Patents
Literature
59results about How to "Intelligent recognition" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
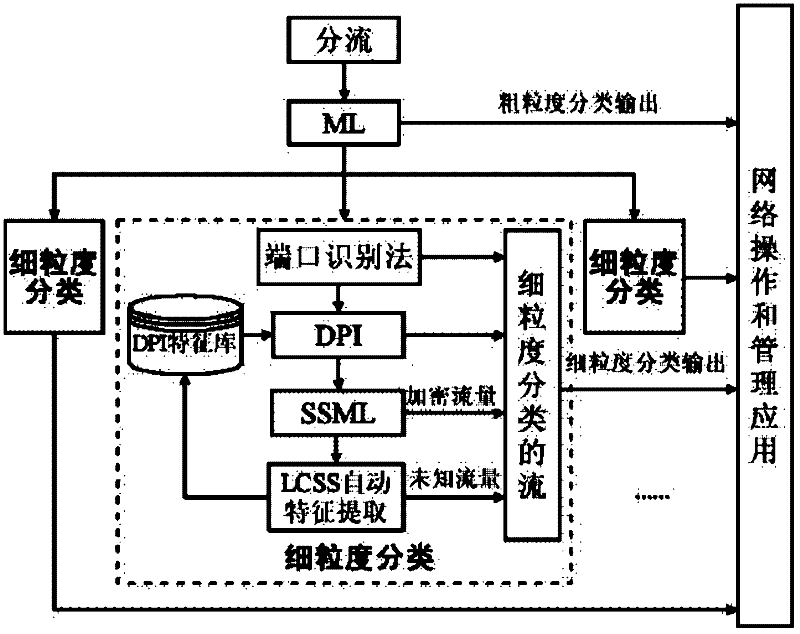
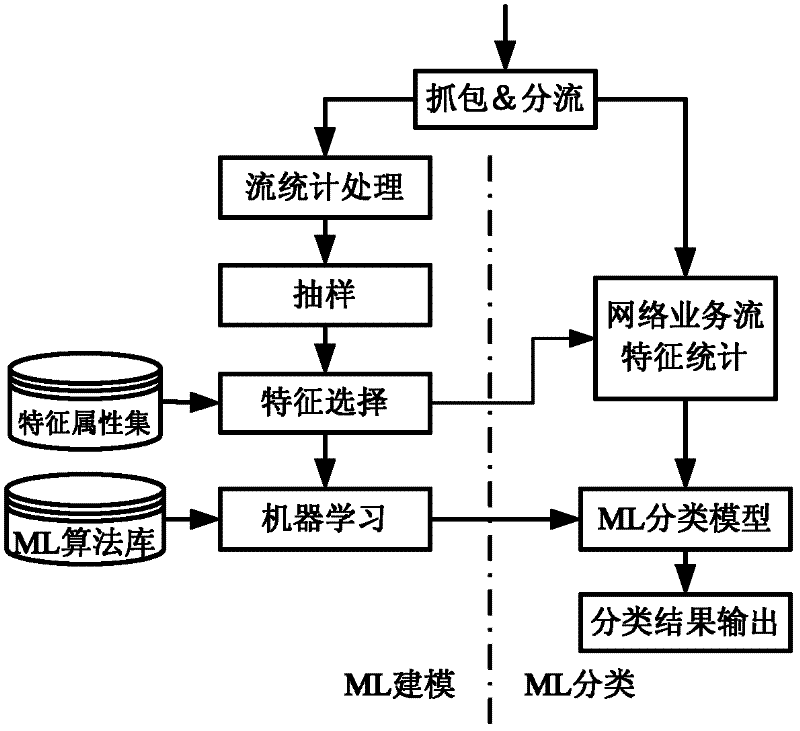
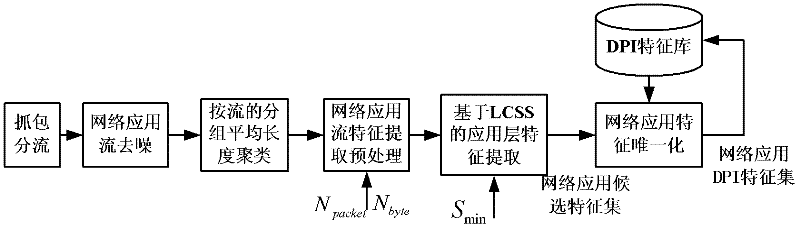
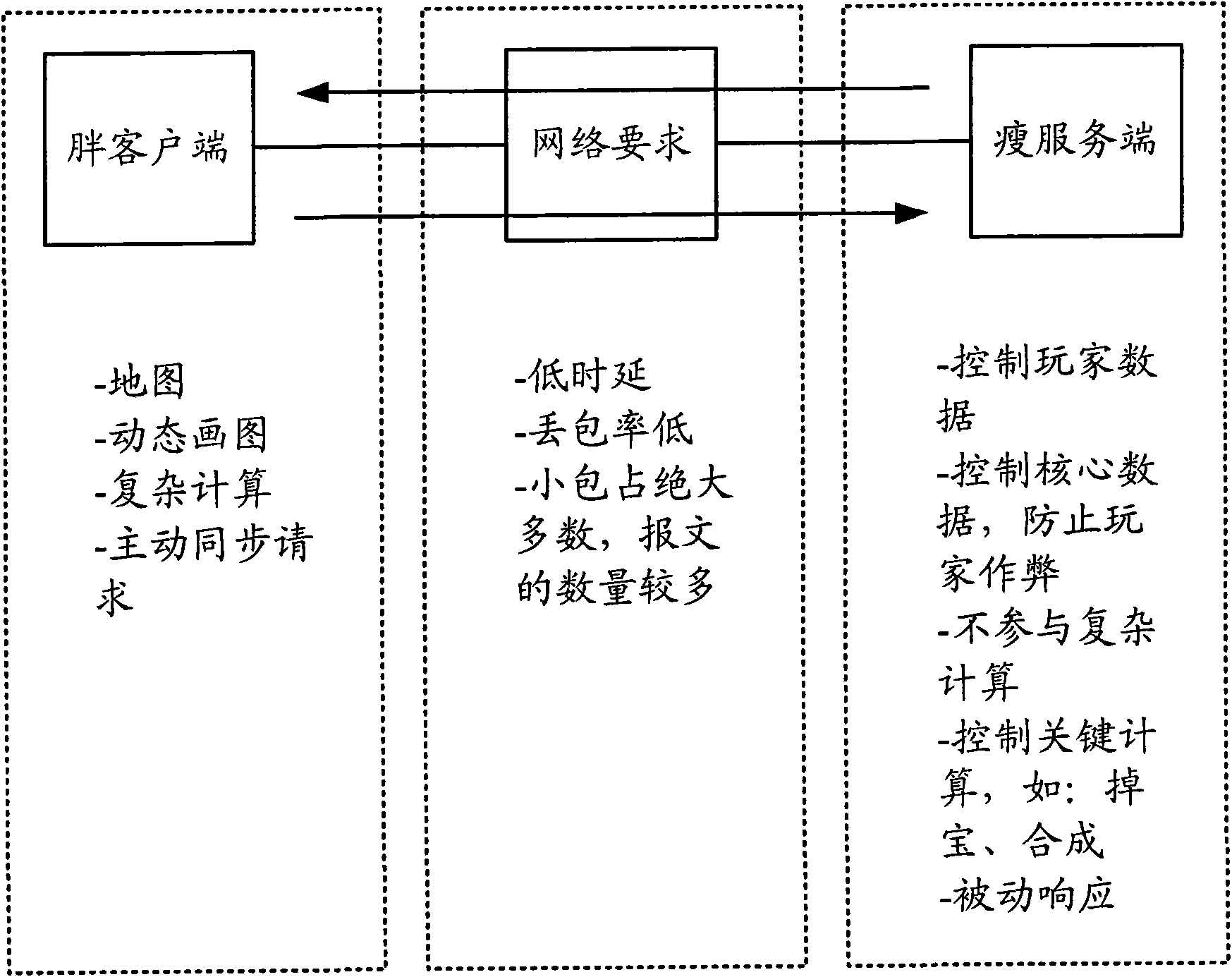
Hierarchical classification method for internet flow
InactiveCN102394827AImprove classification performanceAccurate identification and processingData switching networksTraffic volumeInternet traffic classification
The invention relates to a hierarchical classification method for internet flow, comprising the following steps: firstly, coarse grained classification is conducted as follows: a flow statistical property method based on machine learning is adopted for quickly classifying network flow, the network flow is divided into applied categories with different characteristics, if the flow distinguished by the coarse grained classification needs to be used, the flow can be output directly, and if the flow needs further classification, next step is conducted; and secondly, fine grained classification is conducted as follows: classification is further conducted on the applied categories distinguished by the coarse grained classification, the network flow can be intelligently, accurately and effectively identified in real time, good integrity and expandability are realized, and the requirements on the internet flow classification with different application targets and classification grain size can be met.
Owner:ZHEJIANG WANLI UNIV
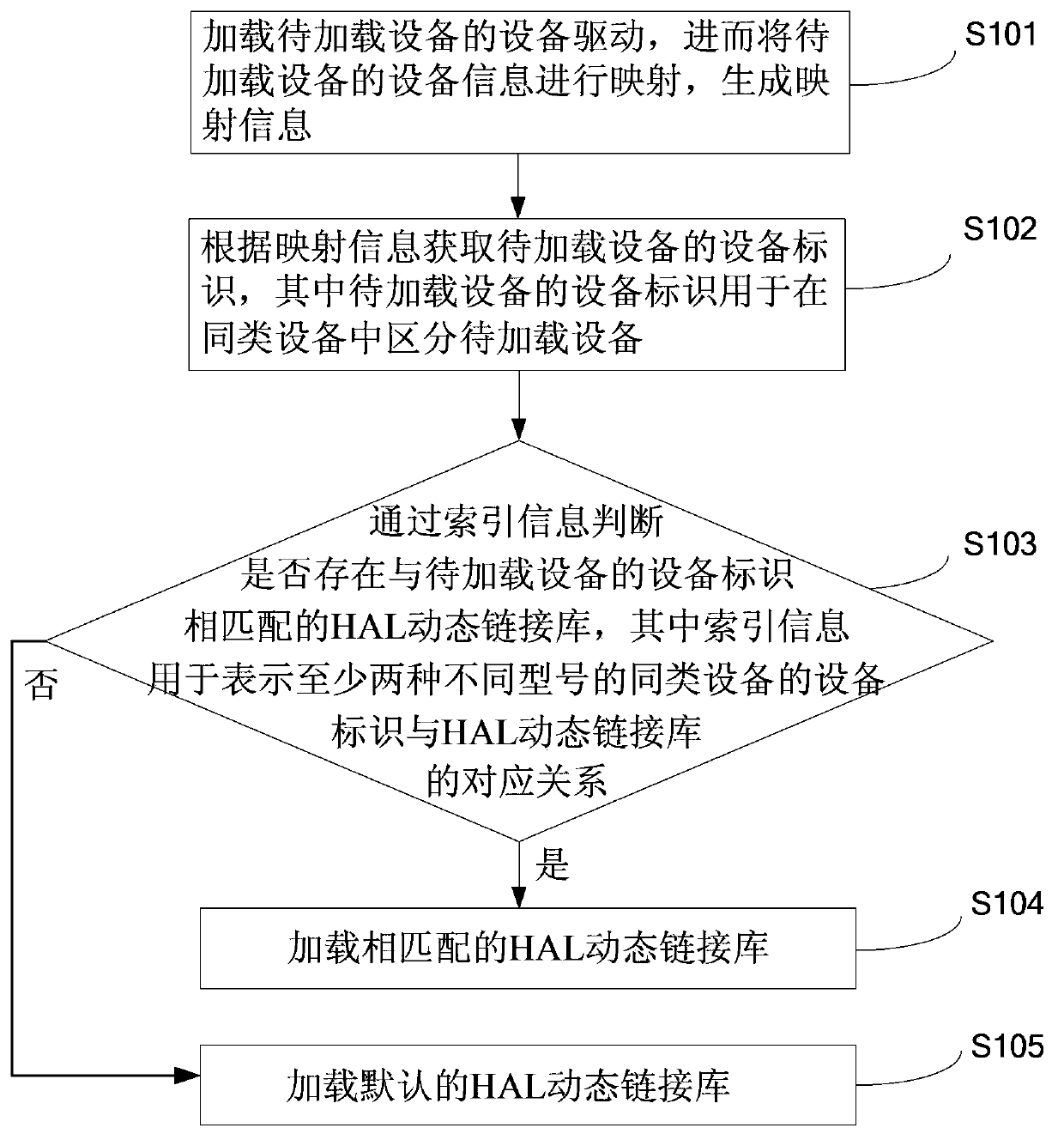
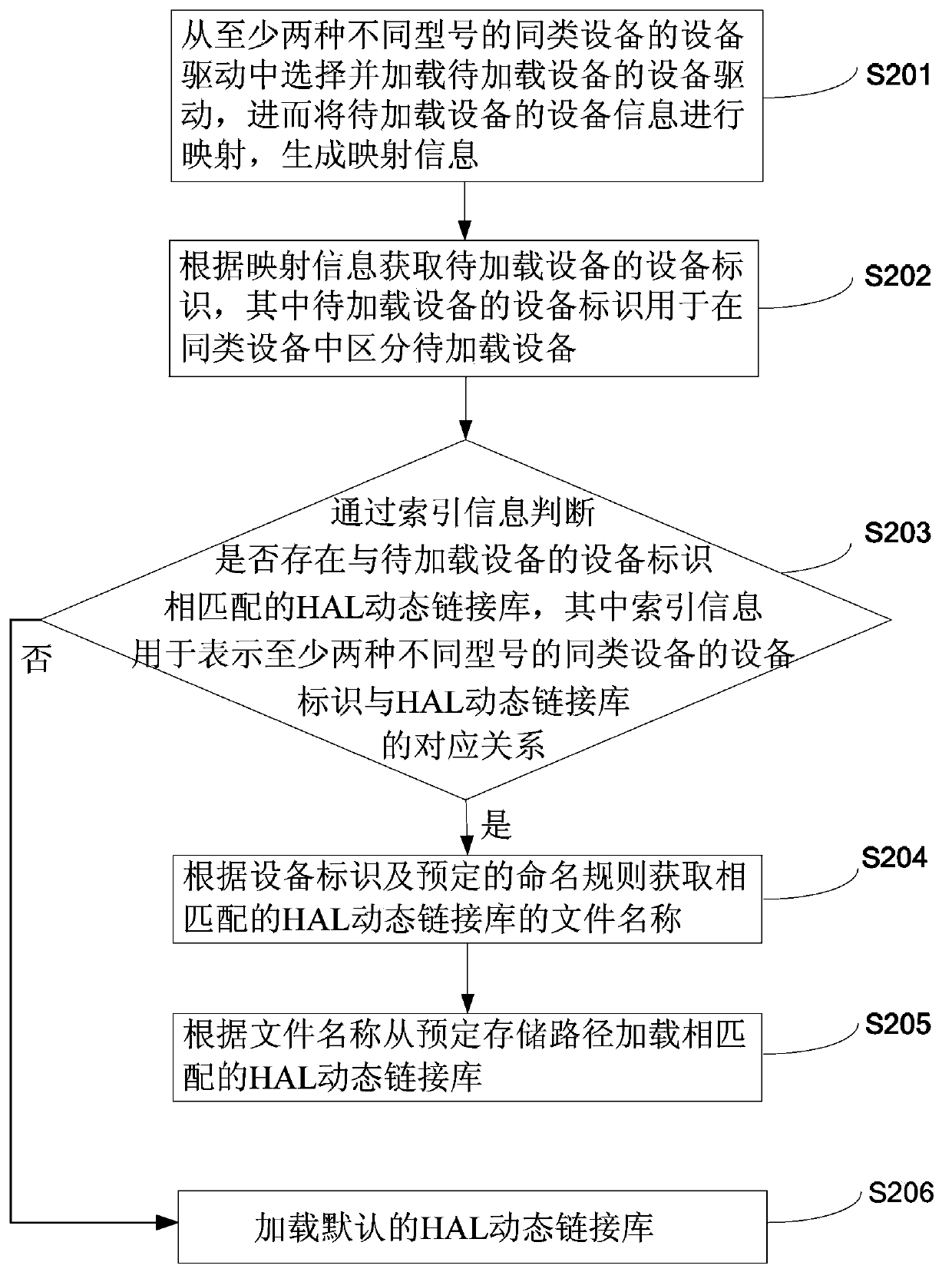
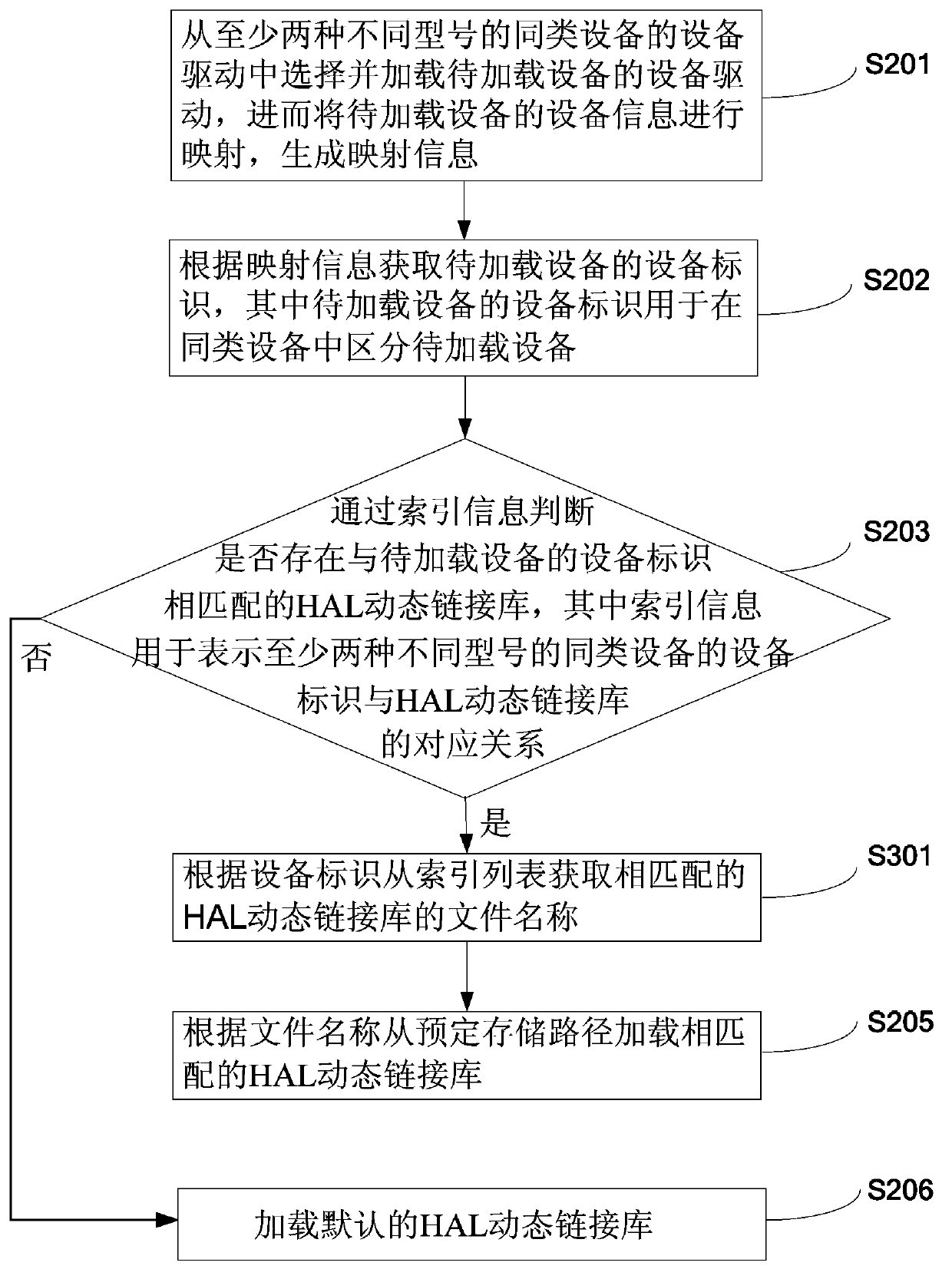
Device loading method and device on basis of Android
ActiveCN103970559AIntelligent RecognitionEasy to useProgram loading/initiatingModel NumberComputer science
The invention discloses a device loading method and device on the basis of Android. The device loading method includes steps of loading device drives of devices to be loaded, mapping device information of the devices to be loaded and generating mapping information; acquiring device identifications of the devices to be loaded according to the mapping information; judging whether an HAL (hardware abstraction layer) dynamic link library matched with the device identifications of the devices to be loaded exists or not according to the index information, if yes, loading the matched HAL dynamic link library, and if not, loading a default HAL dynamic link library, wherein the index information is used for indicting corresponding relation of the device identifications of at least two different specifications of the devices of the same kind and the HAL dynamic link library. According to the above technical scheme, the same-kind devices of different specifications can be intelligently identified in the Android system, corresponding device drives and HAL dynamic link libraries can be dynamically loaded, and the devices can operate normally.
