System anomaly detection method and system based on depth log sequence analysis
An anomaly detection and sequence analysis technology, applied in neural learning methods, digital data information retrieval, unstructured text data retrieval, etc. The effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] The purpose of this embodiment is to provide a system anomaly detection method based on deep log sequence analysis.
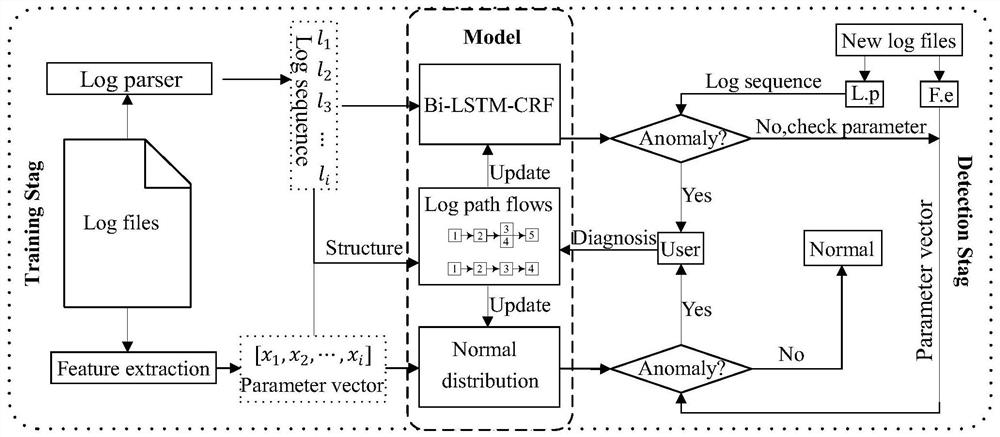
[0035] Such as figure 1 As shown, in this embodiment, a system anomaly detection method based on deep log sequence analysis is provided, including:
[0036] Obtaining a log event historical data set, parsing the log event, and dividing the log event data set into several log sequences according to the parsed identifiers;
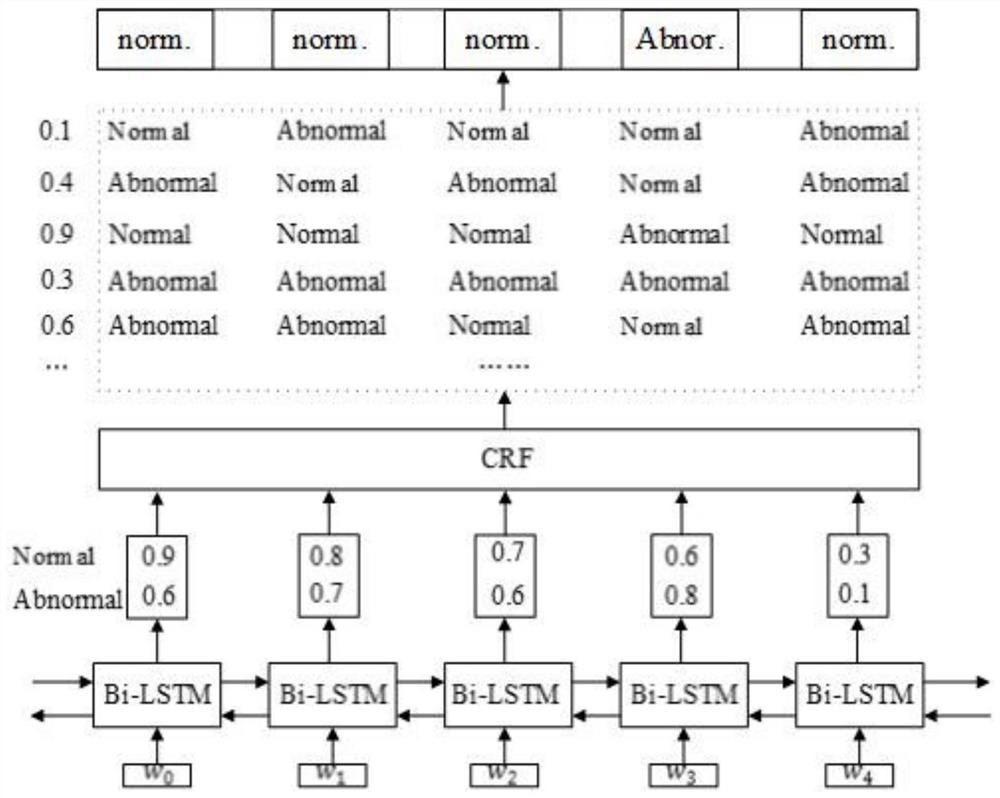
[0037] Using the log sequence as input, the Bi-LSTM-CRF model is trained;
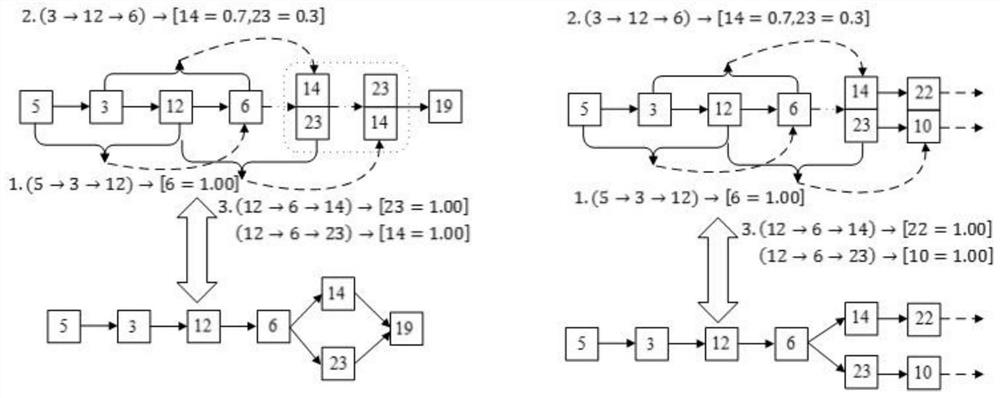
[0038] Use the trained Bi-LSTM-CRF model to perform path anomaly detection on the log sequence to be detected;
[0039] Perform feature extraction on the analyzed log event, extract all parameters from the log event with the same identifier to construct a parameter vector, and use a normal distribution model to fit the parameter vector;
[0040] Perform parameter anomaly detection for log events in the log sequence to be tested through the normal distributio...
Embodiment 2
[0086] The purpose of this embodiment is to provide a system anomaly detection system based on deep log sequence analysis.
[0087] A system anomaly detection system based on deep log sequence analysis, including:
