Image encryption method and device, image decryption method and device, equipment and readable storage medium
An encryption method and image technology, applied in the field of information transmission, can solve problems such as being unsuitable for image encryption, and achieve the effect of fast decryption operation and high security.
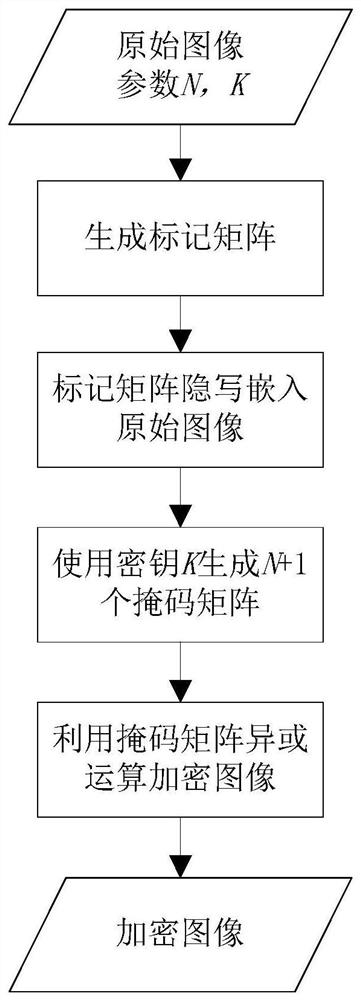
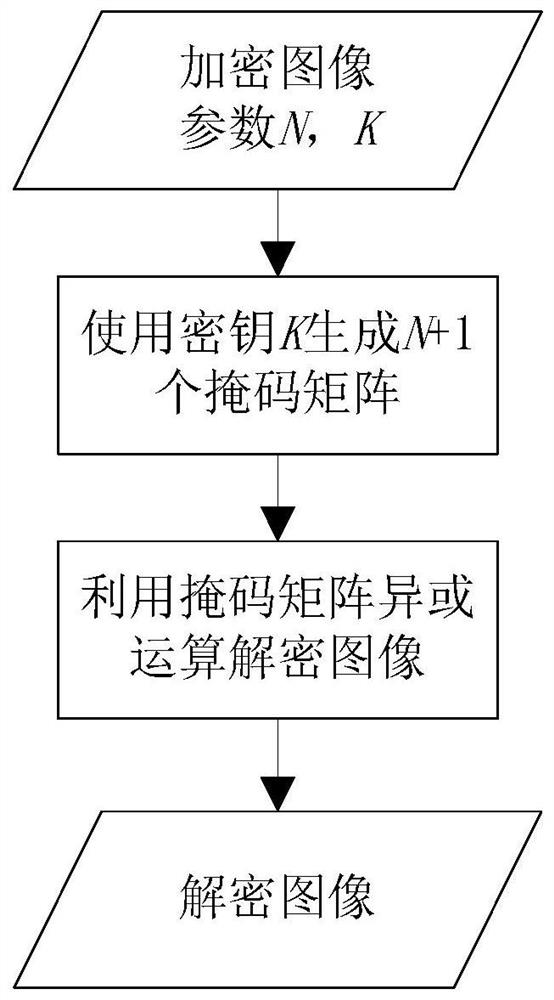
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0093] Next, take an 8*8 color BMP image, select N=4 as an example, and use the RGB three color channels of the BMP image. The encryptor encrypts the original image as three images respectively. Taking one of the color channels as an example, the steps are as follows :
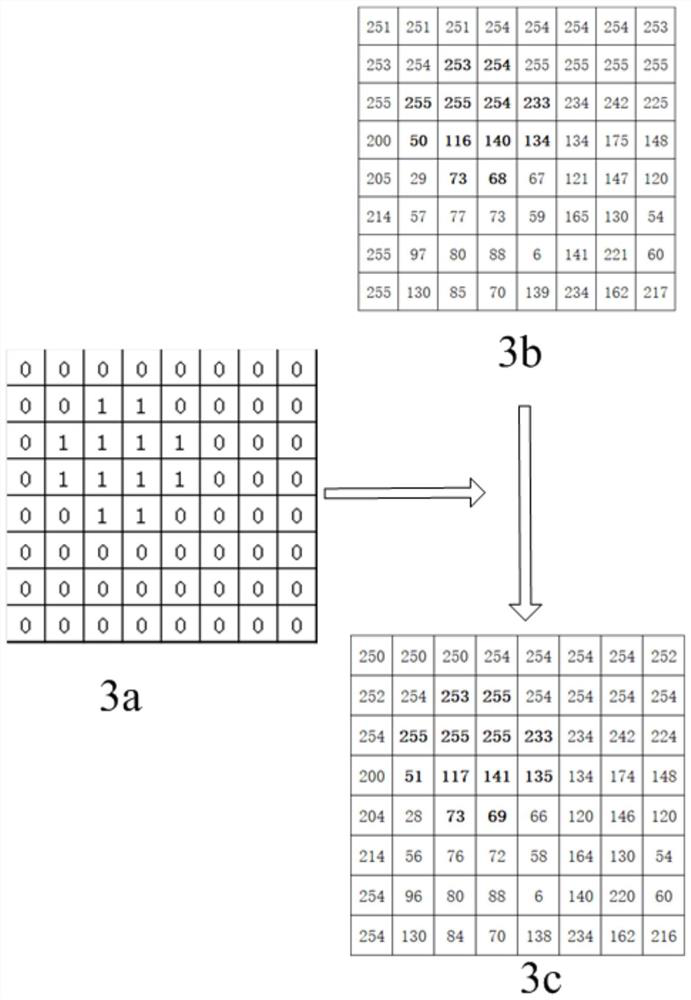
[0094] see image 3 , which is the process of replacing the lowest bit of a single pixel of the original image with a marker matrix.
[0095] Generating a marker matrix: the encryptor generates a marker matrix 3a composed of 0 and 1 according to the pixels involved in the content of the BMP image to be encrypted.
[0096]Steganographically embed the marking matrix into a color channel matrix 3b of the original image: the sender and the receiver agree in advance that the encryptor embeds the marking matrix into the lowest (last) plane of the image to obtain the marked image, that is, the image matrix 3c to be encrypted .
[0097] Such as Figure 4 and Figure 5 , to generate a mask matrix: the encryptor us...
Embodiment 2
[0106] Below with the 8*8 size color BMP image, choose N=4 as example, with the RGB three color channels of the BMP image, the encryptor encrypts the original image (same as embodiment one) as three images respectively, with one of them Taking the color channel as an example, the marking matrix is embedded into the seventh bit plane from high to low of the image to obtain the marked image, that is, the image matrix to be encrypted (such as Figure 7 ).