Owner:BEIJING ERENEBEN INFORMATION TECH
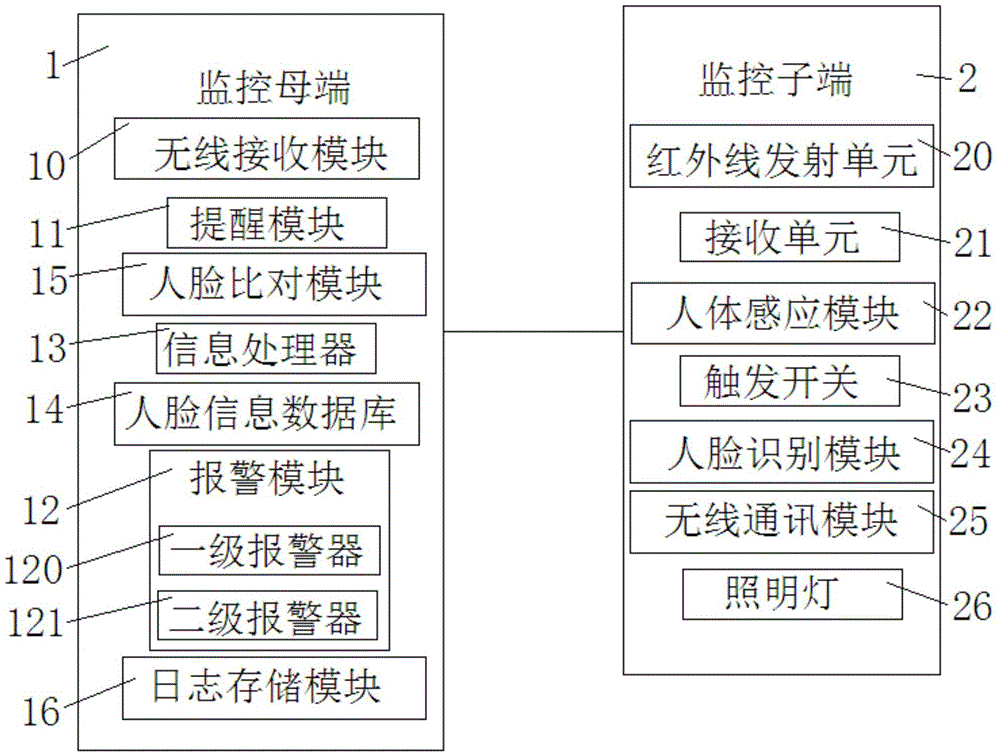
Anti-intrusion system for campus
InactiveCN105659300AAvoid high-intensity workImprove securityBurglar alarm electric actuationInfraredComputer module
The invention relates to an anti-intrusion system for a campus. The system comprises a monitor mother terminal and a monitor son terminal. The monitor son terminal comprises multiple infrared emission units which are arranged on campus walls, receiving units which are matched with the infrared emission units one-for-one, and human body sensing modules. The monitor son terminal also comprises a trigger switch, a face recognition module, and a wireless communication module; the monitor mother terminal comprises a wireless receiving module, a prompting module, an alarming module, an information processing module, a face information database and a face comparison module; when there is somebody climbs over the campus walls, the person is sensed by the human body sensing module, and a prompt message is sent to the monitor mother terminal by use of the trigger switch. The system has high safety and high intensity work load of monitoring personnel is avoided. By arrangement of the face recognition module, when the face information of the intrusion person does not match with the data in the face information database or matches with ministry of public security wanted person information in the face information database, alarm is given off through the alarm module so that the recognition of intrusion person is more intelligent.
Owner:汤美
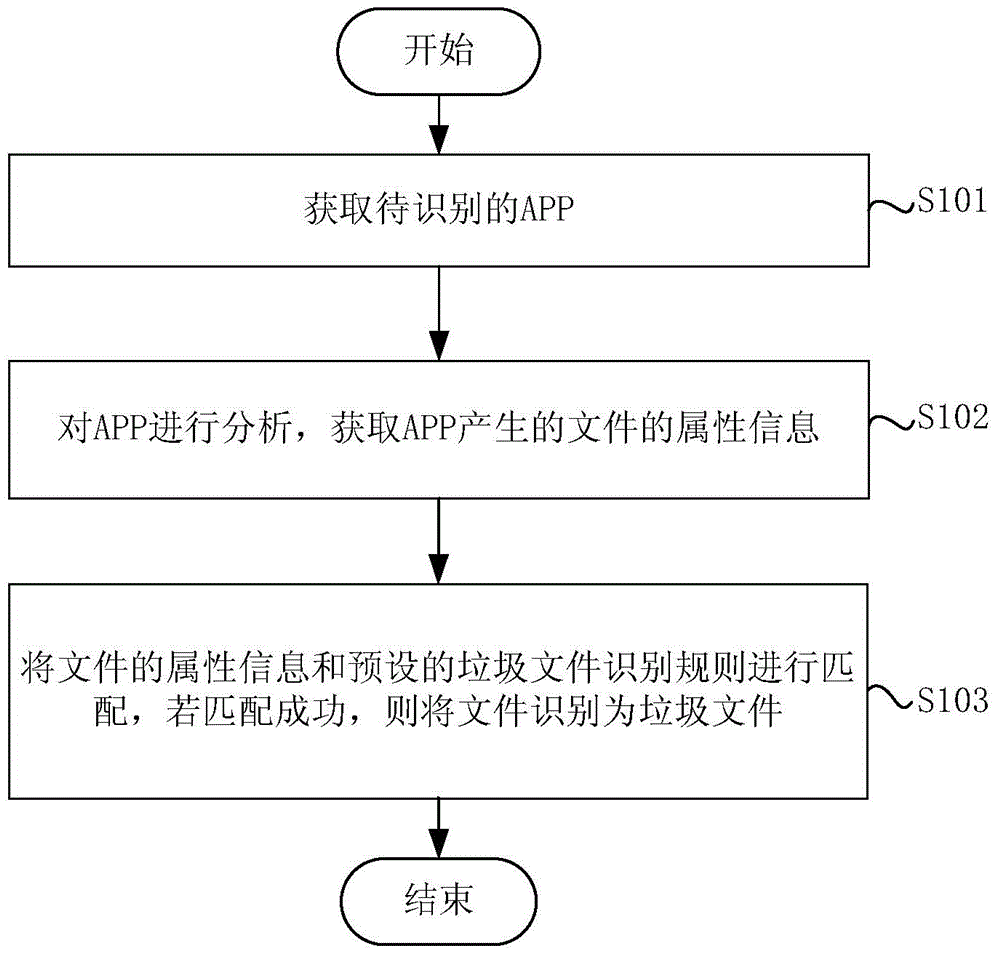
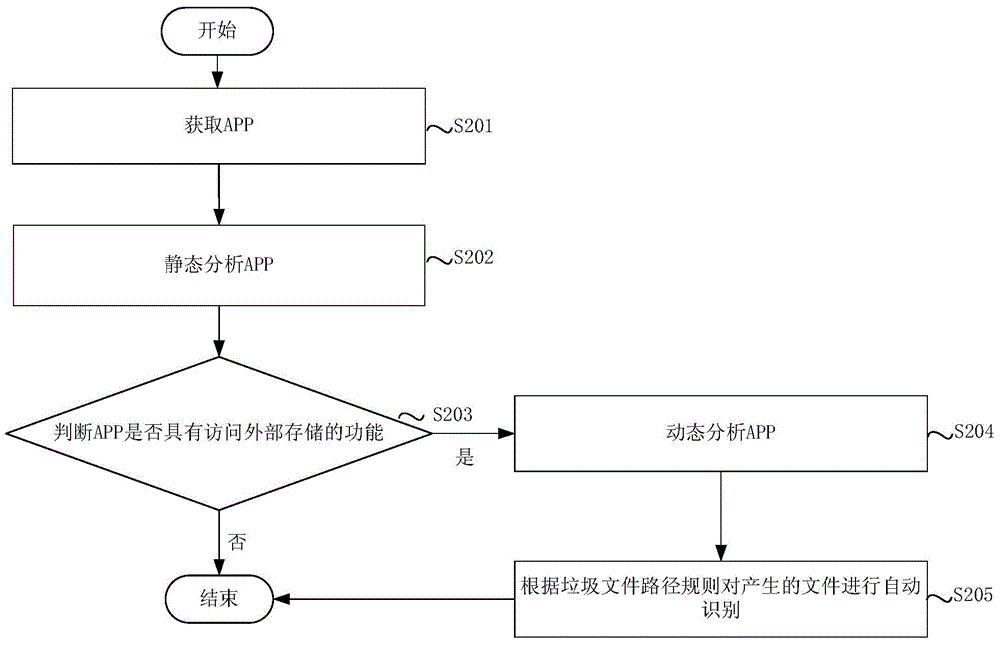
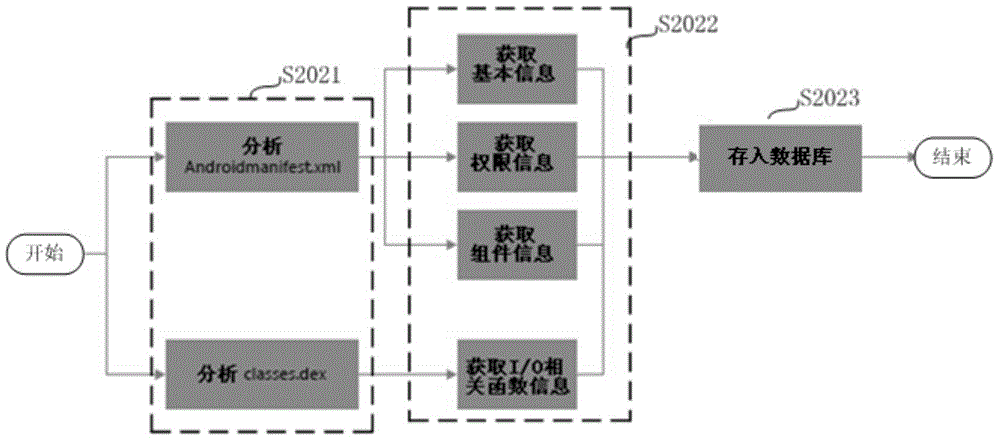
Automatic garbage file identification method and apparatus
ActiveCN105224574AQuick identificationLow costDesign optimisation/simulationPlatform integrity maintainanceDocument IdentifierDatabase
Owner:KINGSOFT
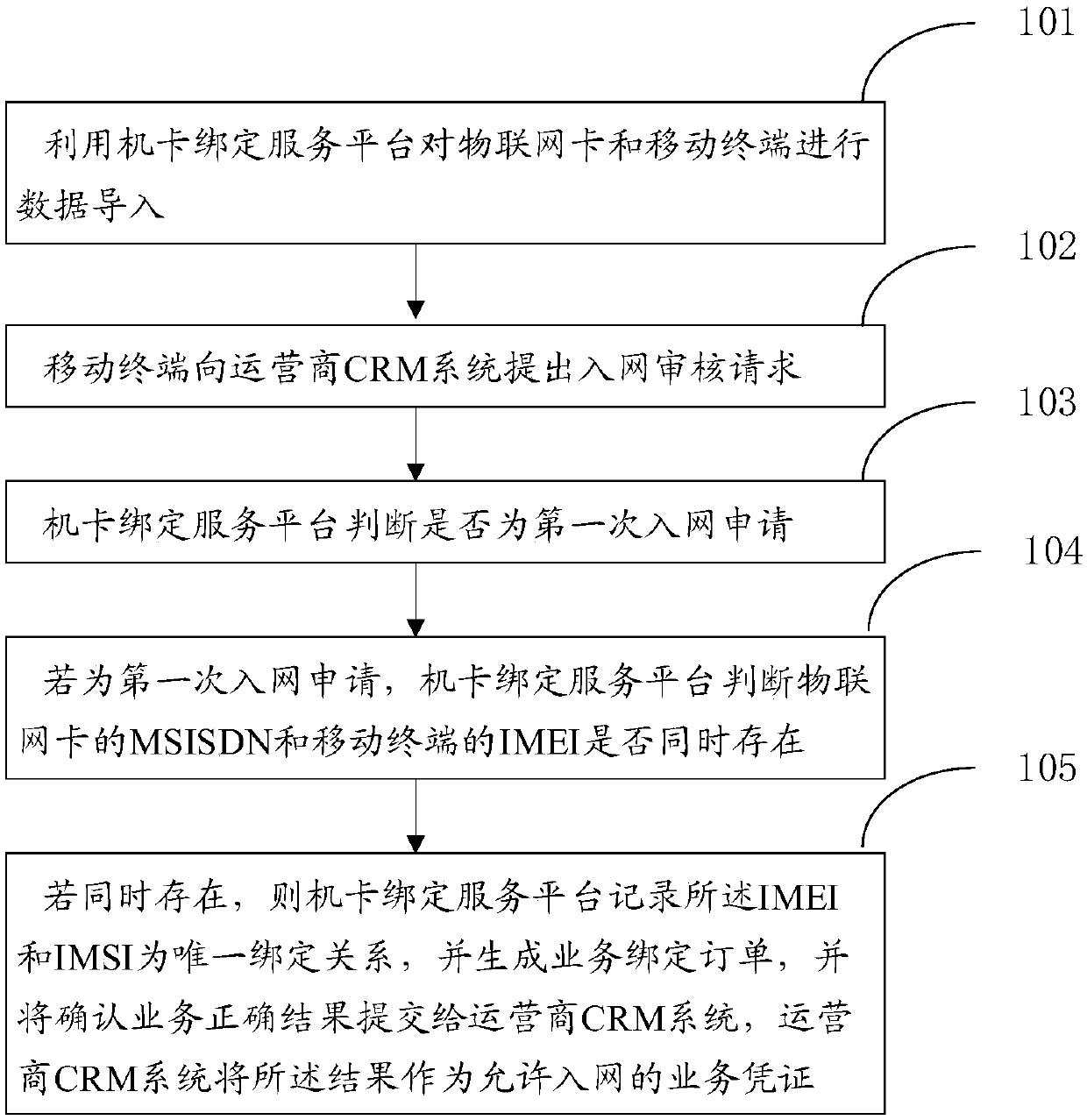
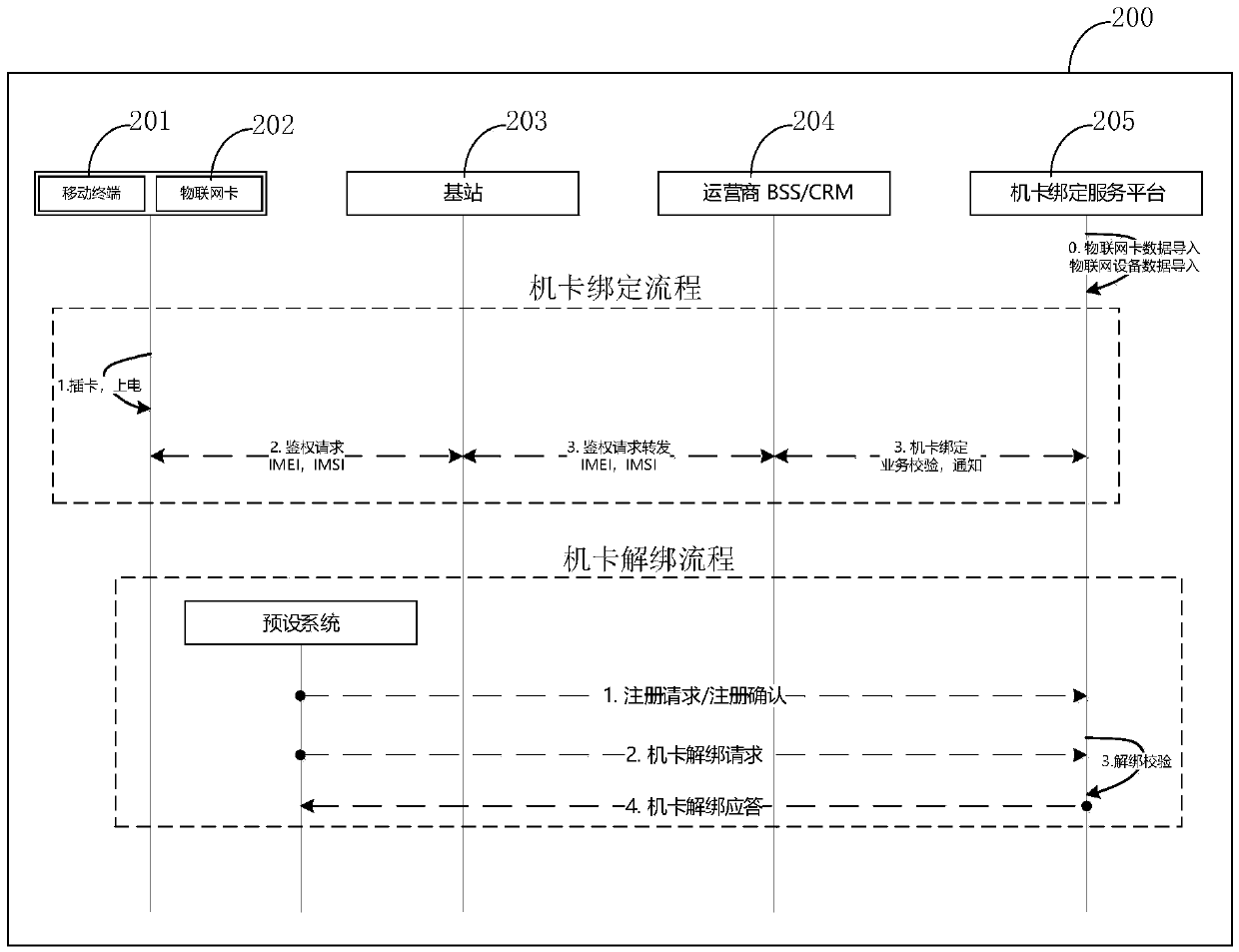
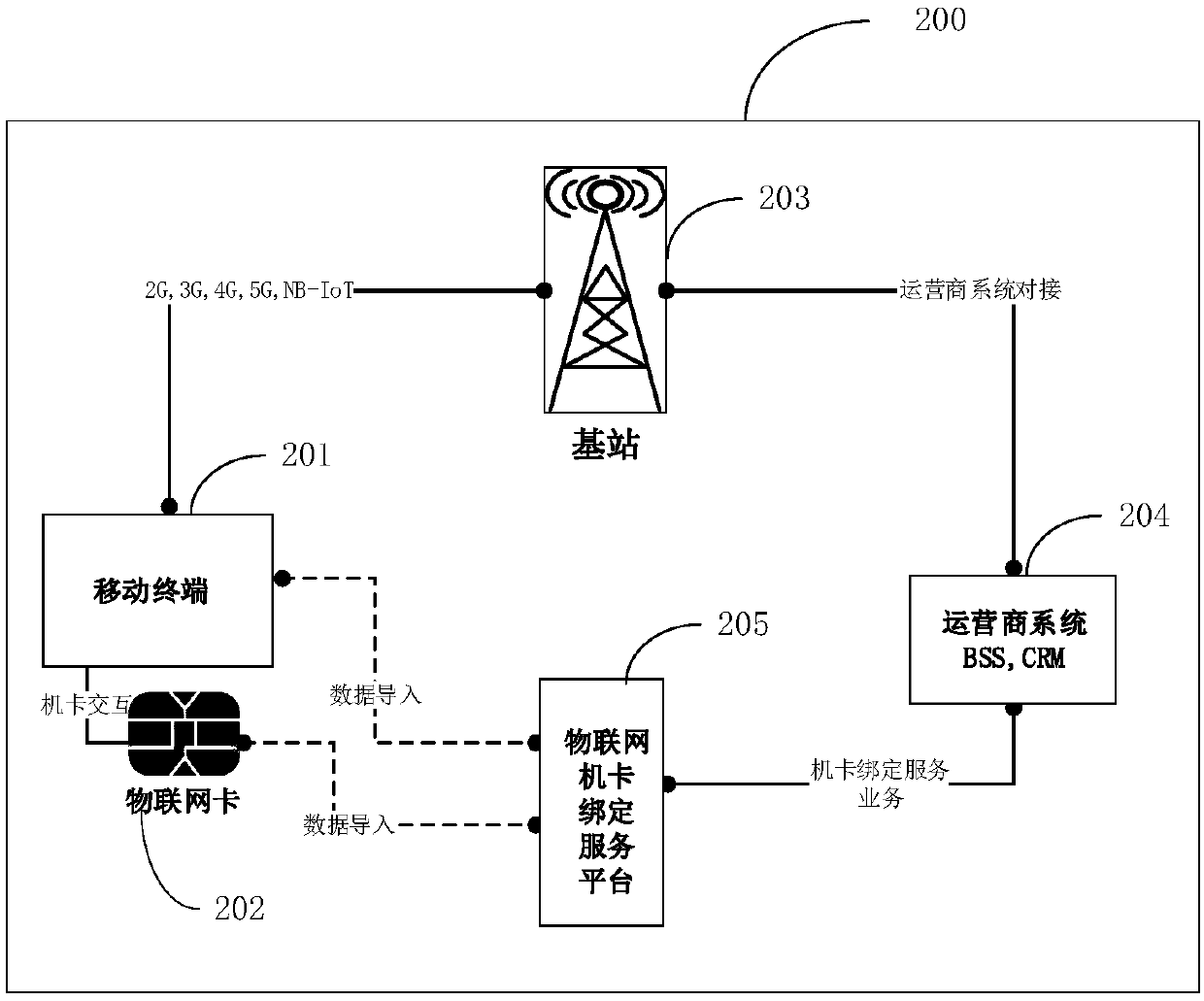
Method and system for binding Internet of Things service machine card
PendingCN110446200AThe binding process is simpleImprove binding efficiencyNetwork data managementInternet of ThingsMSISDN
The invention relates to a method and a system for binding Internet of Things service machine card. The method comprises the following steps: performing data import on an Internet of Things card and amobile terminal by using a machine-card binding service platform; the mobile terminal puts forward a network access auditing request to an operator CRM system; judging whether the application is a first network access application or not by the machine-card binding service platform; if the application is the first network access application, judging whether the MSISDN of the Internet of Things card and the IMEI of the mobile terminal exist at the same time or not by the machine card binding service platform; and if the IMEI and the IMSI exist at the same time, recording the IMEI and the IMSI as a unique binding relationship by the machine-card binding service platform, generating a service binding order, and submitting a service correctness confirmation result to an operator CRM system, wherein the operator CRM system takes the result as a service voucher allowing network access. According to the method and the system, special customization of a machine card is not needed. The intelligent binding and unbinding functions between the mobile terminal and the network access authentication module SIM can be realized when the Internet of Things accesses the network by adopting a cellulartelecommunication network.
