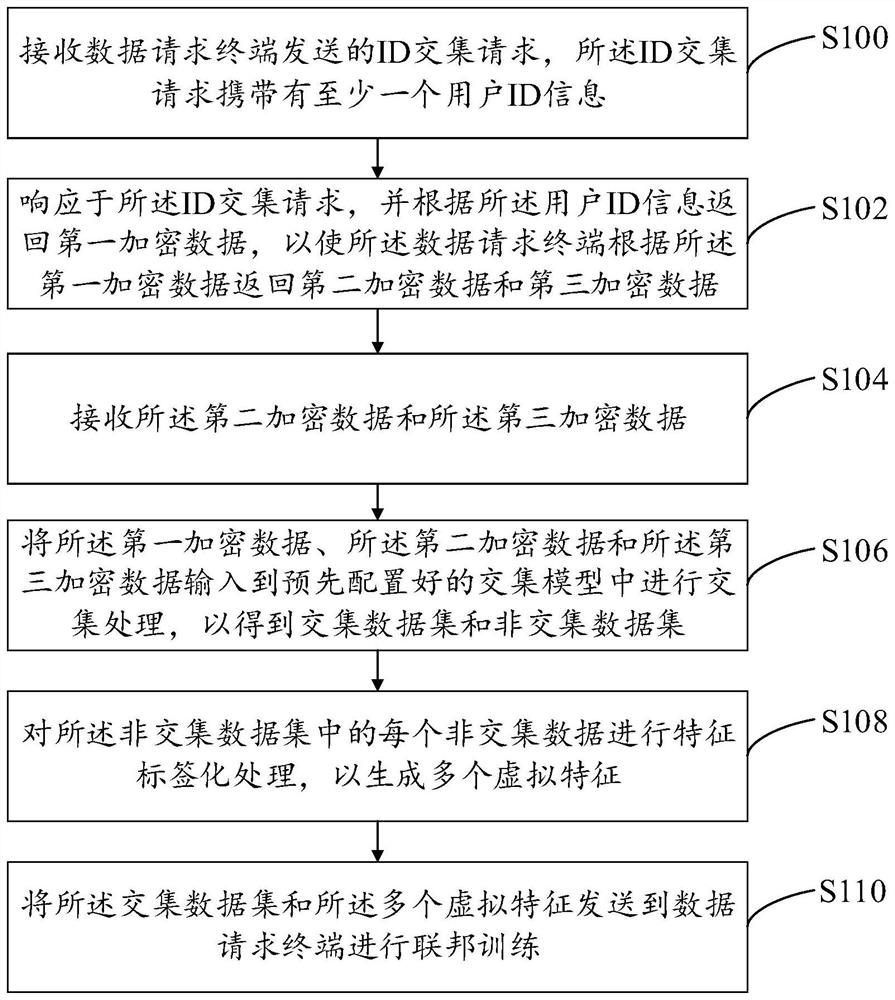
[0049] refer to figure 1 , shows a flow chart of the steps of the method for generating intersection data according to the embodiment of the present invention. It can be understood that the flowchart in this method embodiment is not used to limit the sequence of execution steps. The following is an exemplary description using a data providing terminal as an execution subject. The data providing terminal is a data providing end and can perform an encryption operation on data. details as follows.
[0050] Step S100, receiving an ID intersection request sent by a data requesting terminal, where the ID intersection request carries at least one user ID information.
[0051] The data providing terminal may receive the ID intersection request sent by the data requesting terminal, where the ID intersection request carries at least one user ID information.
[0052] The data requesting terminal is the initiator of the service request and has the function of sending a request to the d...
