A method and device for encrypting and decrypting electronic bills based on related parties
A technology of electronic bills and encryption methods, which is applied in the direction of secure communication devices, computer security devices, and electronic digital data processing, can solve the problems of large redundancy, difficult maintenance of database tables, and low efficiency, so as to reduce redundancy, The effect of ensuring security and improving encryption speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
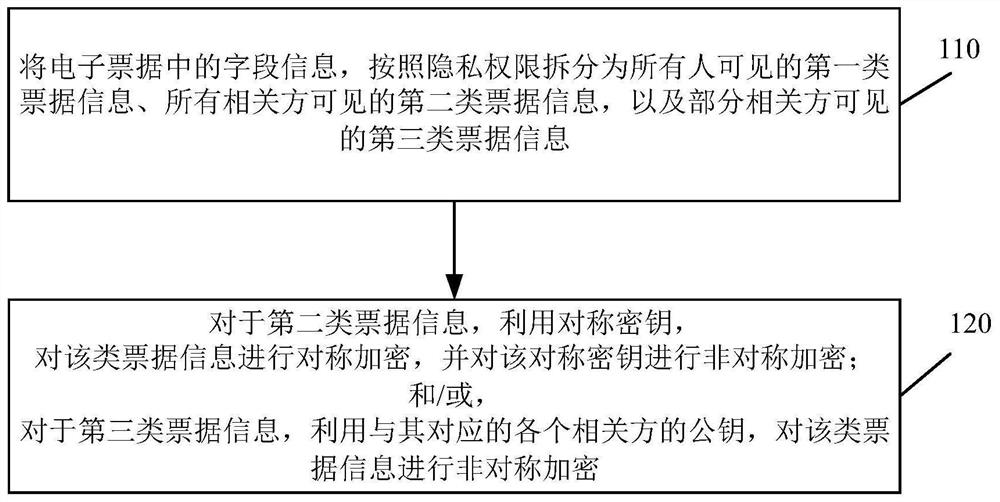
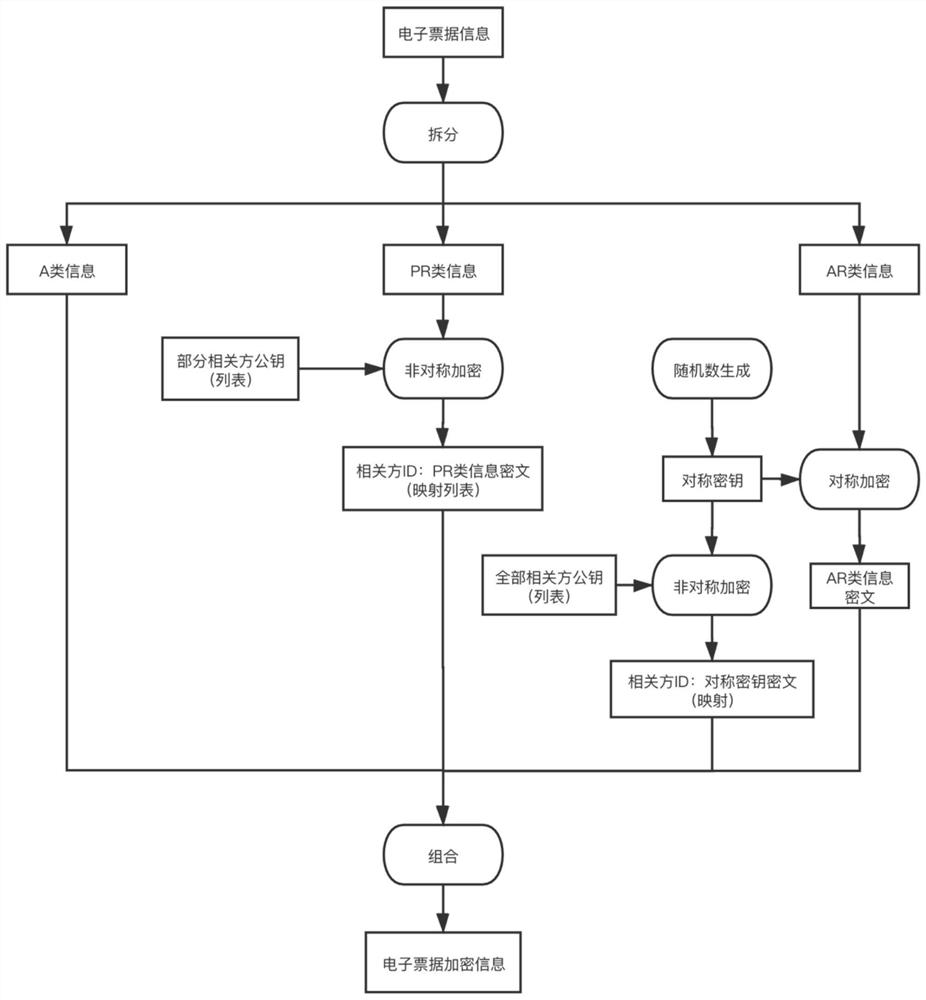
[0071] see figure 1 , figure 1 It is a schematic flowchart of a method for encrypting an electronic note based on a related party provided by an embodiment of the present invention. The authority control terminal applied to the electronic note can be executed by an encryption device based on the related party's electronic note, which can be realized by software and / or hardware, which is not limited in the embodiment of the present invention. Such as figure 1 As shown, the encryption method of the electronic bill provided in this embodiment specifically includes:
[0072] 110. Split the field information in the electronic bill into the first type of bill information visible to all, the second type of bill information visible to all related parties, and the third type of bill information visible to some related parties according to privacy rights.