Owner:WATCHDATA SYST +1
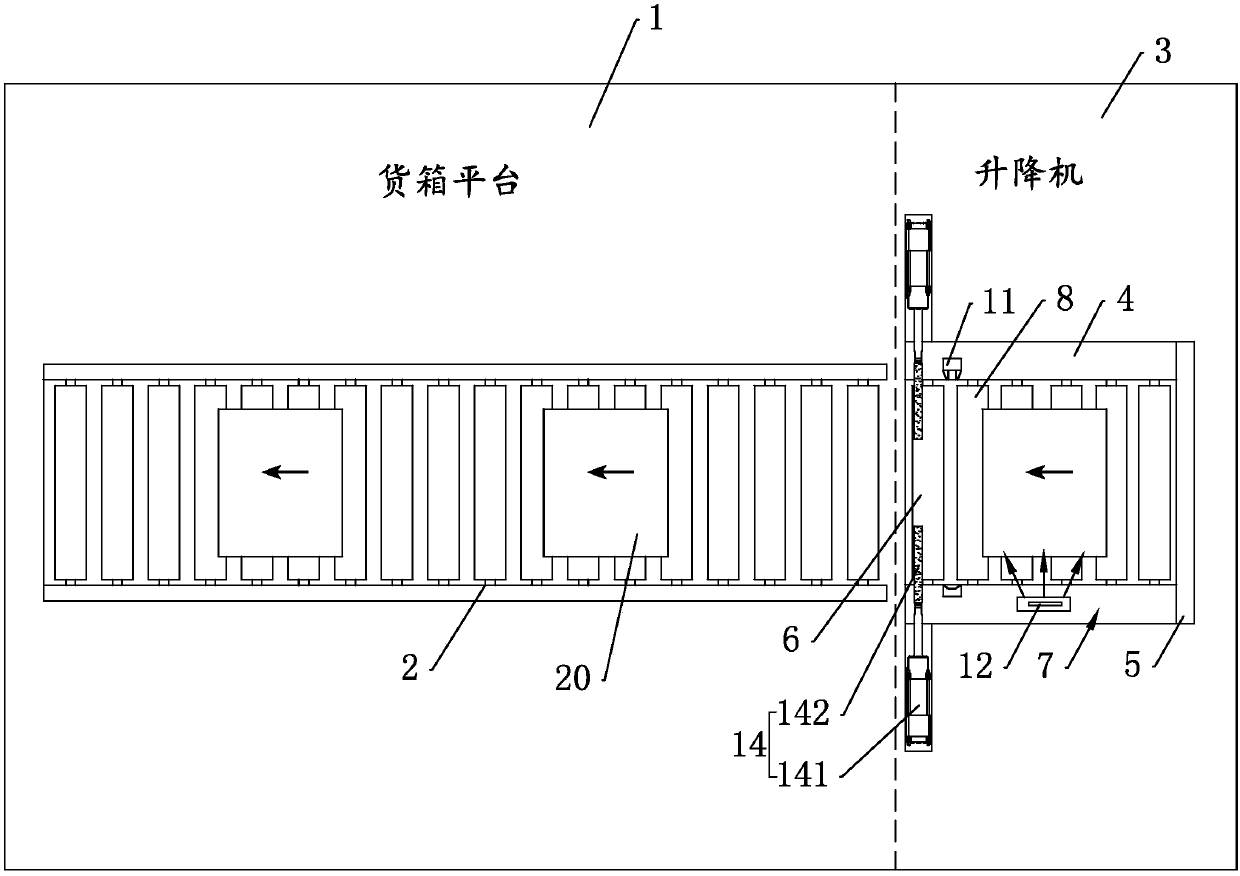
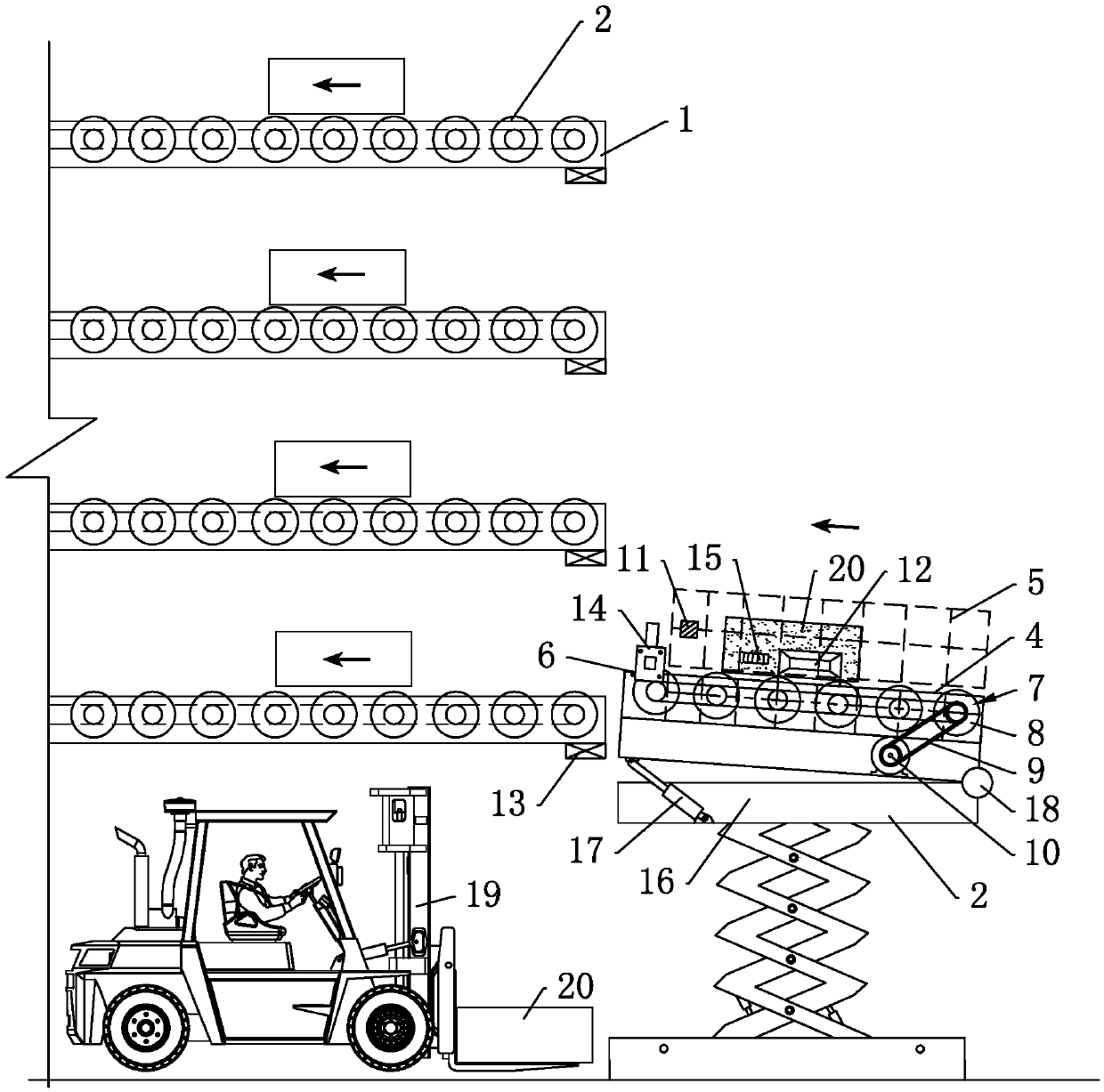
Container leveling conveying system used in large logistics warehouse
The invention relates to a container leveling conveying system used in a large logistics warehouse, and belongs to the technical field of logistics warehouse conveying systems. The container levelingconveying system is used for conveying containers which are loaded in pallets; the container leveling conveying system comprises a multiple levels of container platforms, a horizontal level sensor located on each container platform, a conveyer belt arranged on each container platform, a lifter device arranged on a bottom level container platform, a label identification device located on the lifterdevice and a container pushing device; the container pushing device is arranged on the lifter device and is used for applying horizontal pushing force to a container on the lifter device to push thecontainer out of the lifter device to be received by the conveyer belt; and the container is identified by the label identification device, so that the lifter device reaches a container platform on which the container is located. The container leveling conveying system has the advantages that containers conveyed by a forklift can be identified automatically, and intelligent leveling conveying is performed, so that labor and equipment operation cost is lowered.
Owner:北京春溢通物流有限公司
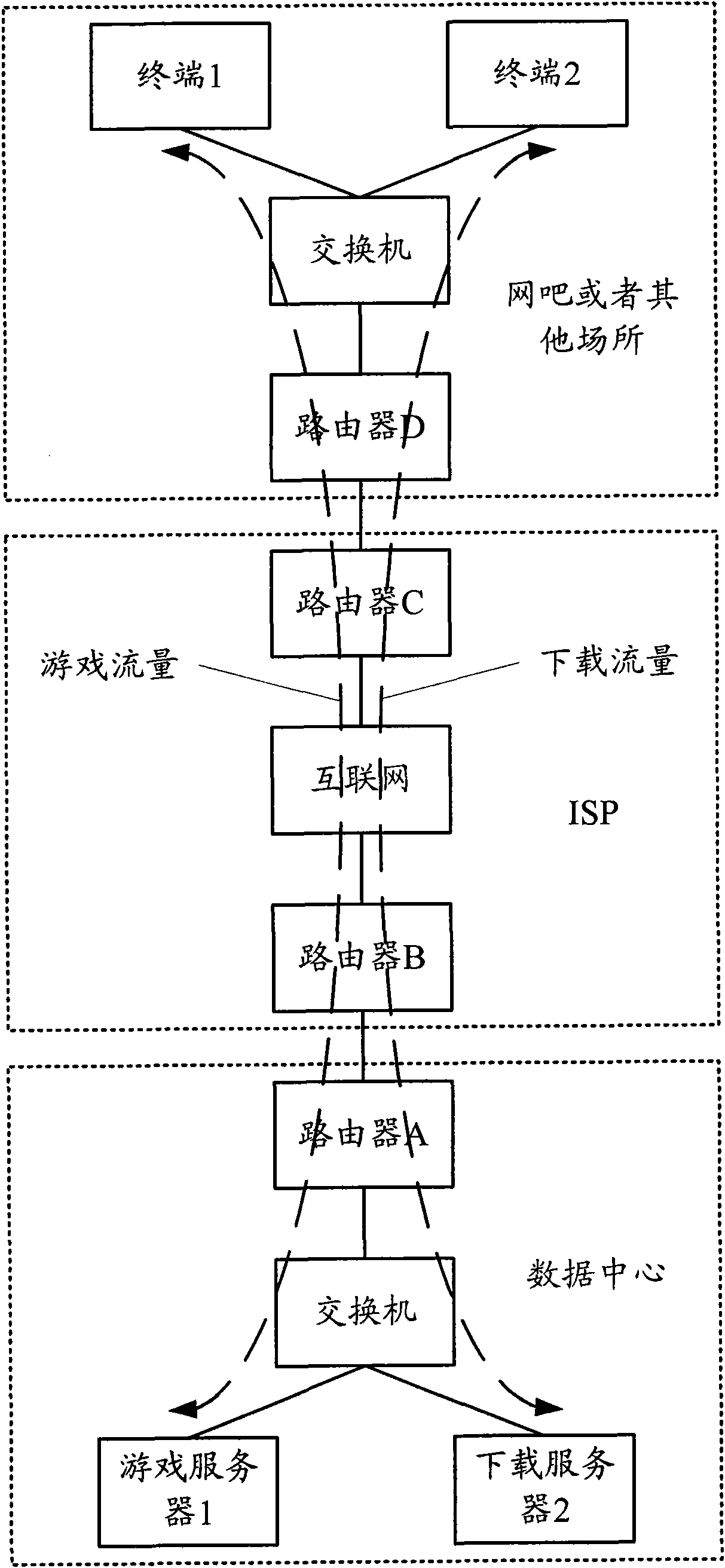
Method and device for dispatching TCP data stream
ActiveCN101616098AIntelligent RecognitionAvoid attackData switching networksSession managementData stream
The invention discloses a method and a device for dispatching TCP data stream, which can intelligently identify small-sized message data stream based on the technology of session management of the small-sized message data stream, meet the priority dispatching requirement of small-sized message, can intelligently identify the small-sized message data stream on a full-network router, simultaneously avoid being attacked, and further carry out priority dispatching for random specific message type according to the technical ideas of the invention.
Owner:NEW H3C BIG DATA TECH CO LTD
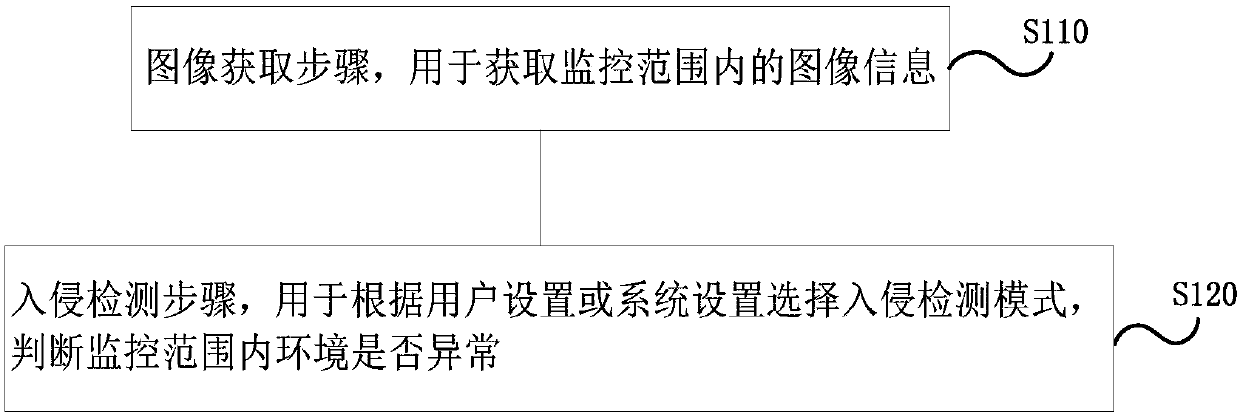
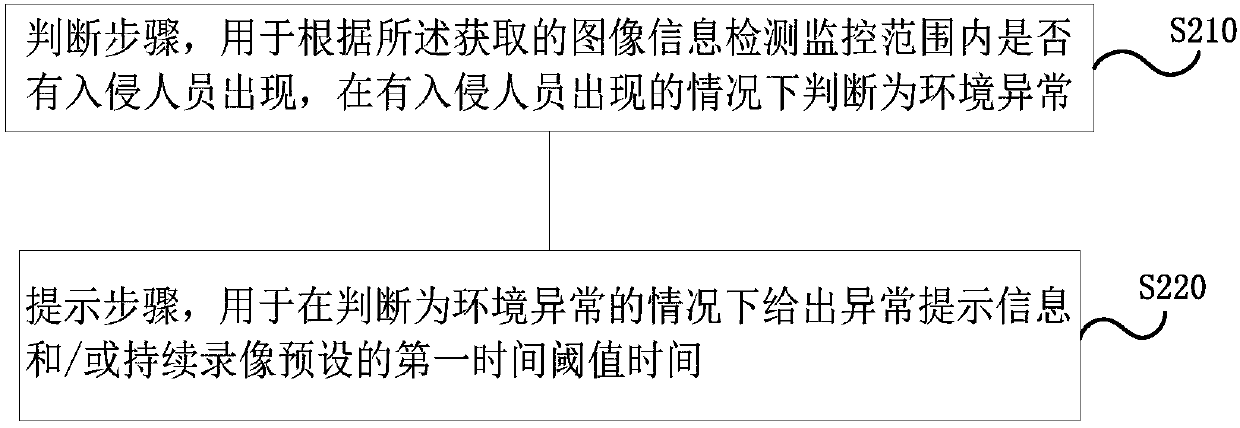
Security and protection monitoring method and device and air conditioner with same
InactiveCN107860097AImprove reliabilityIntelligent RecognitionMechanical apparatusCharacter and pattern recognitionComputer scienceComputer security
The invention provides a security and protection monitoring method and device and an air conditioner with the device. The security and protection monitoring method comprises the image acquiring step for acquiring image information within the monitoring range and an intrusion detection step, wherein in the intrusion detection step, intrusion detection modes are selected according to user settings or system settings, whether the environment within the monitoring range is abnormal or not is judged, and the intrusion detection modes include the ordinary detection mode and / or the stranger detectionmode; in the ordinary detection mode, whether an intruder appears or not within the monitoring range is detected according to the acquired image information, and it is judged that the environment isabnormal under the situation that the intruder appears; and in the stranger detection mode, whether the intruder appears or not within the monitoring range is detected according to the acquired imageinformation, and under the situation that the intruder appears, whether the environment is abnormal or not is judged according to the identity of the intruder. According to the technical scheme, monitoring images can be checked remotely, the reasonable intrusion detection modes can be selected, the intruder can be recognized more intelligently, and the environment safety is guaranteed better.