Embodiment 2
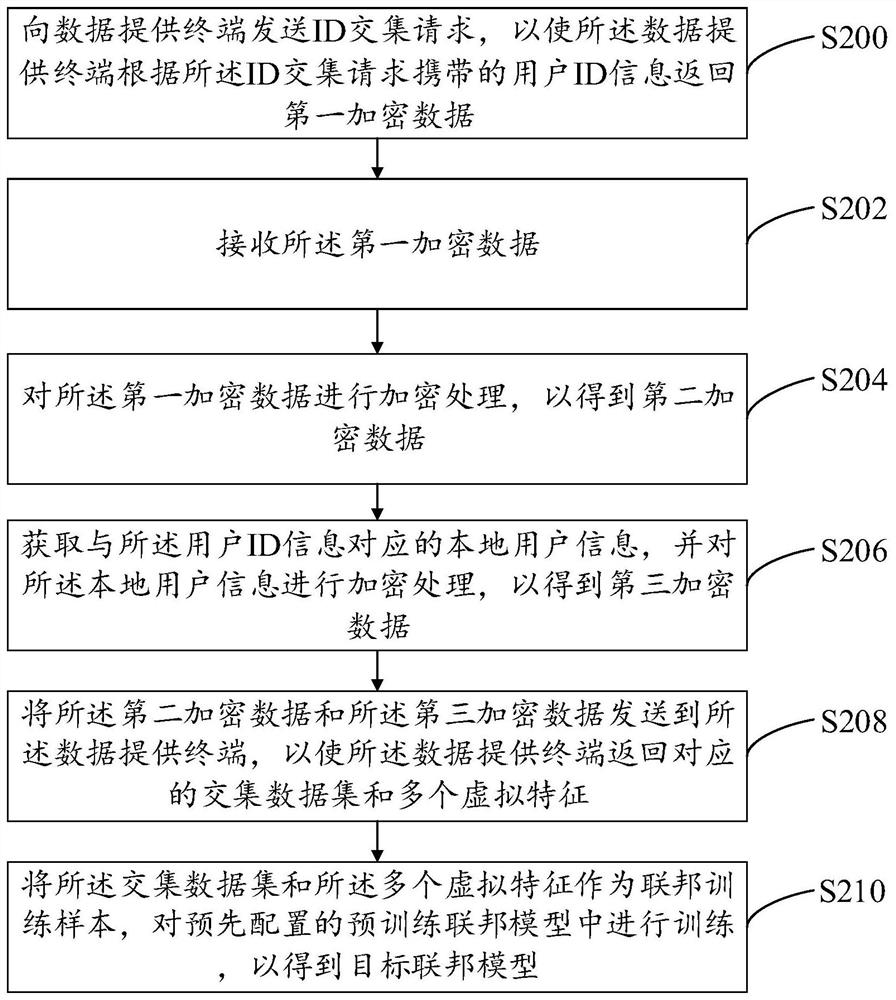
[0074] refer to figure 2 , shows a flowchart of the steps of the federated model training method based on intersection data according to an embodiment of the present invention. It can be understood that the flowchart in this method embodiment is not used to limit the sequence of execution steps. The following is an exemplary description using a data requesting terminal as an execution subject. The data requesting terminal may send request information to a data providing terminal, so that the data providing terminal returns corresponding data. details as follows.
[0075] Step S200, sending an ID intersection request to the data providing terminal, so that the data providing terminal returns first encrypted data according to the user ID information carried in the ID intersection request.
[0076] The ID intersection request is used to instruct the data providing terminal to return corresponding encrypted data according to the ID intersection request.
[0077] The data reque...
Embodiment 3
[0092] image 3 It is a schematic diagram of program modules of Embodiment 3 of the intersection data generation system of the present invention. The intersection data generation system 30 may include or be divided into one or more program modules, one or more program modules are stored in a storage medium, and executed by one or more processors to complete the present invention, and may Implement the method for generating the above intersection data. The program module referred to in the embodiment of the present invention refers to a series of computer program instruction segments capable of completing specific functions, which is more suitable than the program itself to describe the execution process of the intersection data generation system 30 in the storage medium. The following description will specifically introduce the functions of each program module of the present embodiment:
[0093] The request receiving module 300 is configured to receive an ID intersection req...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com