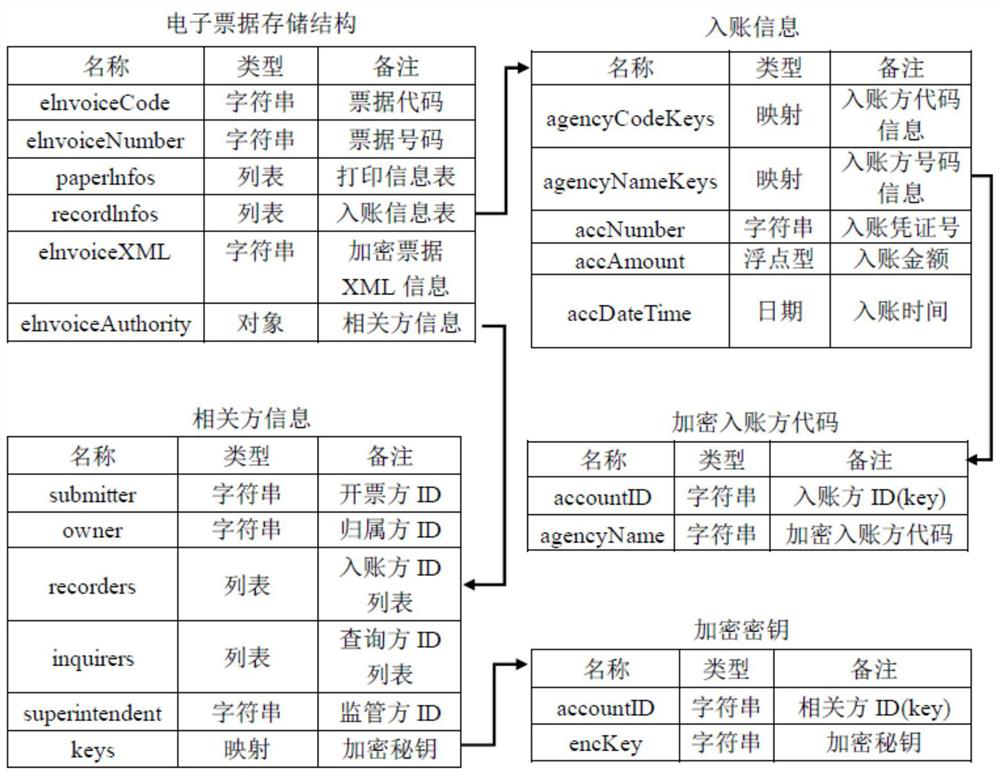
[0073] Among them, the life cycle of electronic bills includes invoicing, printing, downloading, reimbursement application, and ...
Embodiment 2
[0096] see Figure 4 , Figure 4 It is a schematic flowchart of a method for decrypting an electronic note based on a related party provided by an embodiment of the present invention. The decryption method provided in this embodiment corresponds to the related party-based encryption method provided in the above-mentioned embodiments, and can be applied to the authority access terminal of the electronic note corresponding to the related party (also called the querying party). Such as Figure 4 As shown, the method includes:
[0097] 210. Split the encrypted electronic bill information to obtain the first type of bill information visible to everyone and the encrypted bill ciphertext of the bill information.
[0098] 220. For any related party, if the related party corresponds to the second type of note information visible to all related parties, determine the corresponding symmetric key ciphertext according to the identity of the related party, and use the related party's pri...
Embodiment 3
[0107] see Figure 7 , Figure 7 It is a schematic structural diagram of an encryption device for an electronic note based on a related party provided by an embodiment of the present invention. The device can be applied to the weight control terminal of bills. Such as Figure 7 As shown, the device includes: a field splitting module 310, a symmetric encryption module 320, and / or an asymmetric encryption module 330; wherein,
[0108] The field splitting module 310 is configured to: split the field information in the electronic note into first-type note information visible to all, second-type note information visible to all related parties, and partly visible to related parties according to privacy rights. The third type of bill information, wherein the relevant parties include the payer, the billing unit and the reimbursement unit;
[0109] The symmetric encryption module 320 is configured to perform symmetric encryption on the second type of note information by using a sym...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com