Owner:GREE ELECTRIC APPLIANCES INC
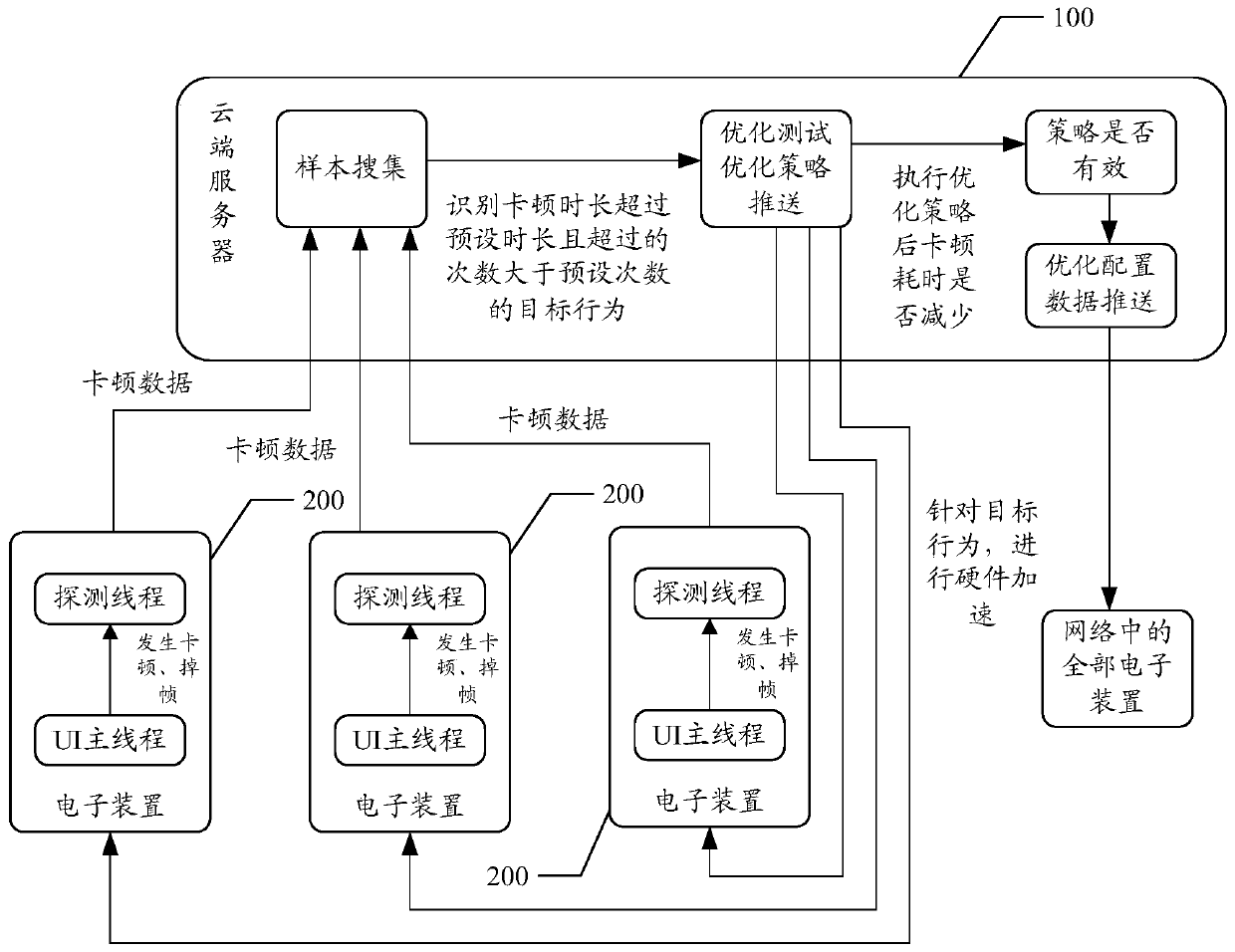
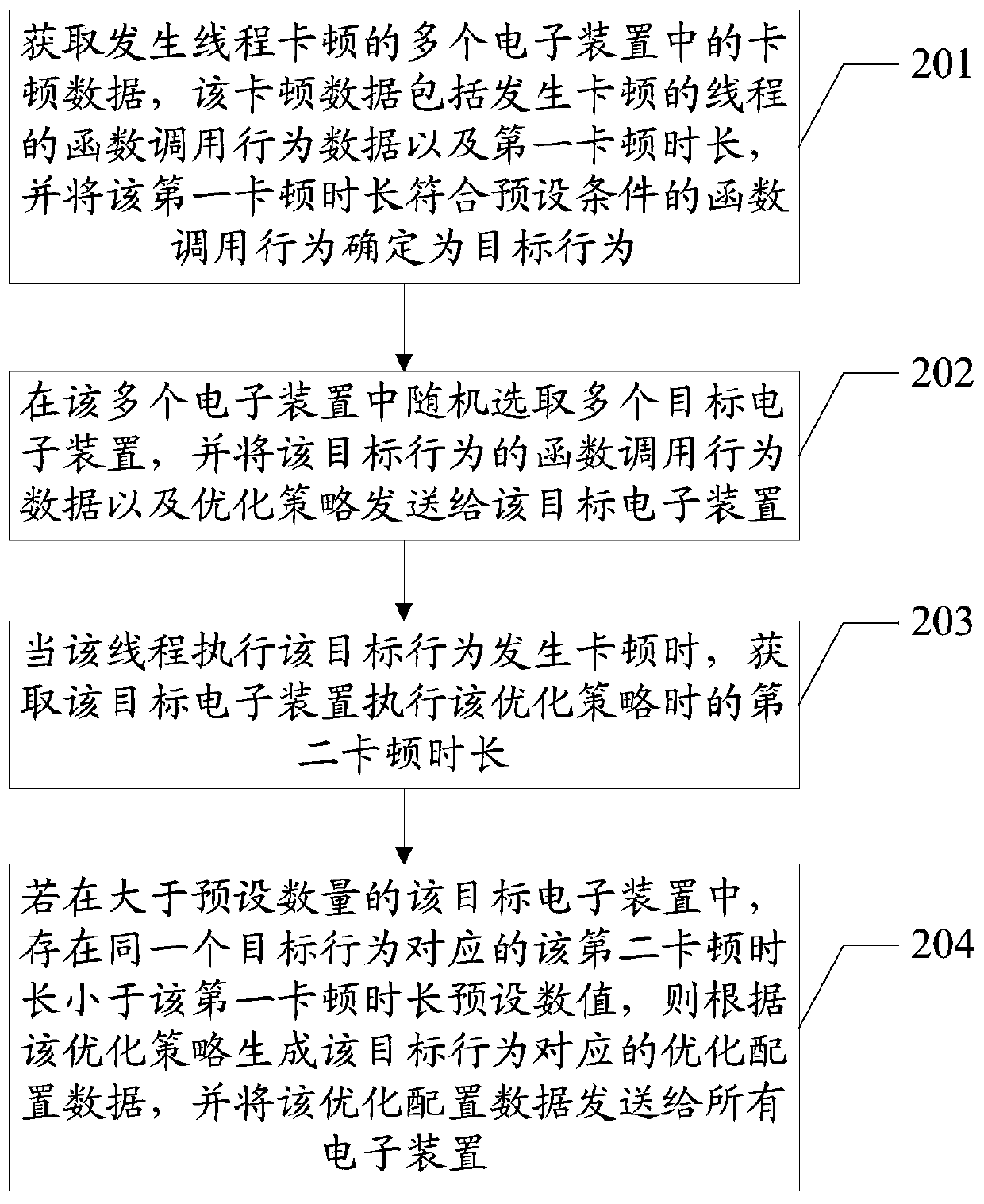
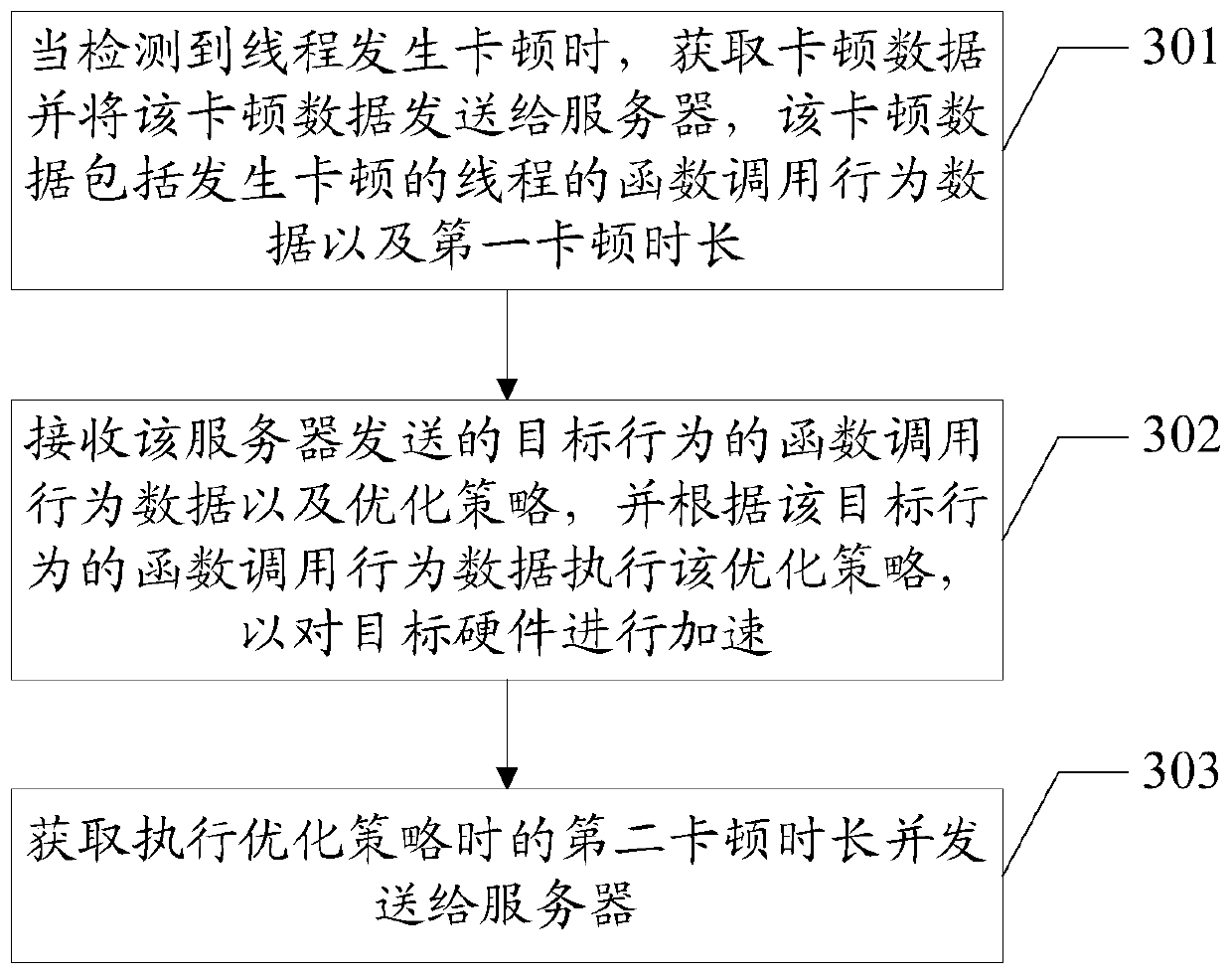
Jamming optimization method, server, electronic device and computer readable storage medium
The embodiment of the invention discloses a jamming optimization method applied to the communication technology field, the method comprises the following steps of: acquiring the jamming data of threadjamming; determining the function calling behavior of which the first jamming duration conforms to a preset condition as a target behavior; and sending the function calling behavior data of the target behavior and the optimization strategy to the target electronic device, when the thread executes the target behavior and jamming occurs, obtaining a second jamming time length when the target electronic device executes the optimization strategy, and if the second jamming duration corresponding to the same target behavior is smaller than the first jamming duration and reaches the preset value inthe target electronic devices with the number larger than the preset number, generating optimization configuration data corresponding to the target behavior according to an optimization strategy, andsending the optimization configuration data to all the electronic devices. The embodiment of the invention further discloses a server, an electronic device and a computer readable storage medium, thejamming can be reduced, and the applicability of solving the jamming problem is improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
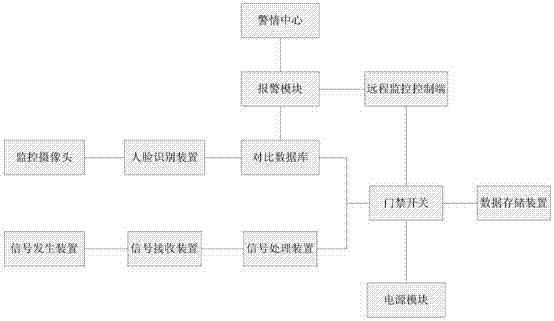
Access control system capable of identifying and alarming intelligently
InactiveCN107301700AIntelligent RecognitionAutomatic door releaseCharacter and pattern recognitionIndividual entry/exit registersSurveillance cameraEmbedded system
The invention discloses an access control system capable of identifying and alarming intelligently. The access control system capable of identifying and alarming intelligently comprises a monitoring camera, a face identifying device, a comparison database, a signal generating device, a signal receiving device, a signal processing device, an alarming module, an alarming situation centre, an access control switch, a remote monitoring control end, an access control switch, a power supply module and a data storage device; data can be transmitted among the monitoring camera, the face identifying device, the comparison database, the signal generating device, the signal receiving device, the signal processing device, the alarming module, the alarming situation centre, the access control switch, the remote monitoring control end, the access control switch, the power supply module and the data storage device; the monitoring camera is used for acquiring video data in a target area and transmitting the data to the face identifying device; the face identifying device is used for converting the video data which are transmitted by the monitoring camera into pictures and transmitting the pictures into the comparison database; the comparison database is used for comparing the obtained pictures with the pictures which are stored in the database, and transmitting a comparison result to the access control switch and the alarming module; the signal generating device is used for transmitting a signal to the signal receiving device when the signal generating device is at a certain distance from the signal receiving device.
Owner:成都智慧家信息技术有限公司
Method for catching images and quickly recognizing targets and embedded device
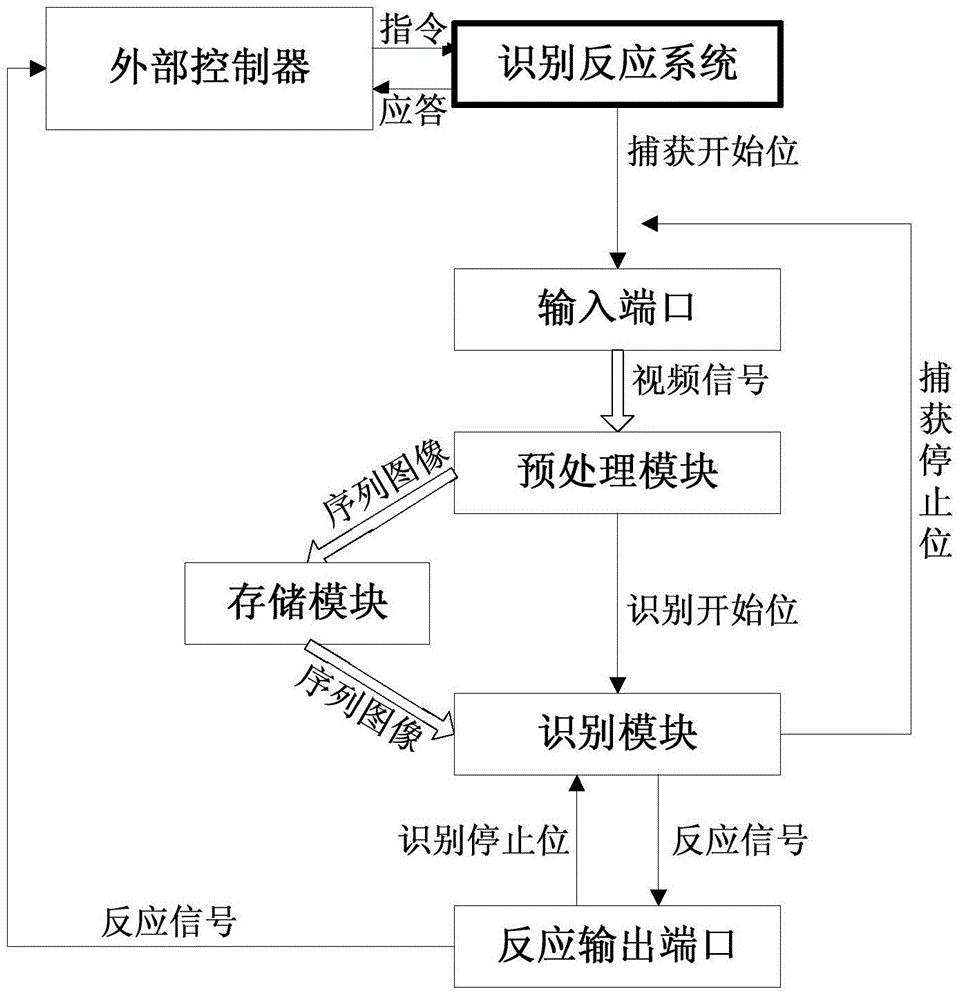
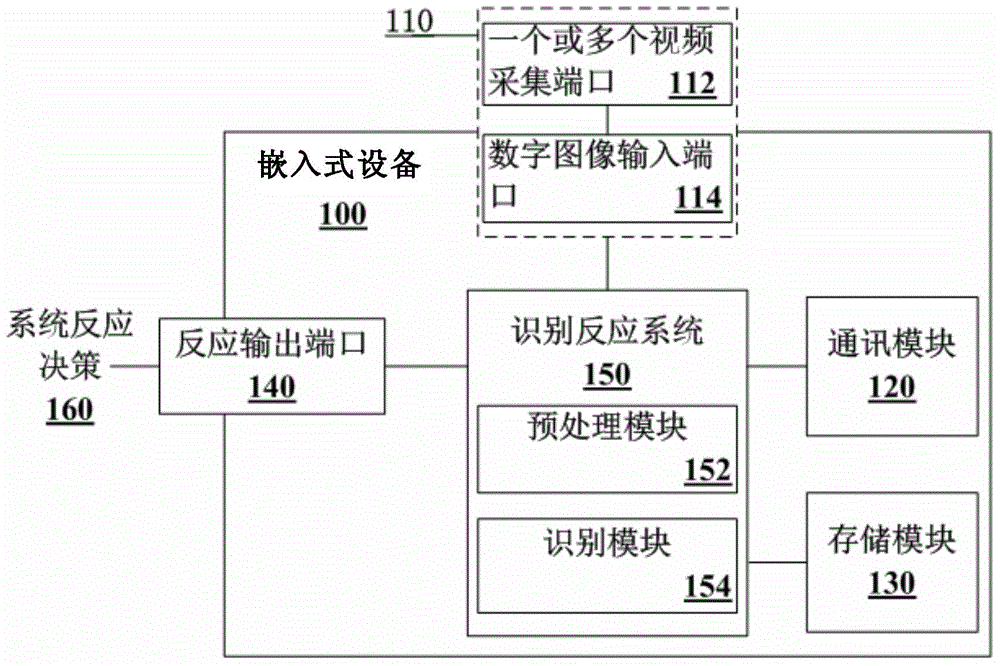
InactiveCN104463114AReduce volumeReduce power consumptionTelevision systemsBiometric pattern recognitionPattern recognitionData acquisition
The invention provides a method for catching images and quickly recognizing targets and an embedded device. The embedded device comprises an input port used for receiving video signals and a recognition reaction system used for catching the images and quickly recognizing the targets. The input port comprises a video collection port and a digital image input port. The recognition reaction system comprises a preprocessing module and a recognizing module. The embedded device can be applied to the fields of intelligent homes, unmanned detection and the like, the purposes that the targets in the images or the videos can be quickly recognized during unmanned monitoring and reaction signals are sent out according to the external device requirements are achieved, the embedded device transplants target recognition operation to an embedded environment from a computer, the transmission loss is reduced, and meanwhile the embedded device only having a data collection function can be more intelligent.