[0088] The data preprocessing module is used to obtain the log event historical data set, analyze each log event, and divide the log event data set into several log sequences according to the identifier obtained by parsing; and characterize the parsed log event Extract, extract all parameters from the log event with the same identifier to construct a parameter vector;
[0089] A model training module, for using the log sequence as input to train the Bi-LSTM-CRF model; and using a normal distribution model to fit the parameter vector;
[0090] The path anomaly detection module is used to utilize the trained Bi-LSTM-CRF model to perform path anomaly detection on the log sequence to be detected;
[0091] A parameter anomaly detection module, configured to perform pa...
Embodiment 3
[0094] The purpose of this embodiment is to provide an electronic device.
[0095] An electronic device, comprising, a memory, a processor, and a computer program stored on the memory, and the processor implements the following steps when executing the program, including:
[0096] Obtaining a log event historical data set, parsing the log event, and dividing the log event data set into several log sequences according to the parsed identifiers;
[0097] Using the log sequence as input, the Bi-LSTM-CRF model is trained;
[0098] Use the trained Bi-LSTM-CRF model to perform path anomaly detection on the log sequence to be detected;
[0099] Perform feature extraction on the analyzed log event, extract all parameters from the log event with the same identifier to construct a parameter vector, and use a normal distribution model to fit the parameter vector;
[0100] Perform parameter anomaly detection for log events in the log sequence to be tested through the normal distribution...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com