Device and method for implementing mimic brackets in distributed mode
A distributed, bracketed technology, applied in the field of network security, can solve problems such as lack of mimetic bracket design, and achieve the effect of avoiding homogeneous loopholes, simplifying functions, and reducing risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
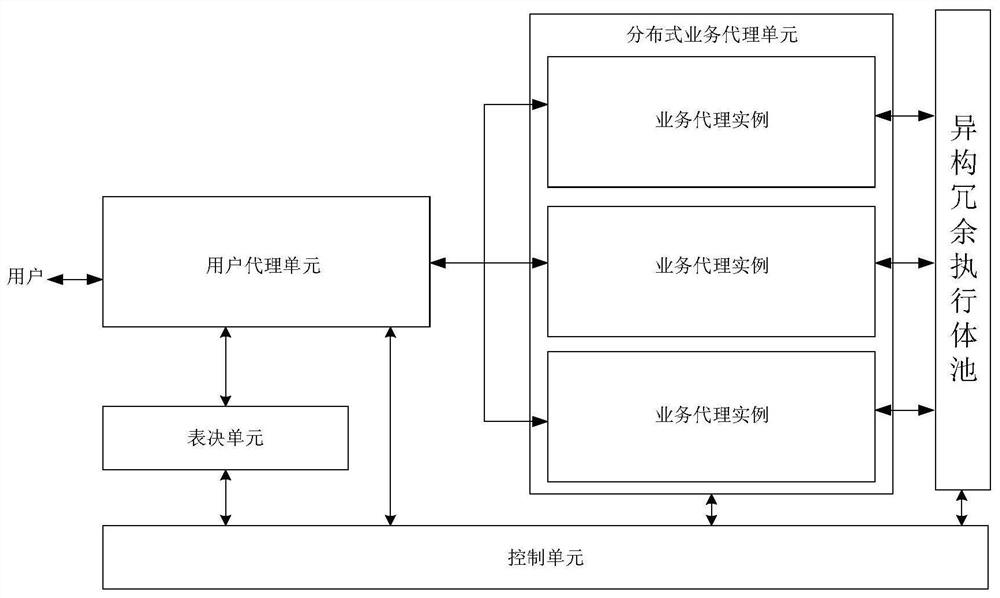
[0038] like figure 1 As shown, a distributed mode mimic bracket implementation device includes a user agent unit, a distributed business agent unit, a voting unit, a heterogeneous redundant executive pool and a control unit;
[0039] The user proxy unit is used to receive user requests, add labels and control information to the user requests, and distribute user requests to the distributed service proxy unit; it is also used to receive and parse the response message returned by the distributed service proxy unit, and send to the voting unit; it is also used to parse the voting result of the voting unit and send it to the user; specifically, the control information includes but is not limited to (1) user IP: after passing through the user proxy unit, the distributed service proxy unit cannot directly obtain The IP address of the client, the voting unit finds it difficult to find the attacker's IP; (2) Packet scrambling: For example, encrypting part of the content will cause con...