Owner:TSINGHUA UNIV
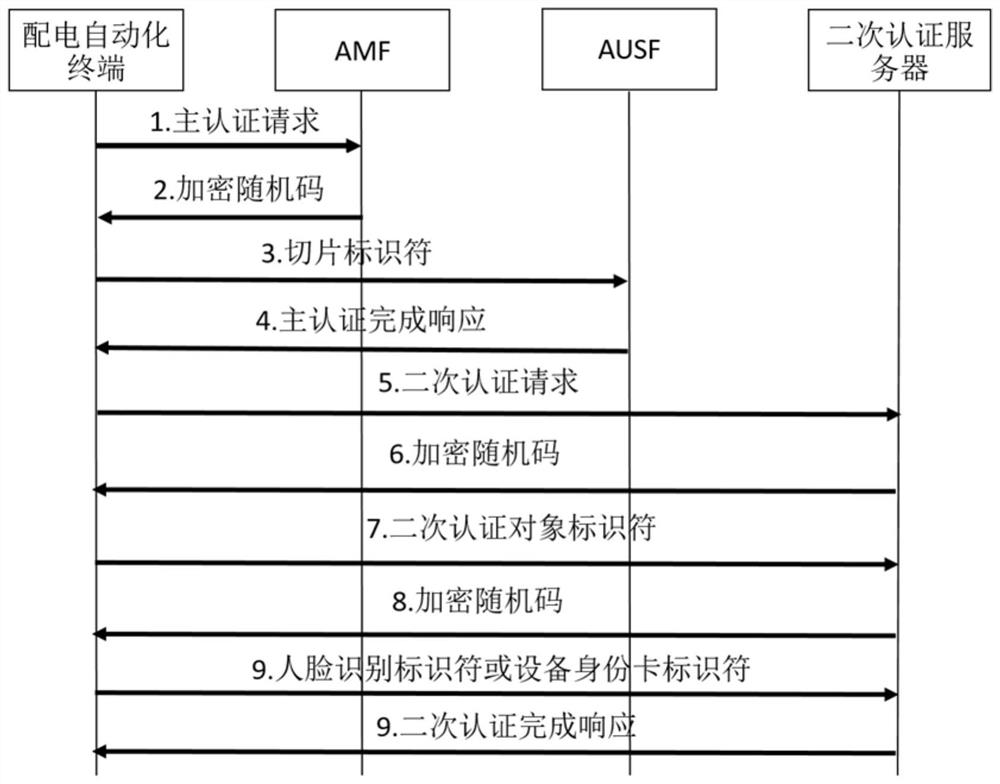
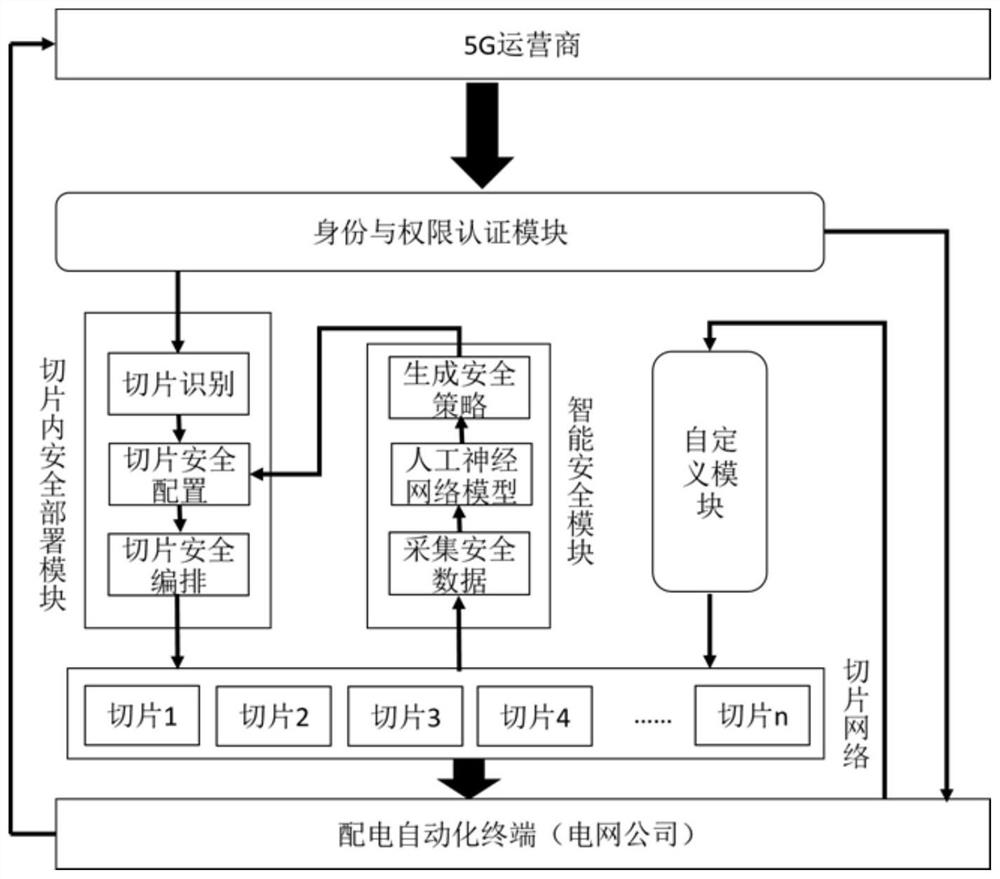
5G network slice-based power Internet-of-Things security management method and system
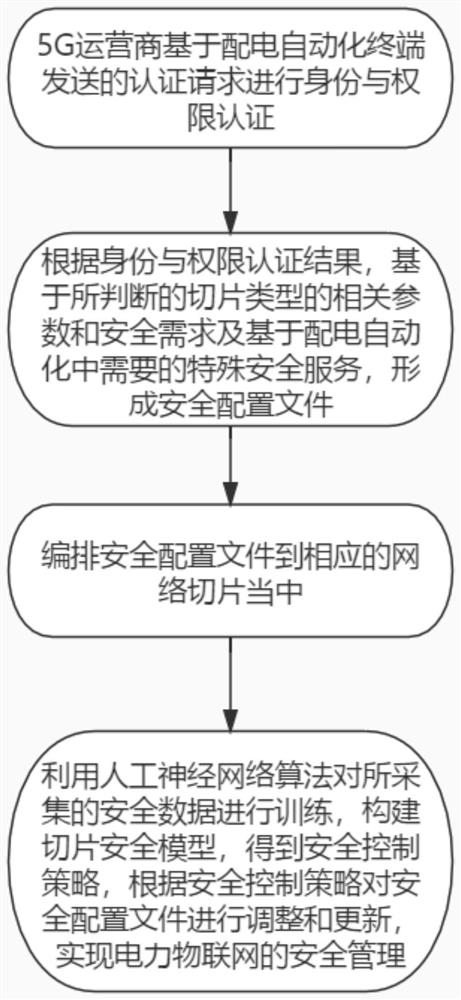
PendingCN112616124AIntelligent RecognitionIntelligent identificationParticular environment based servicesData switching networksInternet of Things5G
The invention discloses a 5G network slice-based power Internet-of-Things security management method and system. The method comprises the steps of: enabling a 5G operator to perform identity and authority authentication based on an authentication request sent by a power distribution automation terminal; according to the identity and authority authentication result, forming a security configuration file based on the relevant parameters and security requirements of the judged slice type and based on the special security service required in the power distribution automation; arranging the security configuration file into a corresponding network slice; and training the acquired security data by using an artificial neural network algorithm, constructing a slice security model to obtain a security control strategy, and adjusting and updating the security configuration file according to the security control strategy to realize security management of the power Internet of Things. According to the invention, the identification of the security threat in the distribution automation slice network is more intelligent, the security deployment is more diversified, and the 5G authentication is safer and more reliable.
Owner:广东电力通信科技有限公司
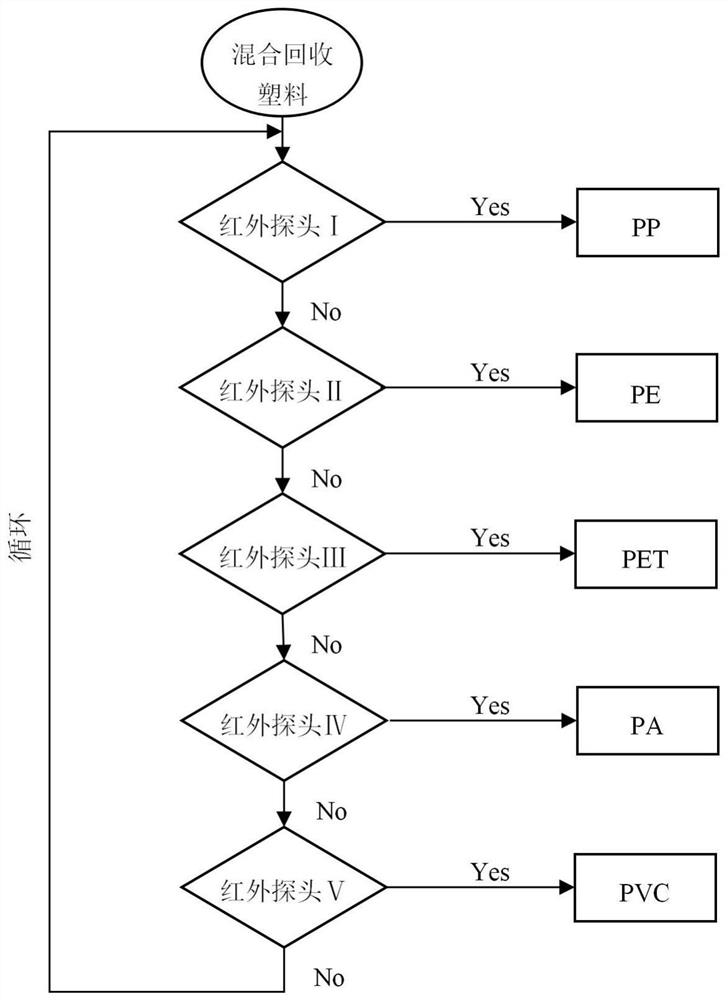
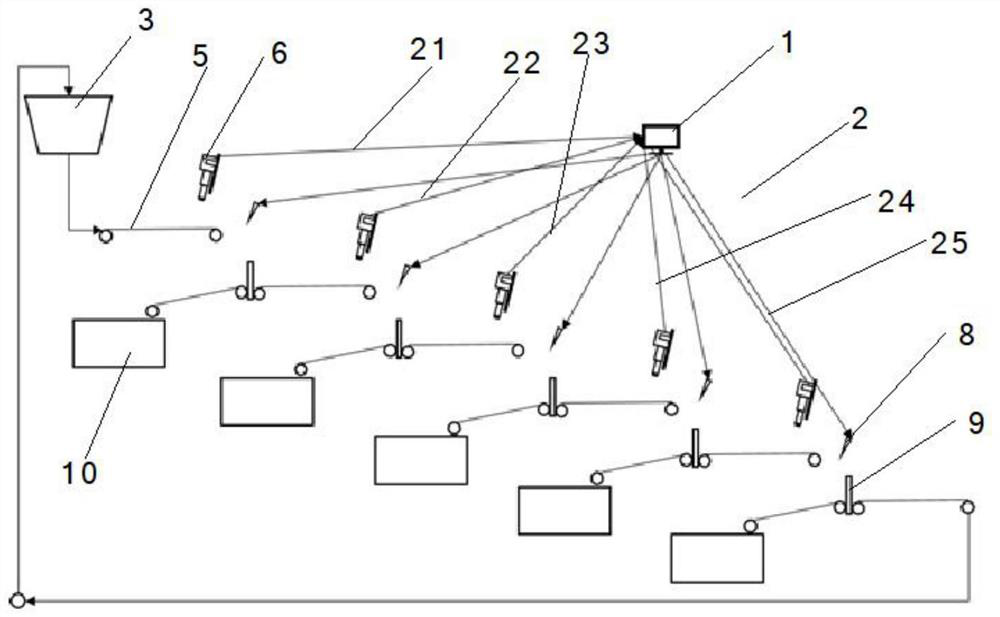
High-throughput intelligent sorting method and system for recovering waste plastic
InactiveCN112693032AEfficient separationAccurate separationPlastic recyclingMechanical material recoveryProduction lineProcess engineering
The invention discloses a high-throughput intelligent sorting method for recovering waste plastic. The method comprises the following steps that (1) a high-throughput intelligent sorting system is arranged, and screening manipulators are sequentially arranged from top to bottom in a layered manner from a hopper to form a multi-layer infrared screening production line; (2) the recovered mixed waste plastic fragments are conveyed to all infrared screening manipulators for spectrum recognition sorting and sorting; (3) the step (2) is repeated, the recovered mixed waste plastic fragments are sequentially fed into all the infrared screening manipulators to complete a first sorting cycle; (4) subsequent sorting circulation is carried out on the remaining unrecognized mixed waste plastic until all the waste plastic is sorted; and (5) the single-component waste plastic is enabled to be separately used for subsequent regeneration processing. The invention further discloses a high-throughput intelligent sorting system for implementing the method. According to the high-throughput intelligent sorting method and system, equipment and labor investment for recovering and reproducing the waste plastic can be greatly reduced, and the requirements of large scale and low cost are met.
Owner:SHANGHAI UNIV
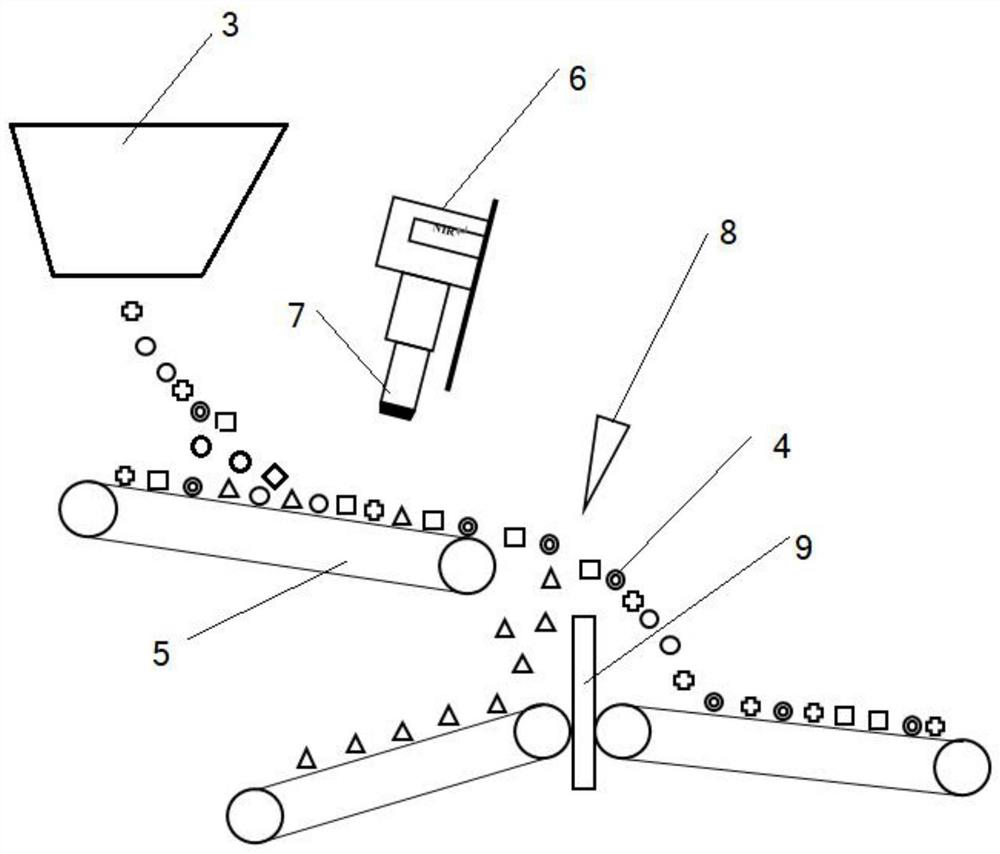
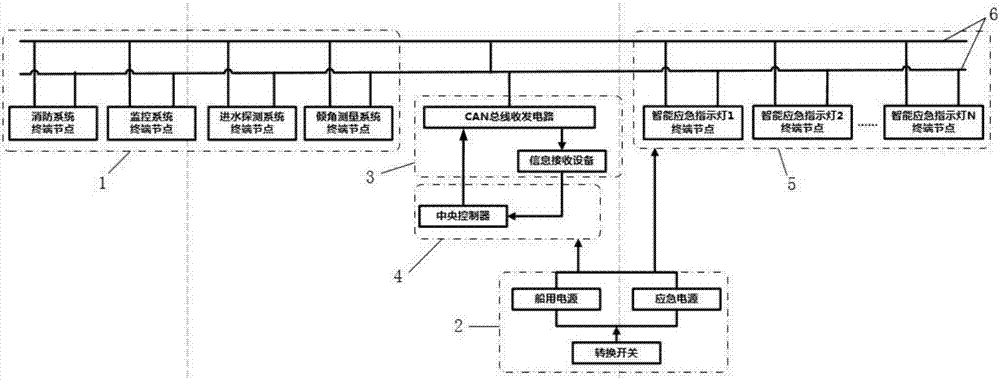
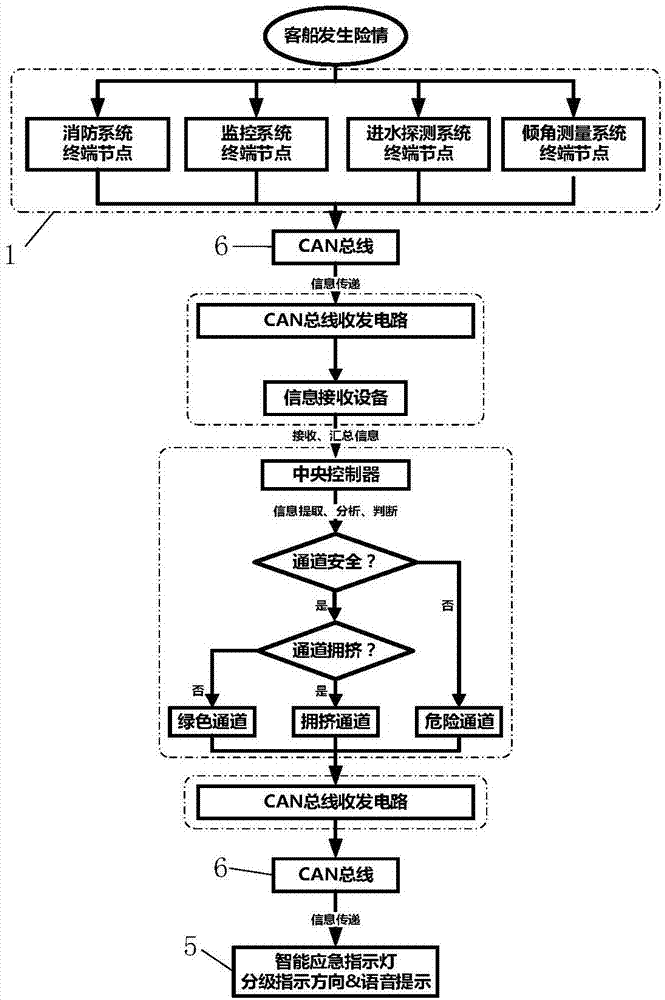
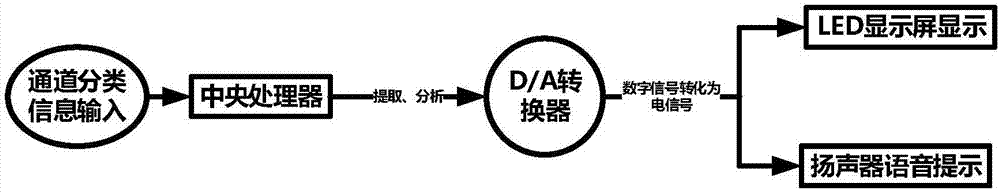
Passenger ship emergency escape warning indicating system
InactiveCN107505868AAchieve timelinessImprove management efficiencyProgramme controlComputer controlElectric energyInformation analysis
The invention discloses a passenger ship emergency escape warning indicating system. A system power supply module provides power for the passenger ship emergency escape warning indicating system. An information collecting module acquires the movement speed of the hull of a passenger ship, heeling and pitching angles of the passenger ship, smoke in each compartment and passage, and the degree of congestion in each passage in real time through each information receiving device, and transmits the information to an information analysis module. The information analysis module is mainly composed of a central controller and related circuits thereof. After the central controller extracts the information received from the information collecting module for analysis, the central controller determines the type of each passage according to the safety and the degree of congestion in each passage, and transmits the type to a warning indicating module. The warning indicating module indicates a correct escape route for people in the manners of an LED display and voice prompt through an emergency indicator light. The system can automatically determine the safety and the degree of congestion of each passage on board, and indicates the safe and clear escape route for people on board in the manner of display and voice prompt.
