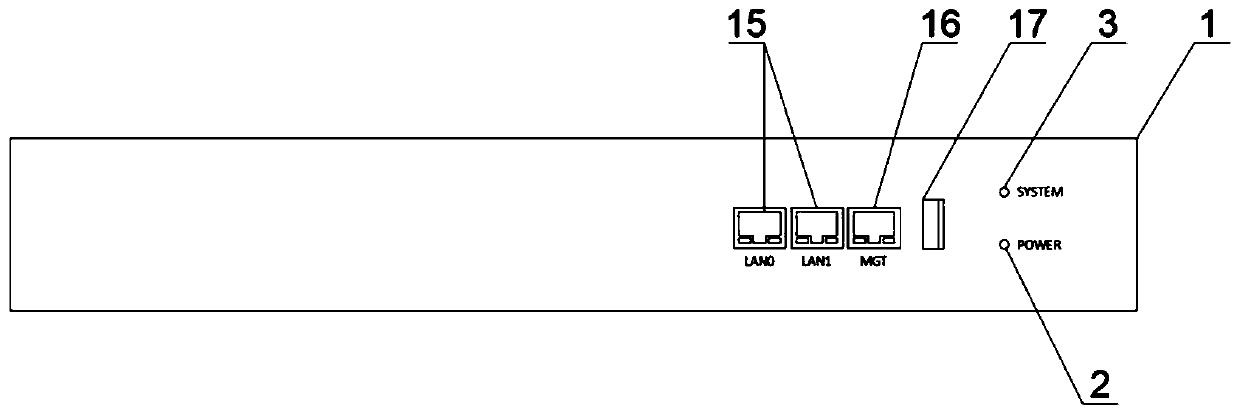
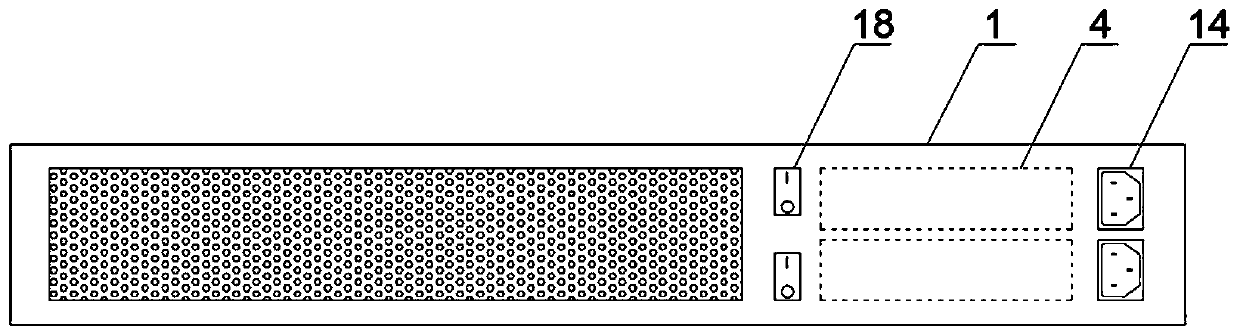
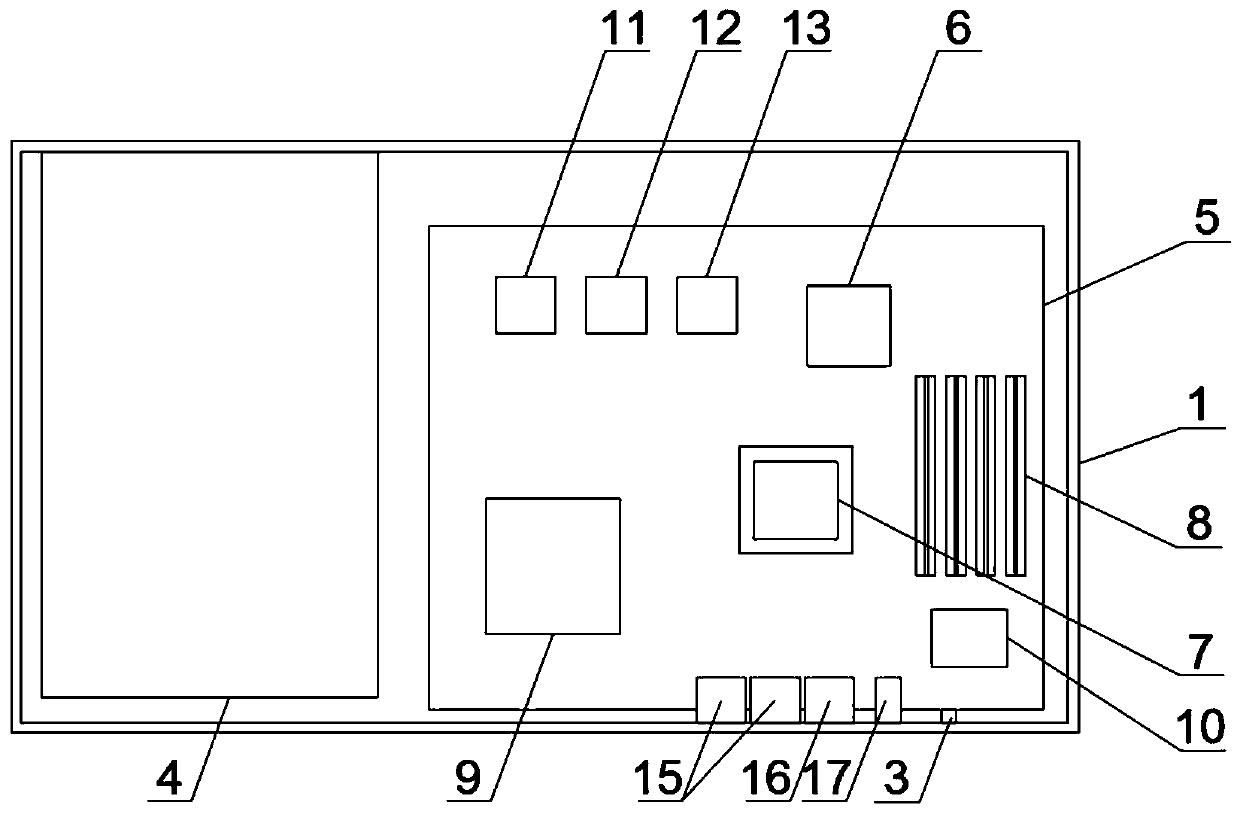
Intelligent autonomous linkage type WEB application protection host
An intelligent, autonomous and application-protective technology, applied in electrical components, transmission systems, etc., can solve the problems of lag in prevention and manual disposal, intrusion, etc., and achieve the effect of reducing losses and workload.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] An operating system official or a third-party security platform released the latest high-risk vulnerabilities. The key processes and services of this vulnerability are related to WEB applications. The general countermeasure is to download and install the corresponding patch after the corresponding patch is released. It is very likely that the vulnerability has been exploited by the attacker and the staff did not notice it. , has caused harm. After obtaining the latest vulnerability, the host analyzes the degree of correlation with the WEB application, that is, links with the disaster recovery equipment to back up key databases, webpage files, configuration files, log files, etc.
Embodiment 2
[0037] When a WEB application server is attacked by dDOS, the host will link the operating system to actively shut down unnecessary applications and service processes; related firewalls or routers will disable the ports of non-critical applications, etc., to reduce the attack surface and ensure the normal operation of the core main application with the maximum load capacity run.
Embodiment 3
[0039] The process of SQL injection attack is that once the scanning program finds the possibility of injection, the attack program will start, while passive defense and manual handling are relatively lagging behind. The host will regularly conduct tentative attacks on stock webpage files. Once found, it can be injected , that is, the linkage operating system restricts the page file from being accessed, alarms, and records logs, especially after the operating system global file system write operation is completed, the "black box test" is performed on the newly added page file. If the test fails, the page is restricted file access permissions.
[0040]Principle of use: The host hardware platform is based on the X86 structure. On the basis of the ordinary PC computer motherboard, the original CMOS chip is replaced with a burnable CMOS chip, and the necessary network card interface and auxiliary chip are added. The main idea of the software platform is anthropomorphic Persona...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com