[0107] For the image pixel matrix to be encrypted from high to low, the five bit planes 1, 2, ..., 4, 7 are XORed with the mask matrix respectively, and the 5th, 6th, and 8th bits of the encrypted image pixel are The bits are the same as before encryption, and the encrypted image pixel matrix (such as Figure 8 ). Correspondingly, when extracting the marker matrix in the decryption step, the marker matrix is extracted from the seventh bit plane, that is, the fifth mask matrix is XORed with the bit plane embedded in the...
Embodiment 3
[0111] In this example, the marking matrix is saved independently and not embedded in the image, that is, the original image is not marked, and it does not form such image 3 The shown image to be encrypted 3c, in this embodiment, the image to be encrypted is the original image, directly for example image 3 The original image shown in 3b with Figure 5 The shown masking matrix is XORed to obtain an encrypted image, and after encryption, the marking matrix is sent to the decryptor separately. The decryptor does not need to extract the mark matrix, and directly uses the mark matrix and the secret key to generate such as Figure 4 The shown random matrix is operated to obtain the mask matrix, and the decrypted image can be obtained by XORing the first 4 mask matrices with the first 4 bit planes of the encrypted image. This final decrypted image is the original image. By saving the marking matrix independently, it can be guaranteed that the decrypted image is exactly t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com