Owner:WUHAN UNIV OF TECH
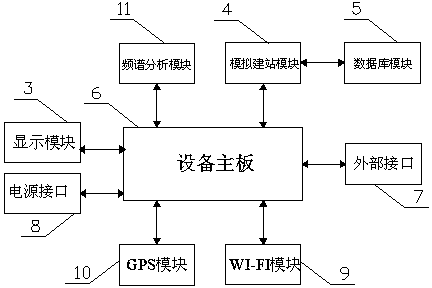
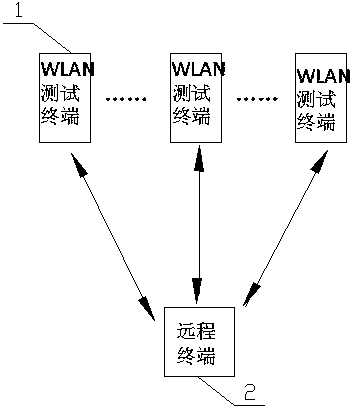
3D modeling-based WLAN wireless network testing system
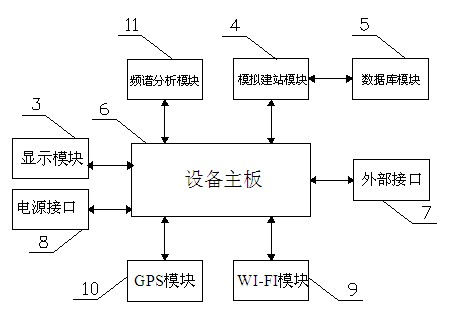
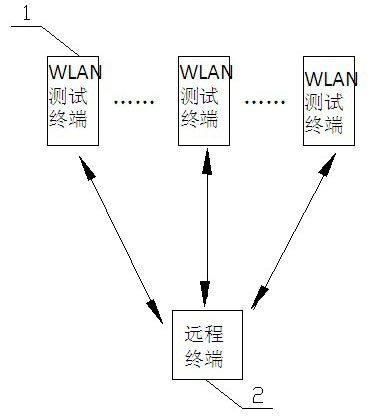
InactiveCN102131214AVersatileImprove business performanceWireless communicationWi-FiComputer Aided Design
The invention relates to a wireless local area network (WLAN) wireless network testing system, in particular to a three-dimensional (3D) modeling-based WLAN wireless network testing system. The system comprises a WLAN testing terminal (1) and a remote terminal (2), wherein the WLAN testing terminal (1) comprises an equipment motherboard (6), and a display module (3), a wireless fidelity (WI-FI) module (9), an external interface (7) and a power supply (8) which are connected with the equipment motherboard (6); the WLAN testing terminal (1) is in communication connection with the remote terminal (2) through the WI-FI module (9); a 3D analog station construction module (4) is connected to the equipment motherboard (6); and the 3D analog station construction module (4) is connected with a database module (5). According to the technical scheme, the WLAN wireless network testing system can perform 3d browsing, intuitively, attractively and intelligently identify computer aided design (CAD) drawings, and automatically analyzes the simulated effect; the function of the WLAN wireless network testing system is enriched; and the comprehensive service capacity of the WLAN wireless network testing system is improved.
Owner:ZHEJIANG SAFE COMM EQUIP
Method for testing plasma flocs
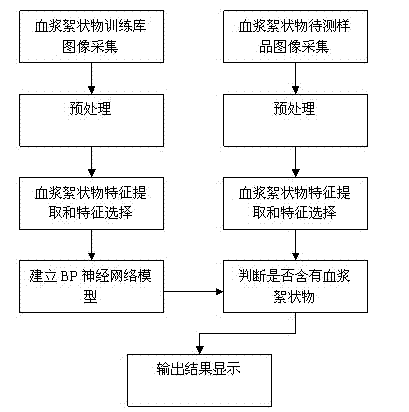
InactiveCN102509106AImprove accuracyReduce work intensityBiological neural network modelsCharacter and pattern recognitionNon destructiveFeature extraction
The invention belongs to the field of laboratory medicine, and particularly relates to a non-destructive testing method for plasma flocs. The result of the sample to be tested is obtained by the steps of image acquisition, image processing, characteristic extraction, neural network model, comparison judgment and output and display. Compared with the traditional manual test, the method provided by the invention has high reliability and stability in testing the plasma flocs and higher speed and accuracy, and can test multiple indexes at the same time, thereby improving the production efficiency, reducing the labor intensity and lowering the test cost.
Owner:CHONGQING UNIV
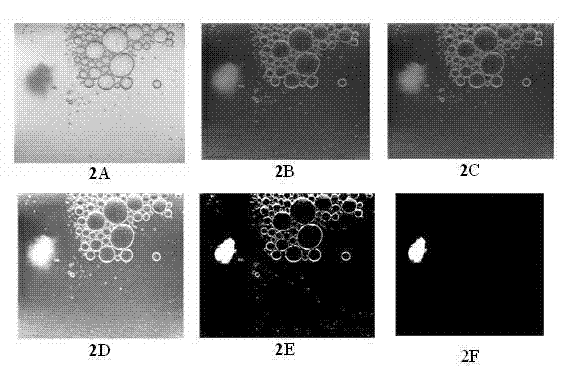
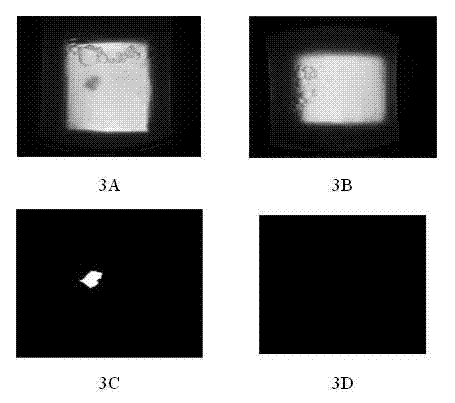
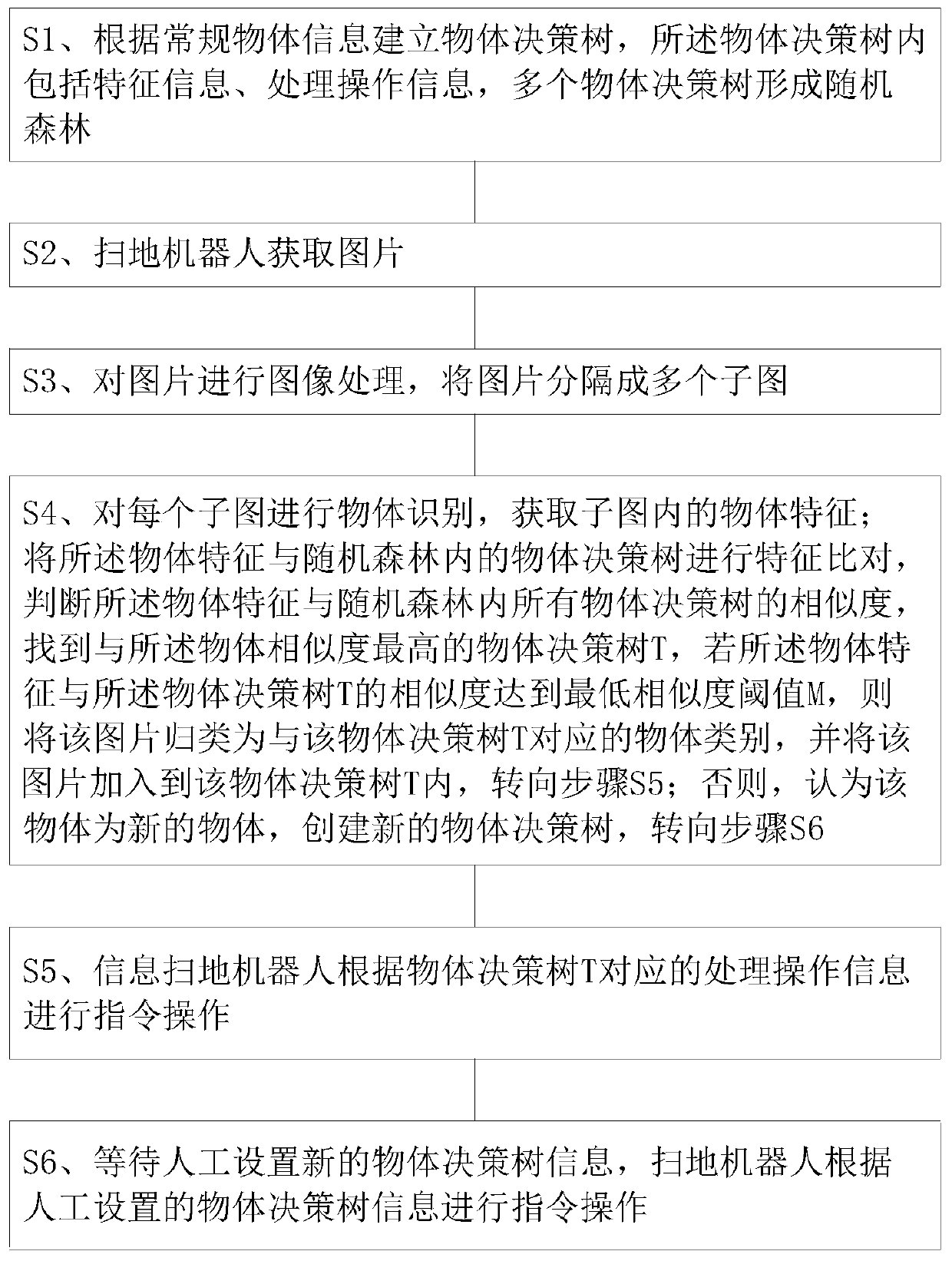
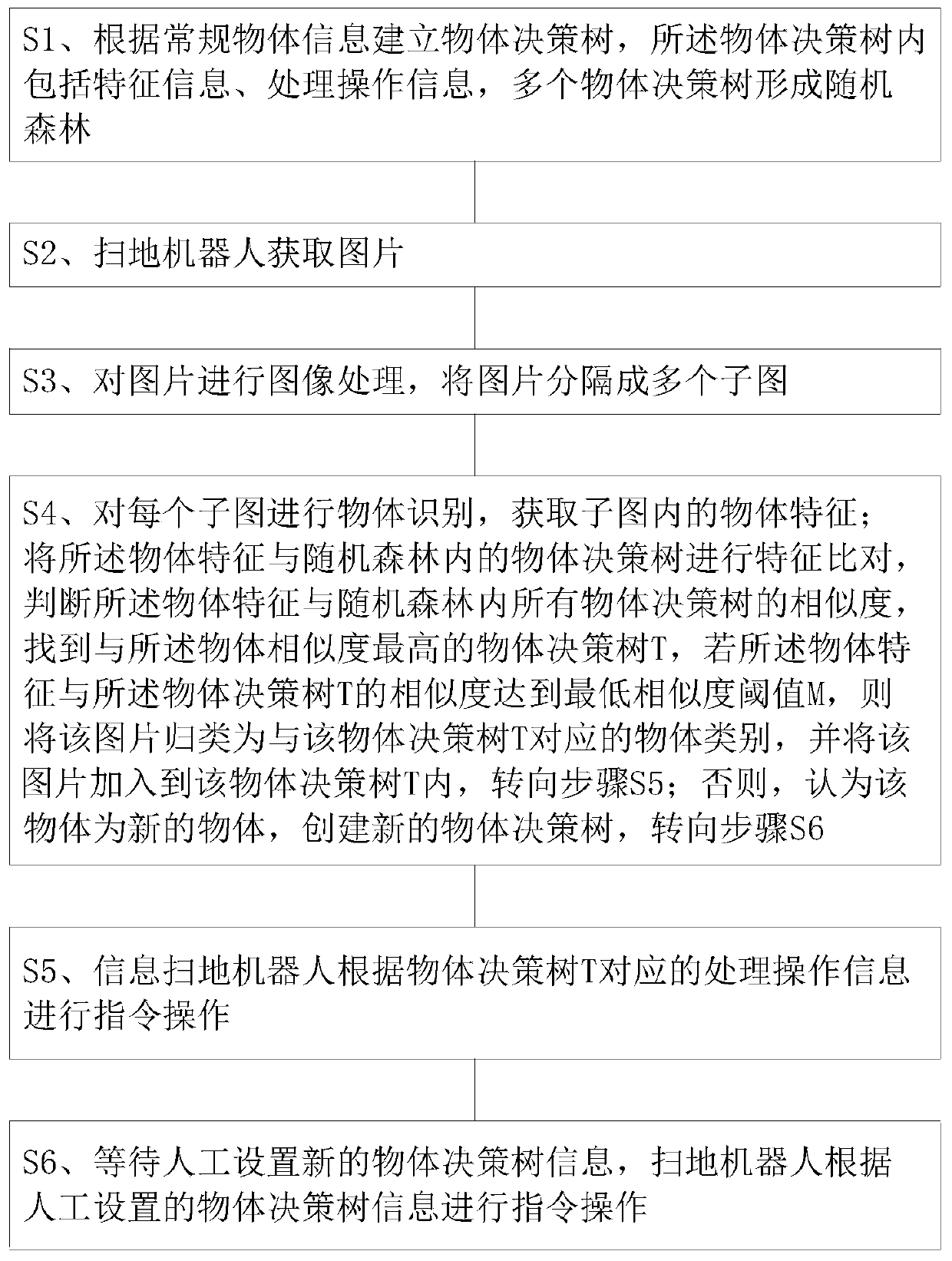
Object identification method for floor sweeping robot
InactiveCN110013197AIntelligent recognitionImprove accuracyCarpet cleanersFloor cleanersAlgorithmRandom forest
The invention discloses an object identification method of a floor sweeping robot. The method comprises the following steps: comparing object decision trees in a random forest with object characteristics in a picture obtained by the floor sweeping robot to find an object decision tree with the highest similarity to the object characteristics; when the compared similarity is greater than a threshold value M, the floor sweeping robot recognizes the object shot by the robot as object information corresponding to the object decision tree so as to perform corresponding instruction operation; and when the similarity is smaller than the threshold value M, after an object decision tree is manually added, the floor sweeping robot records the information of the new object and can learn and perfect the object decision trees independently. The object identification method of the floor sweeping robot can enable the floor sweeping robot to carry out more intelligent self learning and identificationon objects, and has the advantages of being high in intelligent degree and high in self learning capacity.
Owner:SHANGHAI TIANCHENG COMM TECH
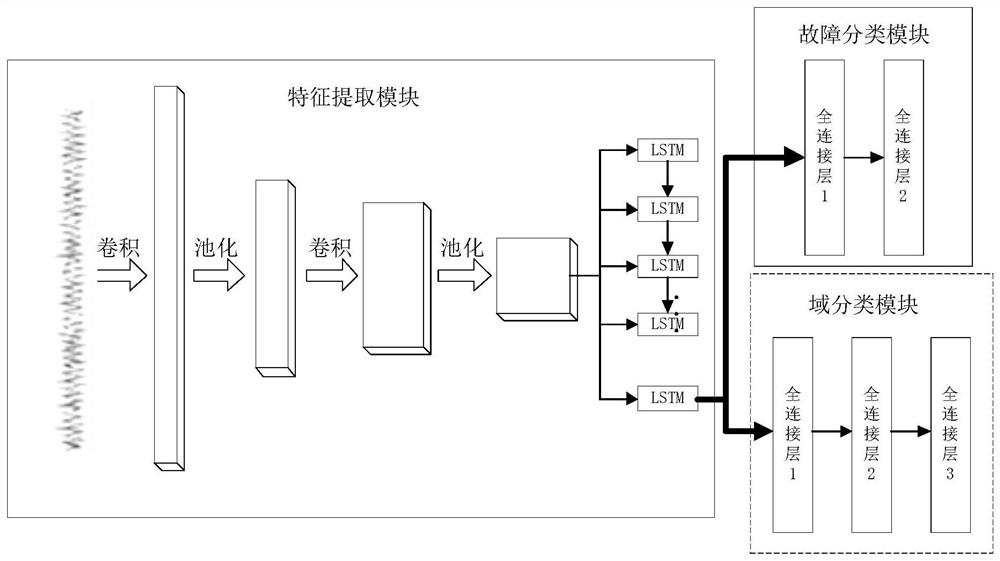
Rolling bearing fault diagnosis method and system based on domain migration and storage medium
PendingCN112418175AImprove diagnostic accuracyIntelligent RecognitionCharacter and pattern recognitionNeural architecturesEngineeringA domain
The invention relates to a domain migration-based rolling bearing fault diagnosis method and system and a storage medium. The method comprises steps of constructing a domain migration deep learning network; and inputting the source domain data and the target domain data into a domain migration deep learning network together, and training the network so that the domain to which the features belongcannot be distinguished while the extracted features are subjected to fault classification. According to the method, various fault types can be better and intelligently identified, and the method hashigh diagnosis accuracy. The method can be widely applied to the technical field of mechanical fault diagnosis.
Owner:BEIJING INFORMATION SCI & TECH UNIV
Virtual key and multi-area protection method and device for automatic door control
PendingCN110454027AReduce wearExtend your lifePower-operated mechanismKey pressingAutomatic train control
Owner:B E A ELECTRONICS BEIJING
Home service robot intelligent navigation algorithm adapting to complex environment
InactiveCN112180916AIntelligent RecognitionChoose to adaptPosition/course control in two dimensionsSimulationMultiple sensor
The invention discloses a home service robot intelligent navigation algorithm adapting to a complex environment, which integrates information of multiple sensors, reconstructs the working environmentof a robot in real time, effectively enhances the robustness of a system and realizes all-time and all-weather navigation and positioning of the robot in a strange environment. According to the invention, an evaluation model is established, an optimal local path planning algorithm is selected, and the local path planning algorithm is optimized in combination with the height information, so that the problem that a robot cannot accurately judge whether an obstacle exists in a current advancing path or not due to the fact that the robot cannot sense the height information on a map is solved, andthe traditional ant colony algorithm is optimized., and the problem of path planning when the home service robot has a plurality of necessary working points is solved. Meanwhile, the algorithm has higher convergence speed, and the performance of the algorithm is obviously improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Coiled material for AGV vehicle-mounted environment and preparation method of material
ActiveCN109747243AResilientImprove wear resistanceLamination ancillary operationsNon-macromolecular adhesive additivesFiberSurface layer
The invention discloses a coiled material for AGV vehicle-mounted environment and a preparation method of the material. The coiled material has a layered structure and sequentially comprises a stitched felt reinforcing layer, a fiber cloth reinforcing layer, a two-dimensional code printing layer and a transparent surface layer from bottom to top, wherein the stitched felt reinforcing layer is formed by coating a coating material with high permeability on the stitched felt and curing; the fiber cloth reinforcing layer is formed by coating a coating material with high-permeability on the fiber cloth and curing; the fiber cloth reinforcing layer and the stitched felt reinforcing layer are bonded by an adhesive coating material; the two-dimensional code printing layer is formed by printing anadhesive paint on the fiber cloth reinforcing layer and curing; and the transparent surface layer is formed by coating a surface layer coating material on the two-dimensional code printing layer and curing. Through the structural design of the transparent surface layer, the two-dimensional code printing layer and the double-layer reinforcing layer, and the use of the surface coating material, thecoating material with high permeability and the adhesive coating material, the coiled material for the AGV vehicle-mounted environment is obtained; and the coiled material has the characteristics of wear resistance, high skid resistance and high pressure resistance at the same time, and can meet the requirements of AGV vehicles on the ground.
