User data security protection method in Kubernetes environment
A user data and security protection technology, applied in the field of data security, can solve problems such as inability to guarantee call requests, inability to verify the real identity of users, and inability to verify whether scheduling requests come from trusted users, etc., to achieve the effect of ensuring security and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to make the purpose, content, and advantages of the present invention clearer, the specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
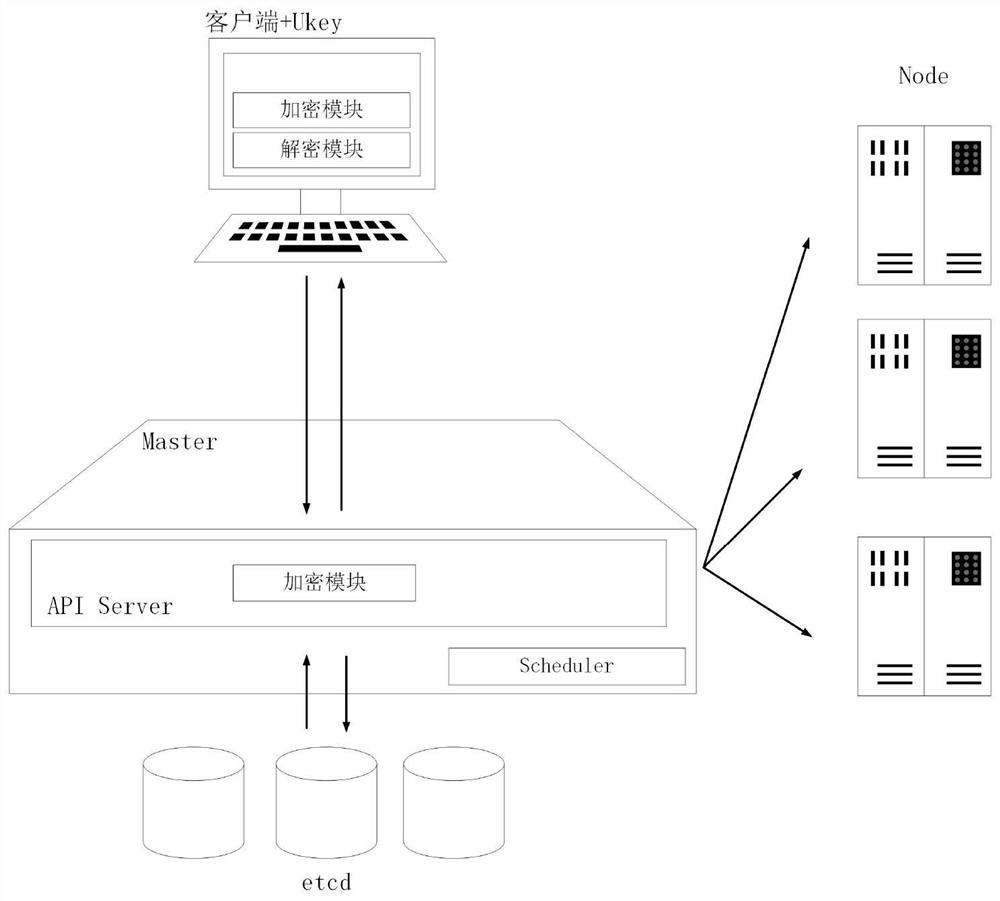
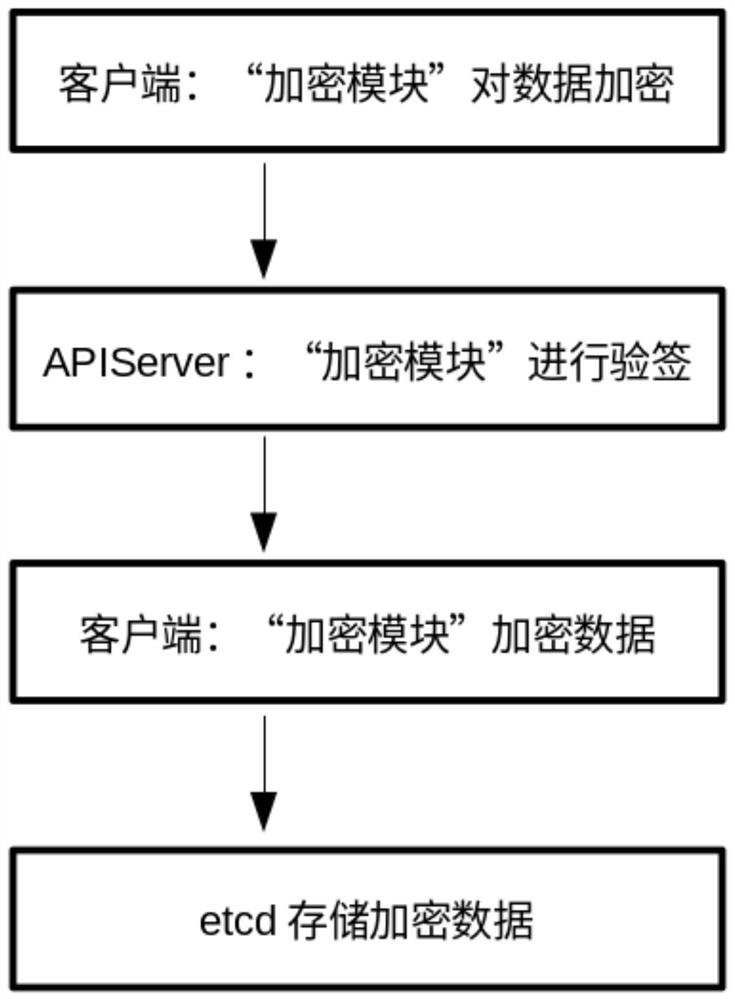
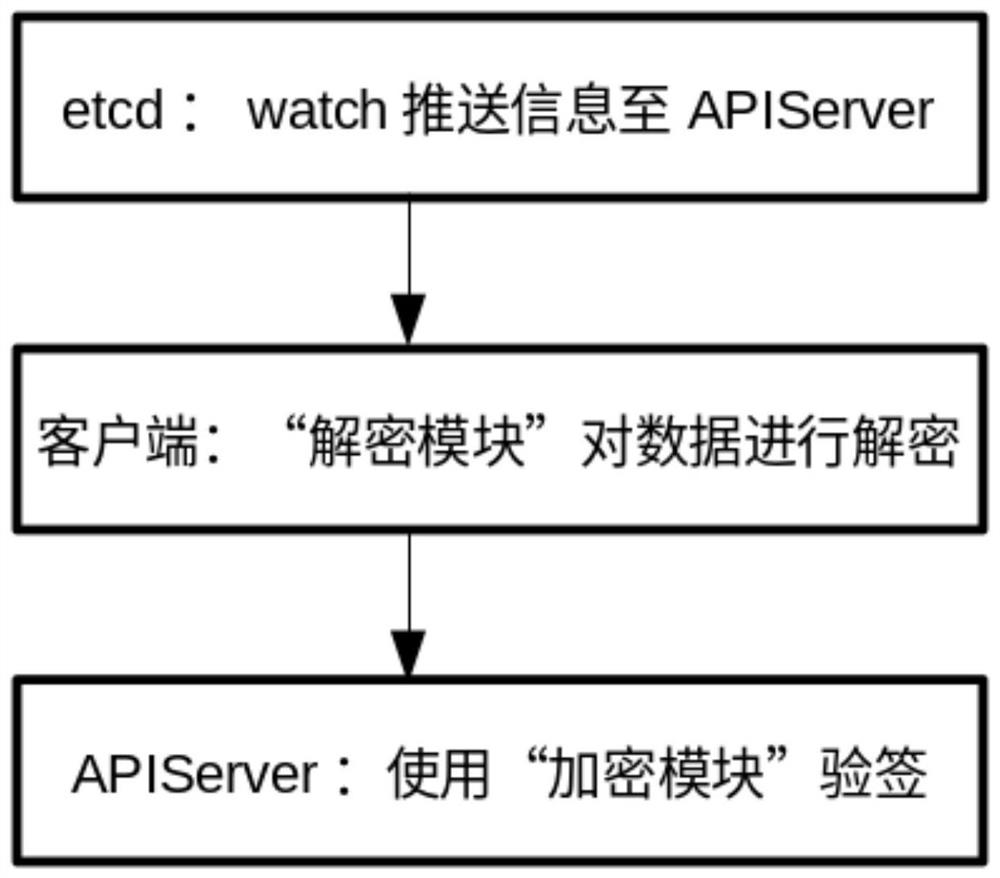
[0021] figure 1 Shown is the system block diagram of the present invention, as figure 1 As shown, the present invention introduces Ukey to authenticate user requests, and securely manages the data stored in Kubernetes etcd through the public-private key system, so as to ensure the security of data transmission and access, and realize "one account, one secret" under the Kubernetes environment. ” user access mechanism.
[0022] Kubernetes is divided into two parts, the Master cluster control node and the Node node, and the Kubernetes security component of the present invention is defined as follows:
[0023] 1) etcd: saves the state of the entire cluster and is responsible for storing the encrypted information of the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com