Embodiment 2
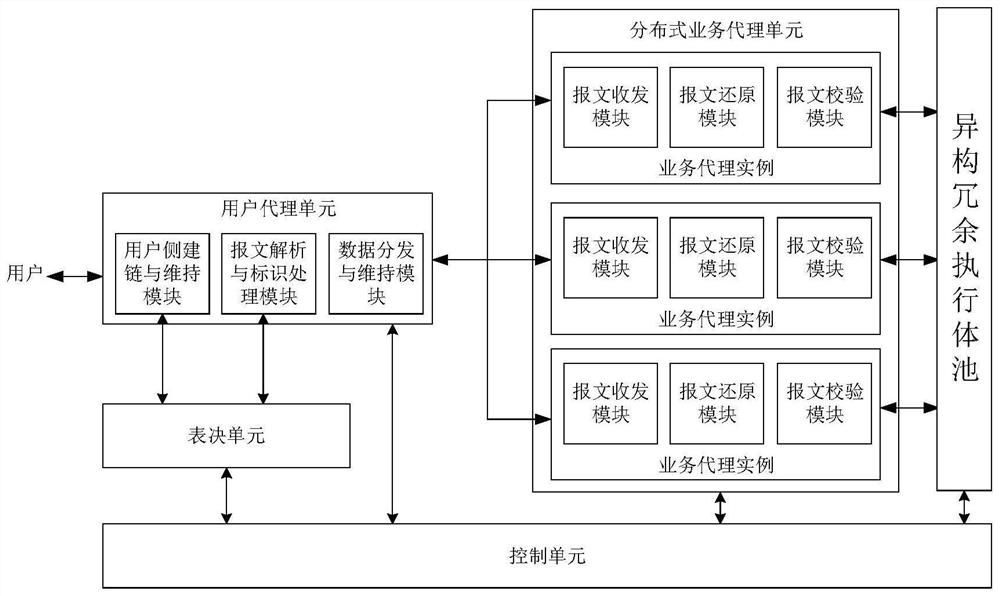
[0045] On the basis of Example 1, as figure 2 As shown in the figure, the present invention also discloses a device for realizing the mimetic brackets in a distributed mode, and the difference from Embodiment 1 is:
[0046] Further, the user agent unit includes a user-side chain building and maintenance module, a message parsing and identification processing module, and a data distribution and maintenance module;
[0047] The user side chain establishment and maintenance module is used for establishing and maintaining a communication link with the user end;
[0048] The message parsing and identification processing module is used to parse the message sent by the user, add labels and control information to the user request, and parse the verification information returned by the distributed service proxy unit;
[0049] The data distribution and maintenance module is used to distribute and maintain the data sent by the user, and is also used to receive the response message return...
Embodiment 3
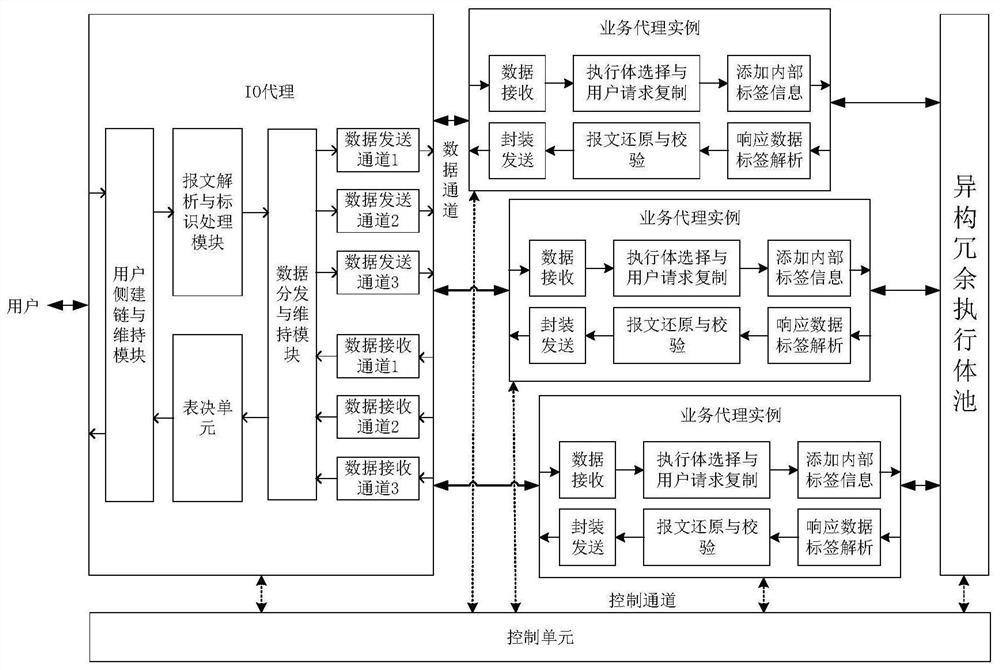
[0055] On the basis of Example 2, as image 3 As shown, the present invention also discloses a distributed mode mimic bracket implementation device, and the difference from Embodiment 2 is:
[0056] Further, both the user agent unit and the voting unit are located on the IO agent; the IO agent further includes a plurality of data sending channels and data receiving channels.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com