Owner:浙江港流高分子科技股份有限公司
Fault detection device of voice communication system
PendingCN112986734AImprove troubleshooting efficiencyQuick identificationFault location by conductor typesTransmission monitoringVoice communicationEngineering
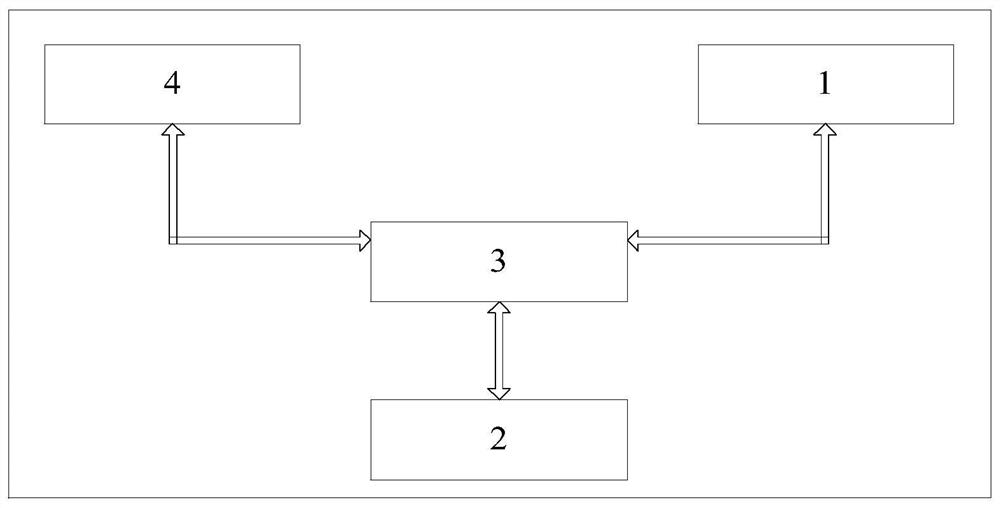
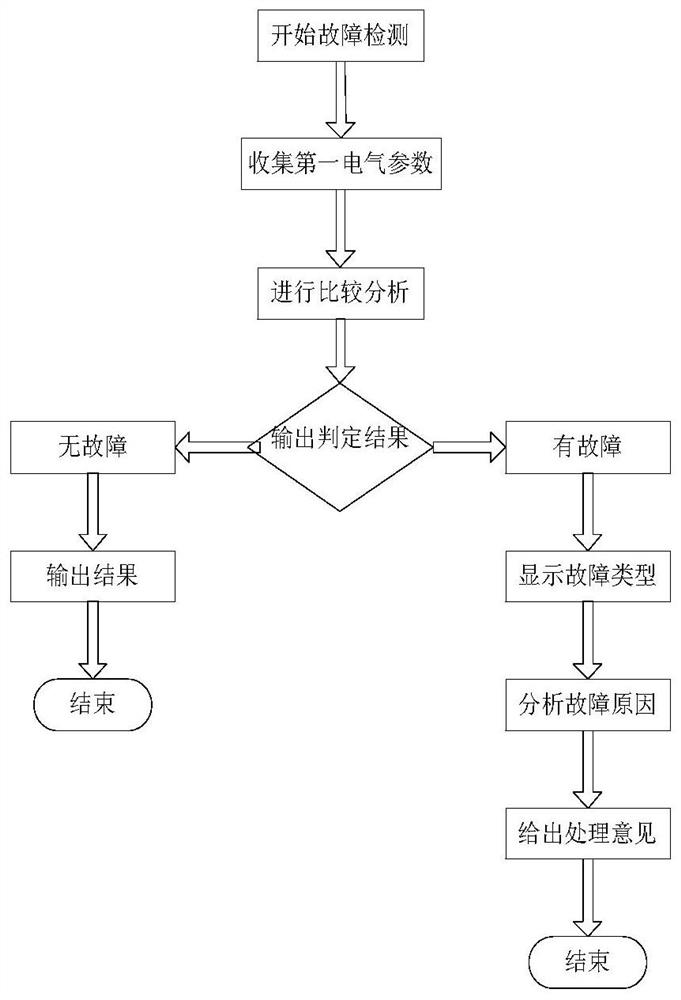
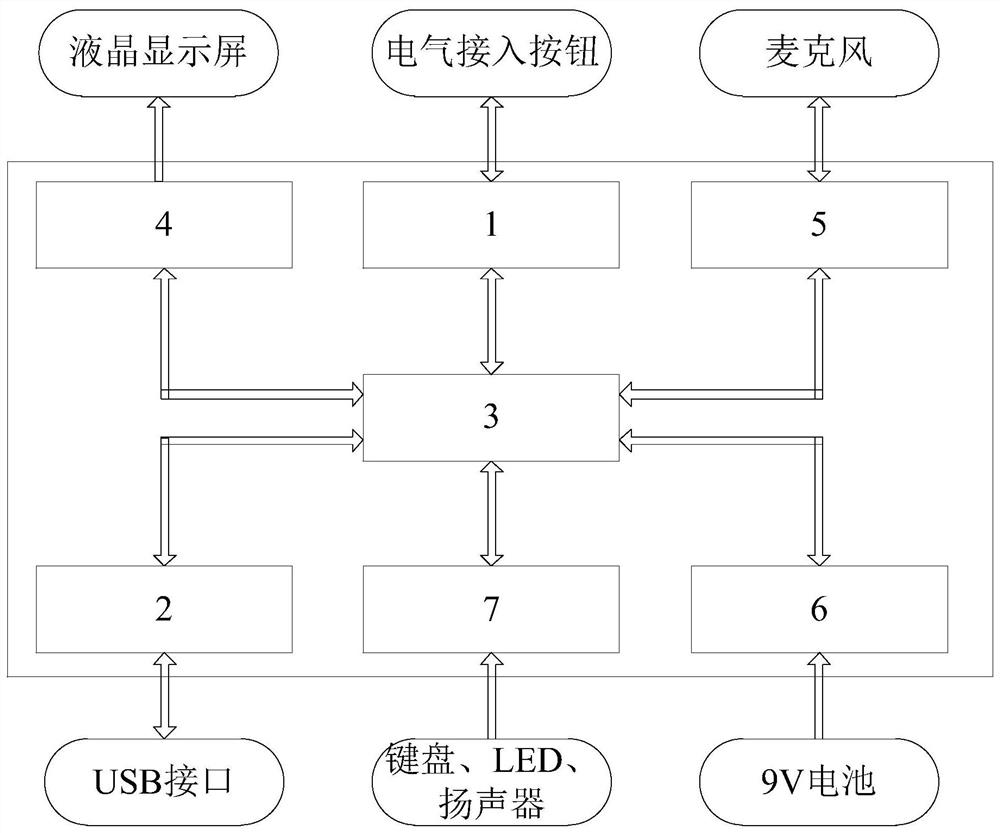
The invention discloses a fault detection device for a voice communication system, and the device comprises: an electrical detection assembly which is used for detecting a first electrical parameter of target equipment in the voice communication system; a memory which is used for storing a device parameter model set, wherein the equipment parameter model set comprises a normal parameter model and a plurality of fault parameter models corresponding to each piece of equipment; a central control assembly which is used for determining a target equipment parameter model corresponding to the target equipment according to the first electrical parameter, if the target equipment parameter model is a normal parameter model, sending first state information representing that the target equipment is normal to a display component; and if the target equipment parameter model is the fault parameter model, sending second state information representing the fault of the target equipment to the display component, wherein the second state information comprises a fault type, a fault reason and a processing suggestion of the target equipment. The fault detection device can significantly improve the troubleshooting efficiency of the voice communication system.
Owner:BEIJING SHOUGANG AUTOMATION INFORMATION TECH
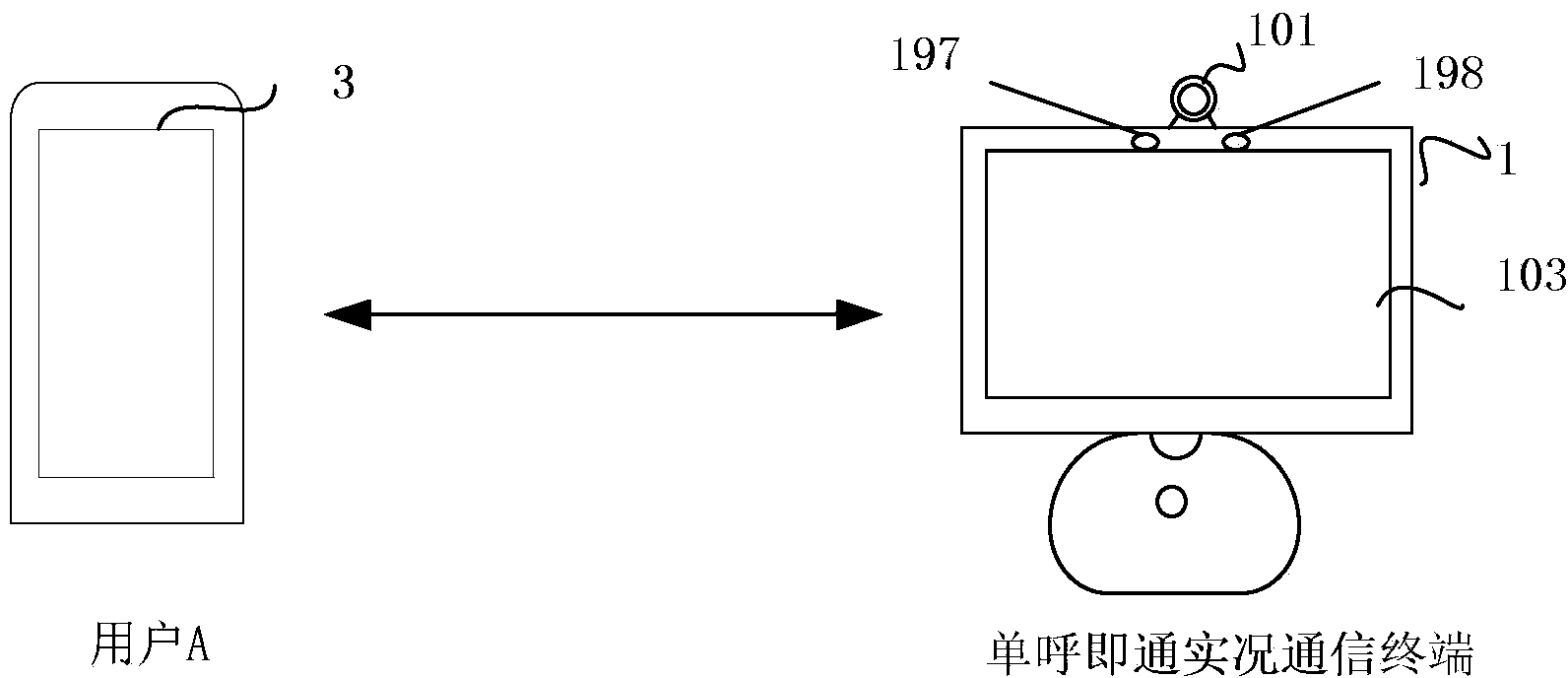
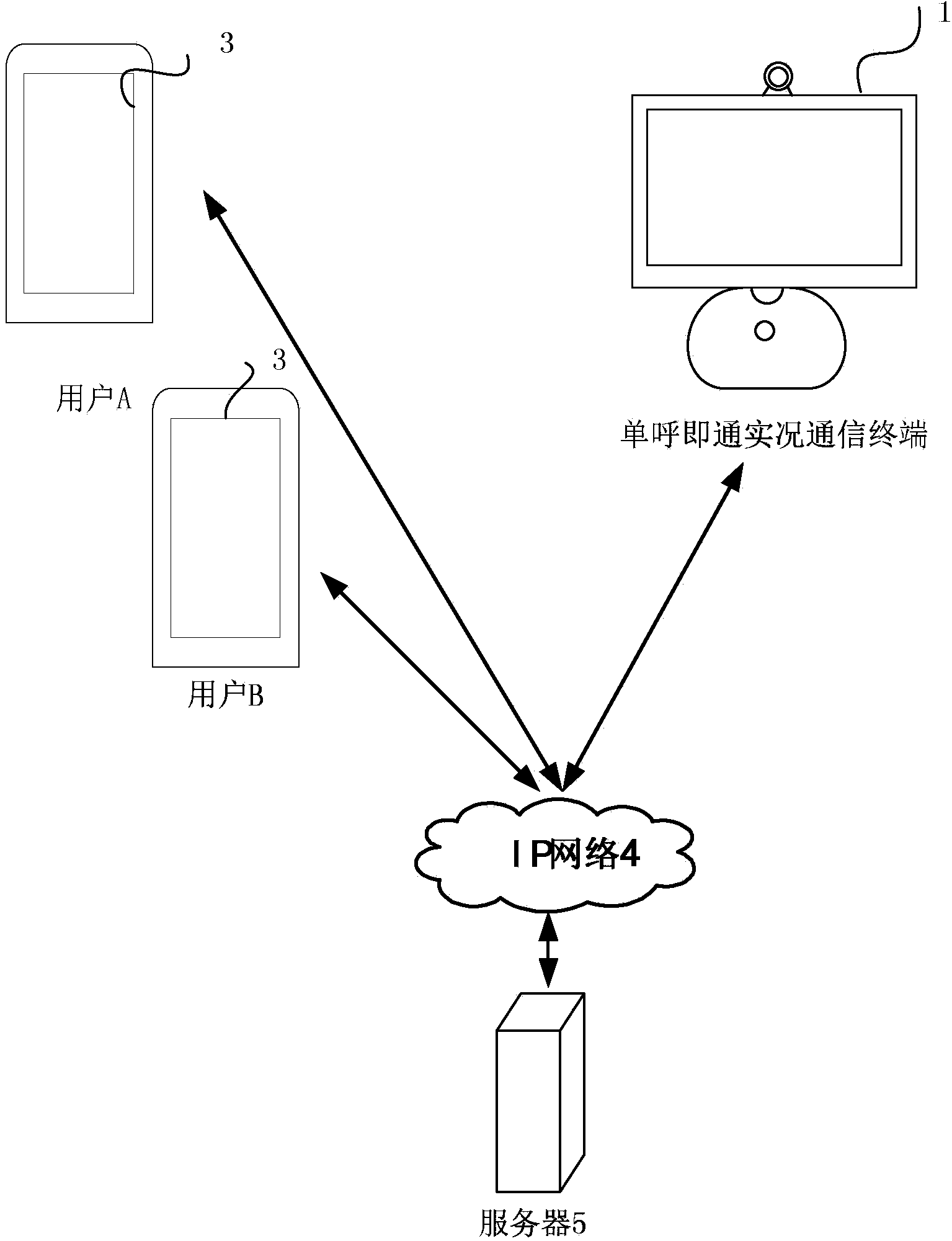
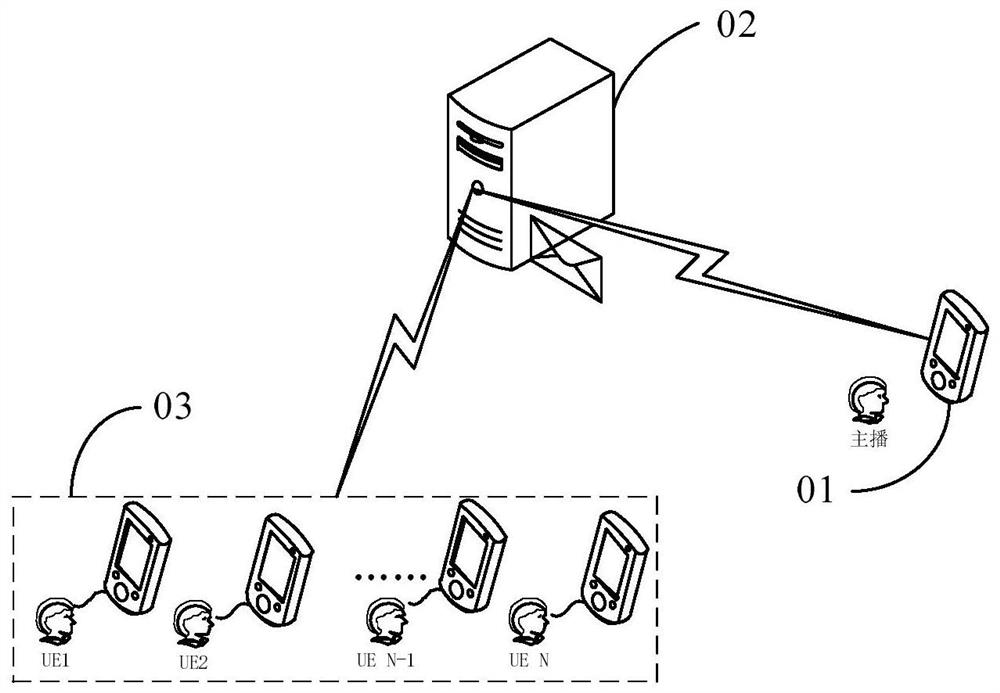
Live communication terminal capable of automatically carrying out bidirectional communication after unidirectional call, method and tool
InactiveCN104023207AImprove experienceFlexible displaySpeech analysisCharacter and pattern recognitionComputer terminalVoice frequency
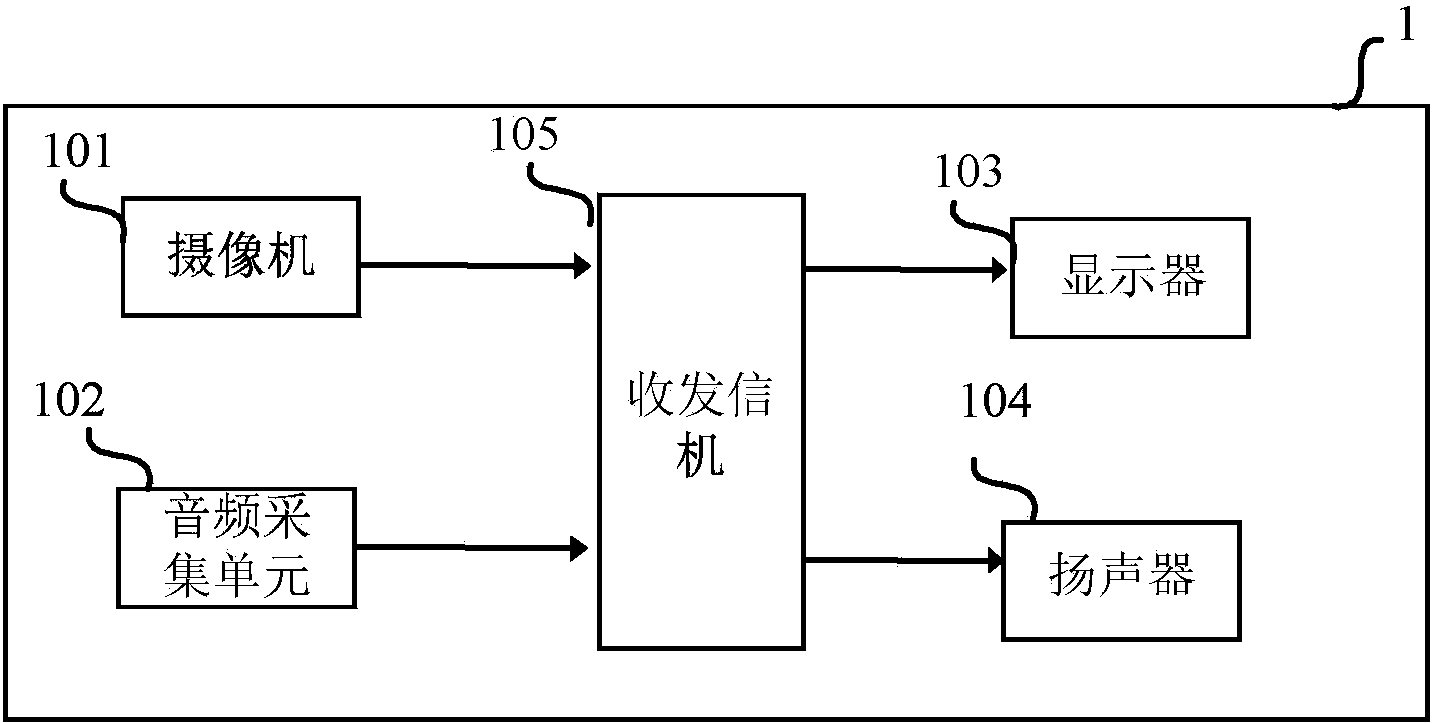
The invention discloses a live communication terminal capable of automatically carrying out bidirectional communication after a unidirectional call, a method and a tool installed on a mobile terminal, wherein the live communication terminal capable of automatically carrying out bidirectional communication after the unidirectional call receives a connection request from a credible user; the received connection request from the credible user is responded, and an answer for the connection request is automatically sent, so that IP (Internet Protocol) communication with the credible user is automatically established; the collected video frequency and voice frequency are transmitted to the credible user in the IP communication with the credible user, and the voice frequency from the credible user is at least received. In comparison with the prior art, the connection request of the credible user is automatically responded through the live communication terminal capable of automatically carrying out bidirectional communication after the unidirectional call, so that the interaction of the credible user at a monitoring end and a monitored end is enhanced, thus the communication experience of the user is improved.
