5G network slice-based power Internet-of-Things security management method and system
A power Internet of Things and network slicing technology, applied in the field of power Internet of Things network security, can solve problems such as power system paralysis, power outages, tampering with configuration parameters, etc., and achieve the effect of safe and reliable authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] The main application scenario of the present invention is distribution automation. The distribution automation terminal equipment is based on computer science and communication engineering technology. The entire distribution network is monitored to isolate faults in time, and at the same time, the terminal equipment that controls the distribution network can timely check the faults in the distribution network and optimize the allocation of resources in the distribution network, so that the power grid benefit to the highest.
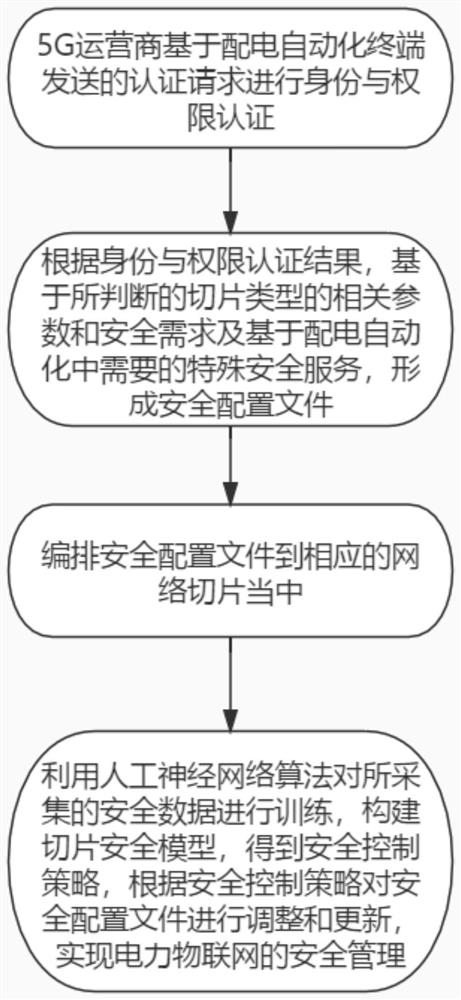
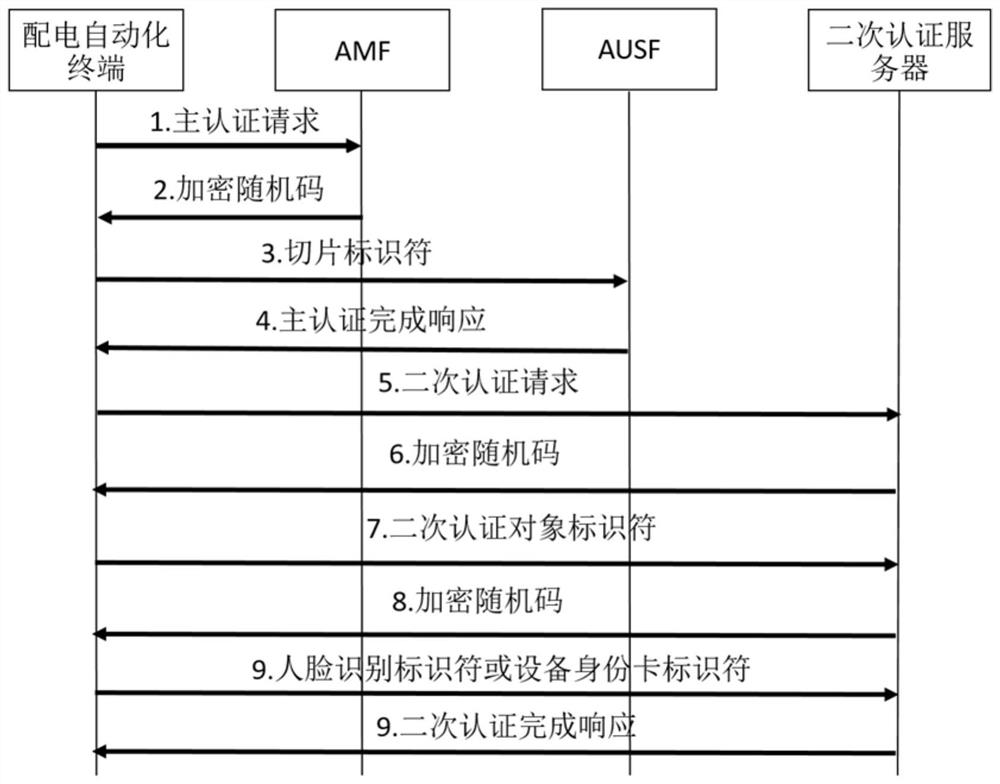
[0035] refer to Figure 1~2 , which is the first embodiment of the present invention, this embodiment provides a 5G network slicing-based power Internet of Things security management method, including:
[0036] S1: 5G operators perform identity and authority authentication based on the authentication request sent by the distribution automation terminal.
