A virtual desktop licensing method based on the combination of software and hardware
A virtual desktop, software and hardware technology, applied in the field of virtual desktop authorization, can solve the problems of hardware replication, inability to modify, loss, etc., to simplify the deployment process, improve security strength, and prevent reverse cracking.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be further described below in conjunction with the accompanying drawings and specific preferred embodiments, but the protection scope of the present invention is not limited thereby.
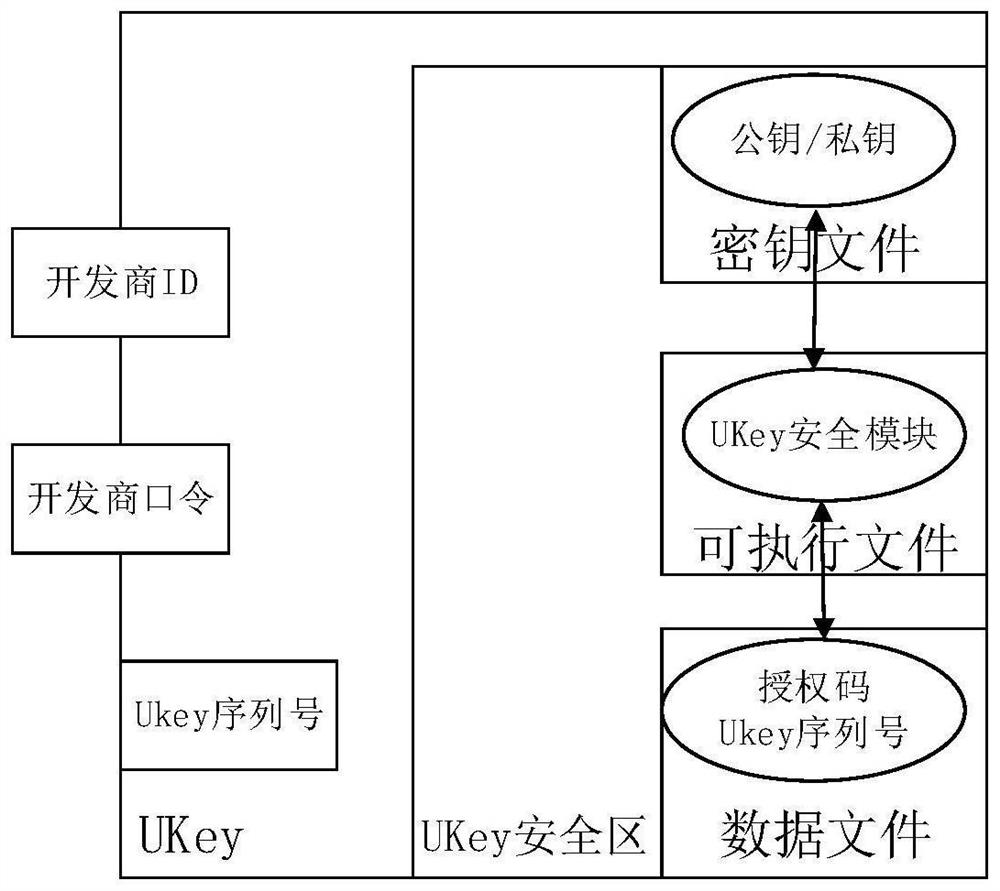
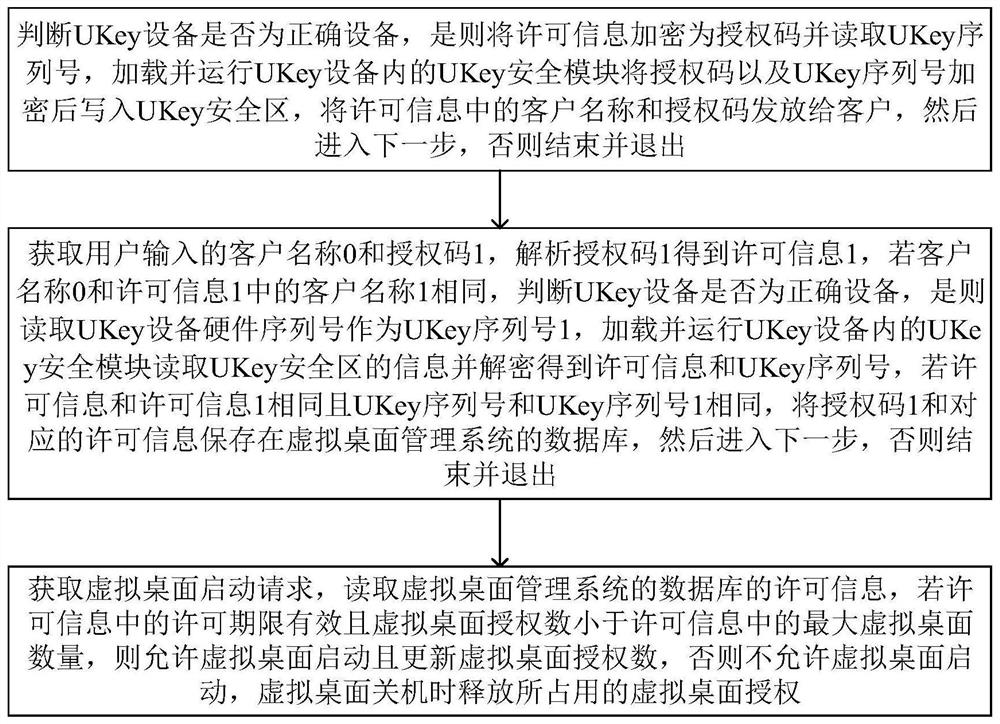
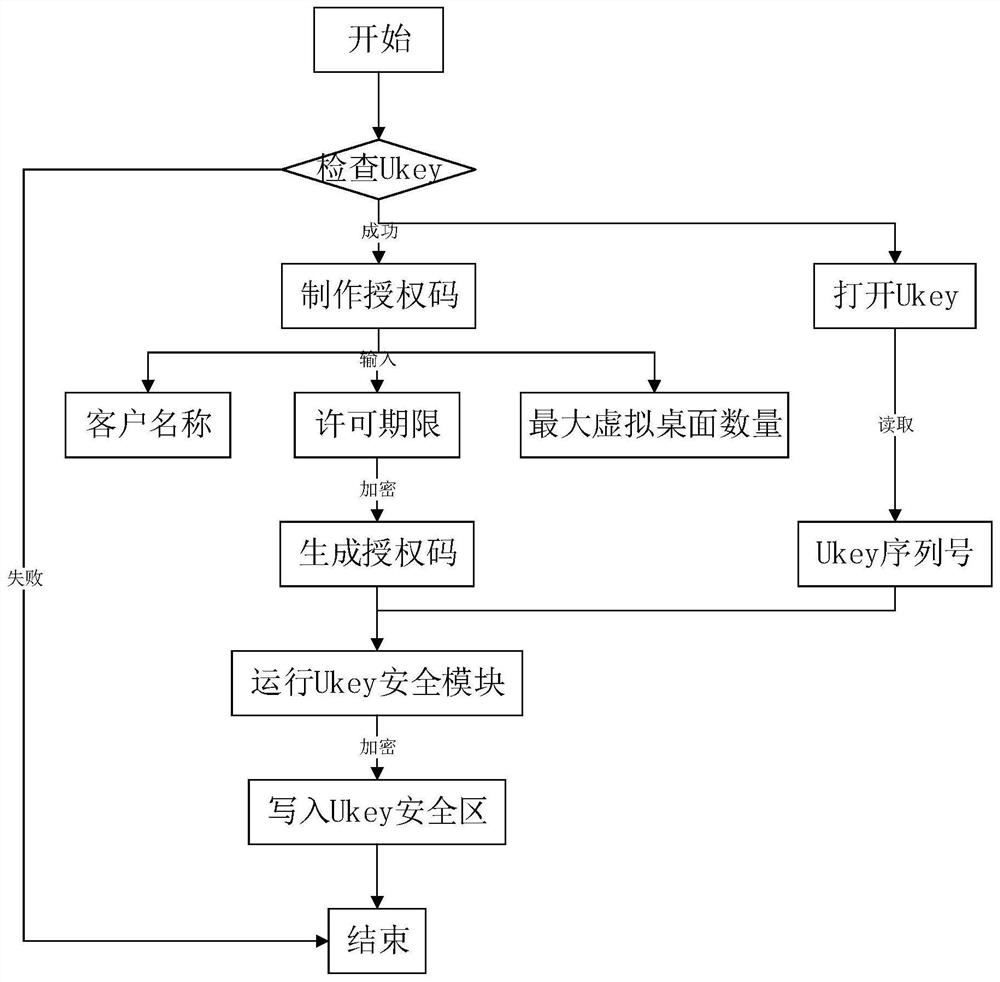
[0049] Such as figure 1 As shown, the present invention performs secondary development on UKey equipment, and configures a UKey security module in the UKey equipment, so that the authorization code and UKey serial number are encrypted by the UKey security module to obtain the key file, and the key file is decrypted by the UKey security module to obtain the corresponding key file. The license information and UKey serial number. The UKey security module is a security component that encapsulates the core encryption and decryption algorithm and code into a C51 program, generates a binary file after compilation, and runs inside the UKey. When initializing each new UKey device, the developer ID and developer password will be automatically set, and the UKey security mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com