[0037] It should be noted that: distribution automation terminals include:
[0038] Based o...
Embodiment 2
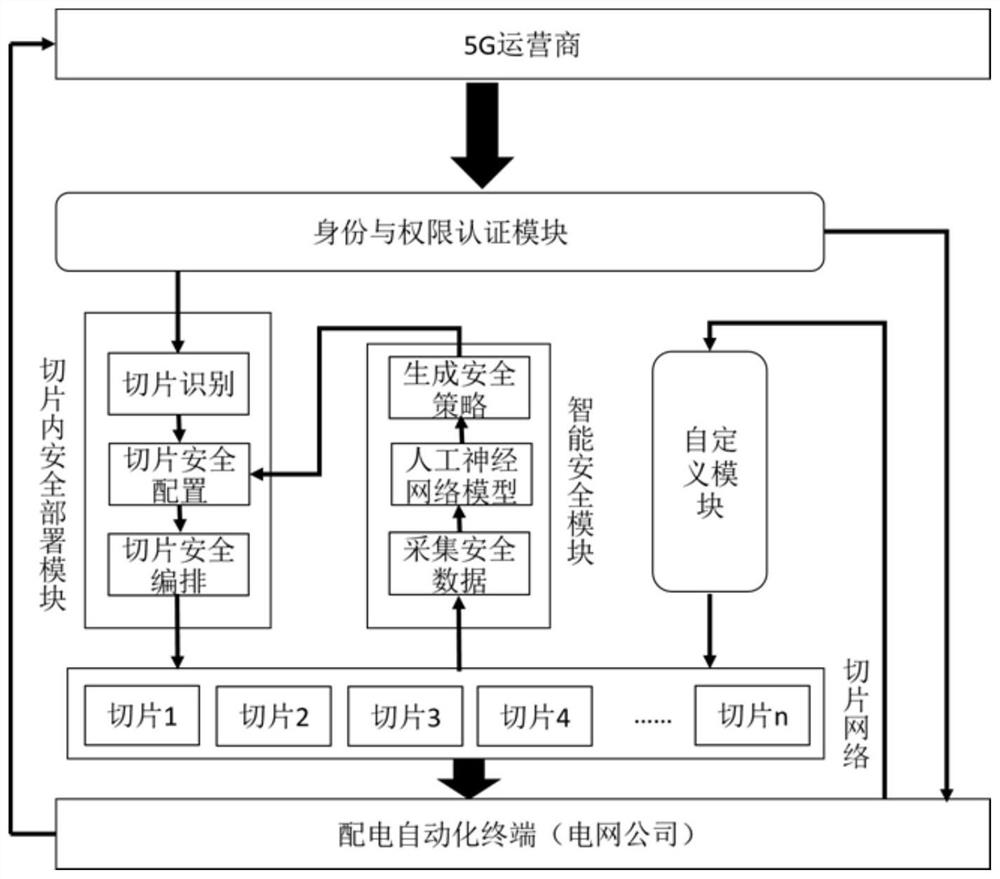
[0059] In the original network slicing security management system, the present invention introduces intelligent security and custom development to make the identification of security threats more intelligent in the security protection of the slicing network, allowing power grid companies to have more independent development rights for specific security services, and at the same time Make the network slicing security management system more in line with the reality of distribution automation.
[0060] refer to Figure 3-4 , which is the second embodiment of the present invention. This embodiment is different from the first embodiment in that it provides a 5G network slicing-based power Internet of Things security management system, including: an identity and authority authentication module, an in-slice For security deployment modules, custom modules, and intelligent security modules, what needs to be explained is:
[0061] The identity and authority authentication module is use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com