Owner:AINEMO
3D modeling-based WLAN wireless network testing system
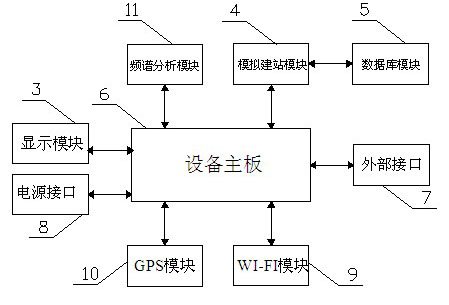
InactiveCN102131214BVersatileImprove business performanceWireless communicationWi-FiComputer Aided Design
The invention relates to a wireless local area network (WLAN) wireless network testing system, in particular to a three-dimensional (3D) modeling-based WLAN wireless network testing system. The system comprises a WLAN testing terminal (1) and a remote terminal (2), wherein the WLAN testing terminal (1) comprises an equipment motherboard (6), and a display module (3), a wireless fidelity (WI-FI) module (9), an external interface (7) and a power supply (8) which are connected with the equipment motherboard (6); the WLAN testing terminal (1) is in communication connection with the remote terminal (2) through the WI-FI module (9); a 3D analog station construction module (4) is connected to the equipment motherboard (6); and the 3D analog station construction module (4) is connected with a database module (5). According to the technical scheme, the WLAN wireless network testing system can perform 3d browsing, intuitively, attractively and intelligently identify computer aided design (CAD) drawings, and automatically analyzes the simulated effect; the function of the WLAN wireless network testing system is enriched; and the comprehensive service capacity of the WLAN wireless network testing system is improved.
Owner:ZHEJIANG SAFE COMM EQUIP
Tunnel connection request distribution method and device
ActiveCN102917071ANo manual intervention requiredIntelligent RecognitionTransmissionLonWorksNetwork address translation
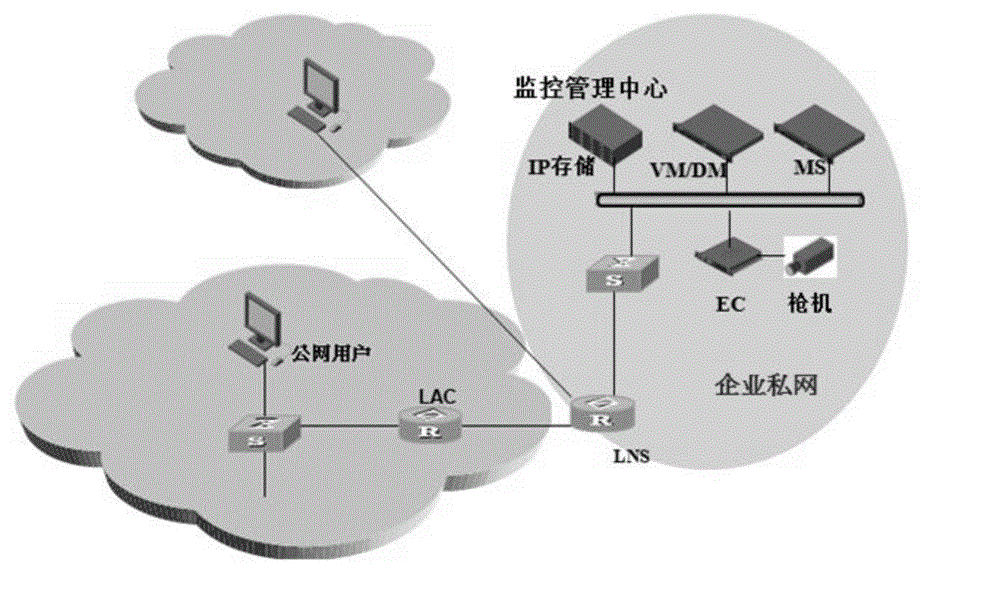
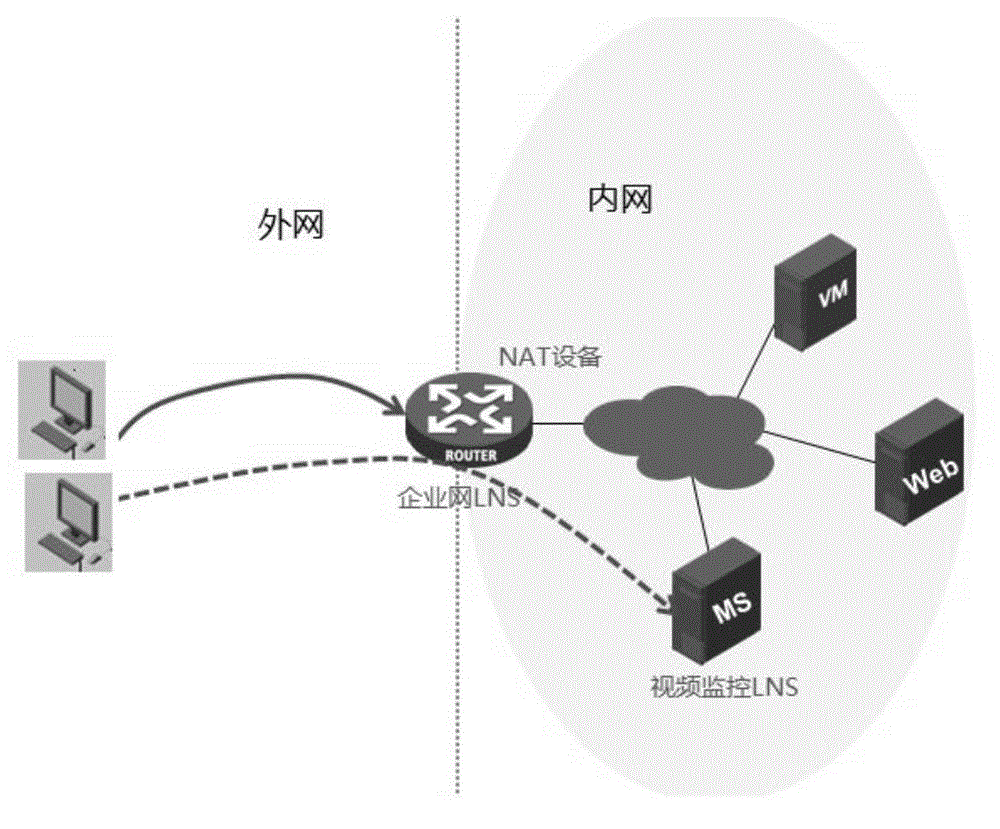
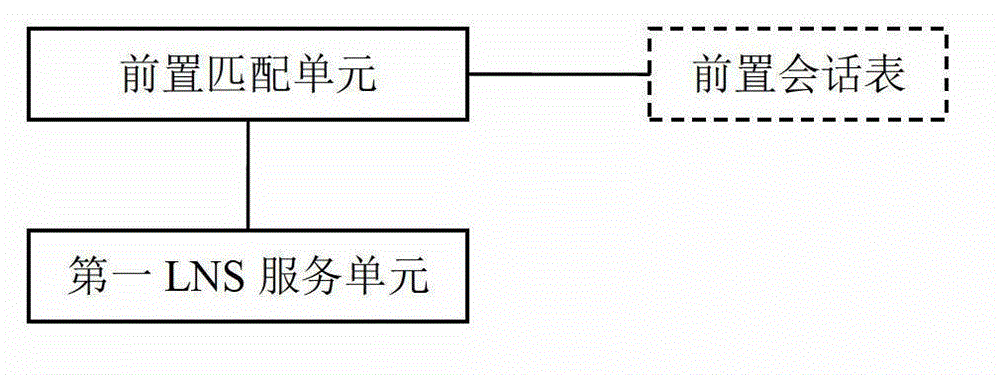
The invention provides a tunnel connection request distribution method which is applied to an NAT (Network Address Translation) gateway to dispatch an L2TP connection request from a user outside the NAT gateway. The method comprises the steps of judging whether an L2TP connection request message from the user requires local authentication according to a preset policy, conducting local processing if required, otherwise returning an authentication failure message to the user, storing session characteristics of the authentication failure message in a session table when the authentication failure message is received, acquiring the session characteristics of a request message when the request message is received subsequently, and searching whether the preposed session table contains a corresponding table entry according to the session characteristics, and forwarding the message to an LNS (Lonworks Network Service) server in the NAT gateway if the table contains the entry, otherwise locally processing the L2TP connection request message. A service network served by the LNS server is different from a local service network. According to the tunnel connection request distribution method, the objective LNS server to which the user is intended to access can be identified intelligently while the existing standard protocol is followed.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
Data processing method and device
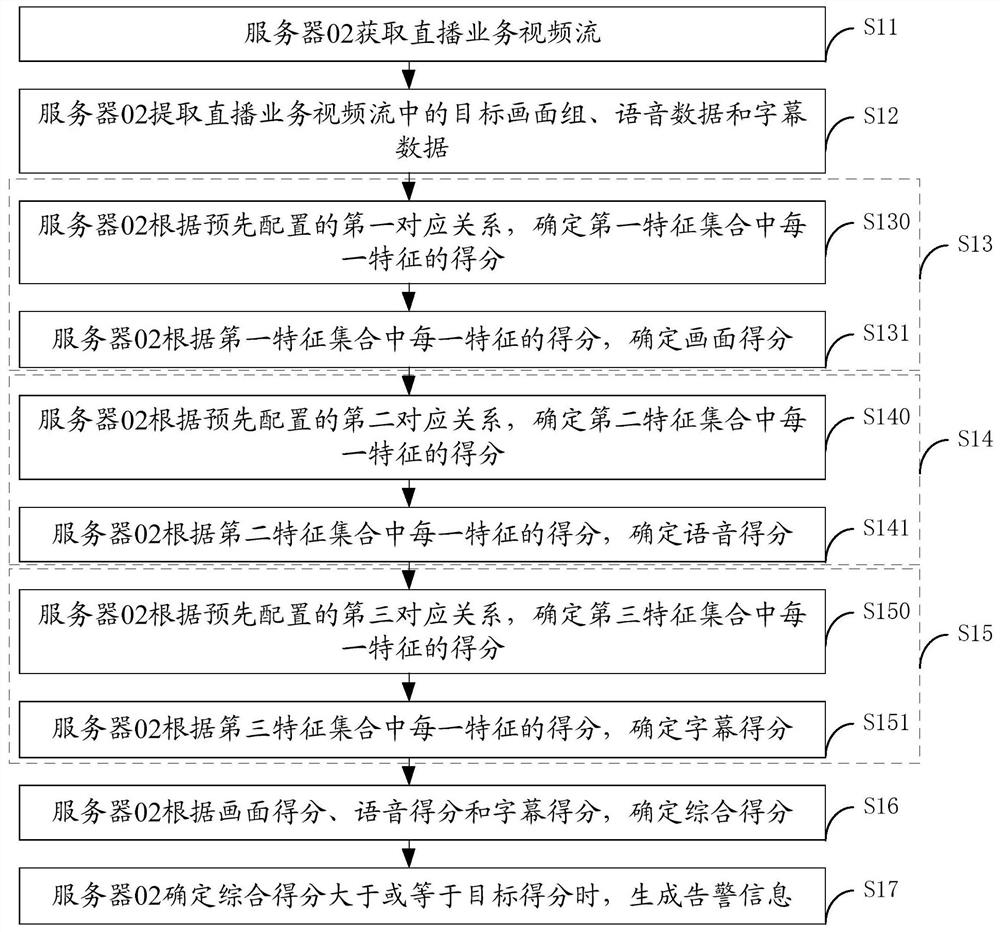
ActiveCN114697687AImprove review efficiencyLabor savingSelective content distributionEnergy efficient computingFeature setData mining
The invention provides a data processing method and device, relates to the technical field of data processing, and solves the problem of how to more intelligently identify whether the content live broadcast in a live broadcast room is regular and legal. The method comprises the following steps: acquiring a live broadcast service video stream; extracting a target picture group, voice data and subtitle data in the live broadcast service video stream; determining a picture score according to a first feature set contained in the target picture group; determining a voice score according to a second feature set contained in the voice data; determining a subtitle score according to a third feature set contained in the subtitle data; determining a comprehensive score according to the picture score, the voice score and the subtitle score; when determining that the comprehensive score is greater than or equal to the target score, generating alarm information; wherein the alarm information is used for indicating that the live broadcast service video stream is abnormal.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Contact network suspension operating state intelligent detection system
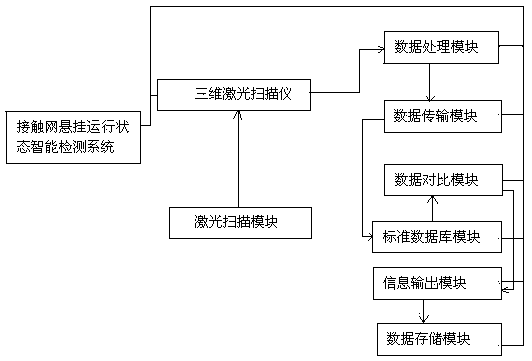
PendingCN110244320AFind problems in timeAll-in-one installationOptical rangefindersElectromagnetic wave reradiationContact networkControl system
The invention discloses a contact network suspension operating state intelligent detection system. The contact network suspension operating state intelligent detection system comprises a three-dimensional laser scanner and a laser scanning module, and further comprises a data processing module, a data transmission module, a data comparison module, a standard database module, an information output module and a data storage module; the data processing module, the data transmission module, the data comparison module, the standard database module, the information output module, and the data storage module are application software installed in a PC; the laser scanning module is a built-in control system of the three-dimensional laser scanner; and the PC is integrated into an inspection repair vehicle and can also be installed in a power supply section. The contact network suspension operating state intelligent detection system can perform intelligent identification and intelligent judgment, can quickly and accurately identify the operating states of various parts of the system, and can discover the problematic part in advance and process the problematic part in time; therefore, the occurrence of driving safety accidents is avoided, and meanwhile, the labor intensity of the detecting personnel is greatly reduced, the detection efficiency is improved, the accuracy of the detection is improved, and a guarantee for driving safety is provided.
Owner:四川艾德瑞电气有限公司
Method and device for dispatching TCP data stream
ActiveCN101616098BIntelligent RecognitionAvoid attackData switching networksOperating systemNetwork router
The invention discloses a method and a device for dispatching TCP data stream, which can intelligently identify small-sized message data stream based on the technology of session management of the small-sized message data stream, meet the priority dispatching requirement of small-sized message, can intelligently identify the small-sized message data stream on a full-network router, simultaneouslyavoid being attacked, and further carry out priority dispatching for random specific message type according to the technical ideas of the invention.
Owner:NEW H3C BIG DATA TECH CO LTD
Early warning method and device
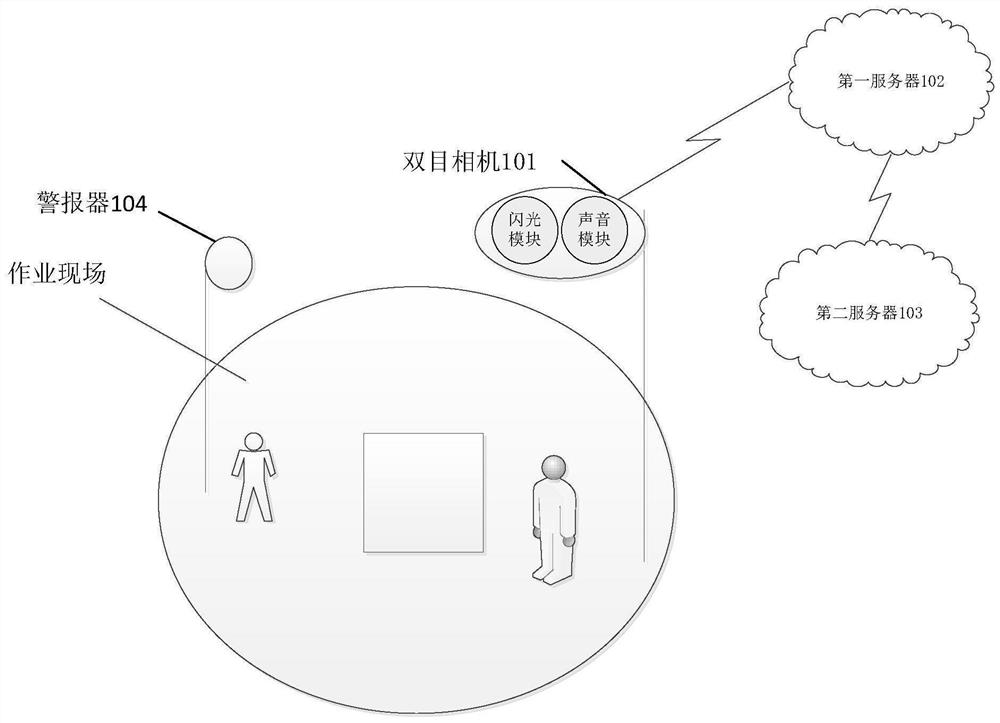
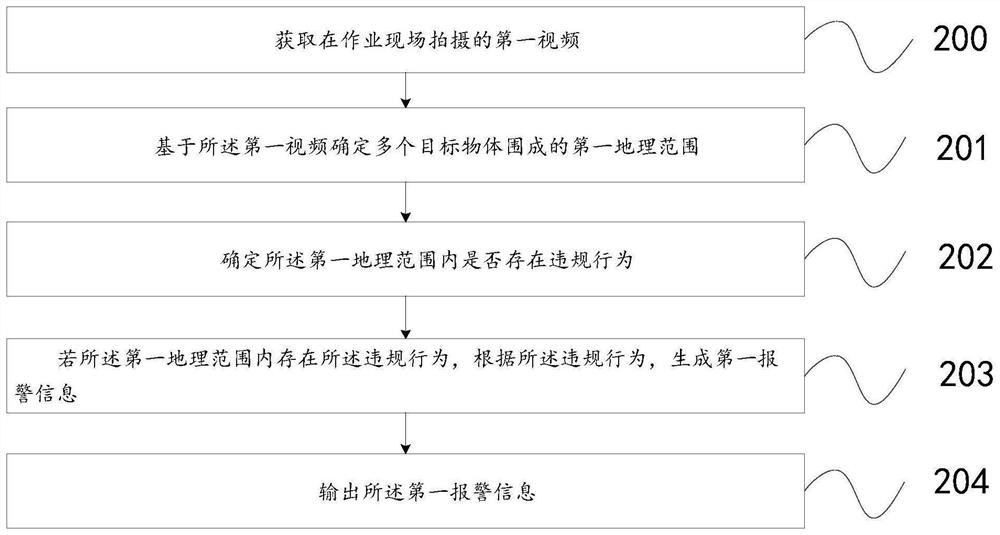
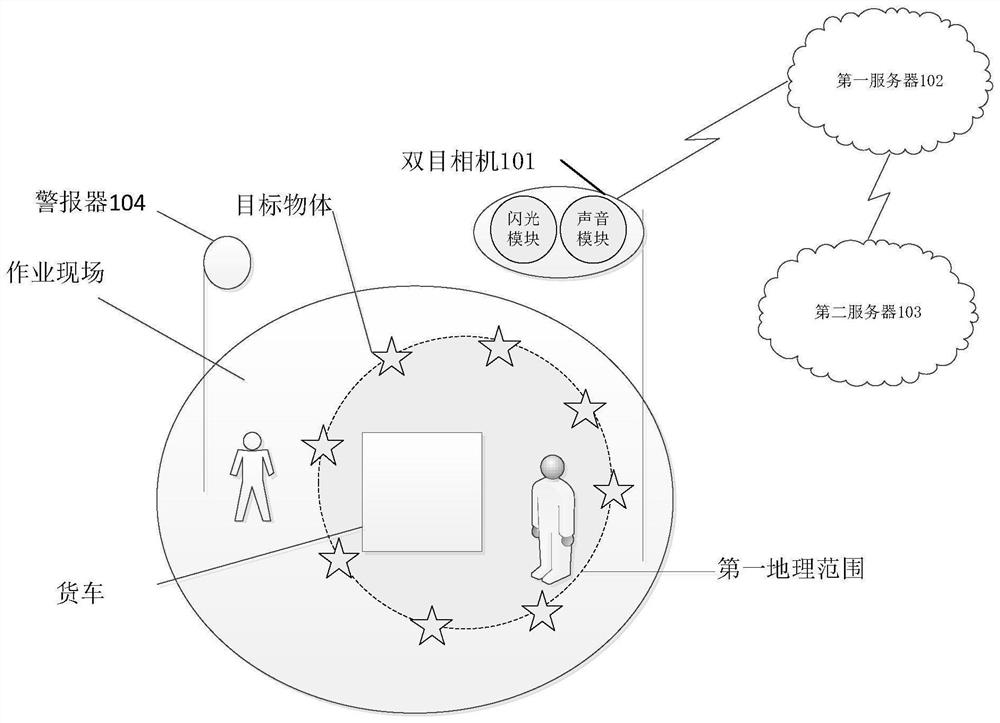
InactiveCN112037451AIntelligent RecognitionImprove efficiencyBurglar alarm short radiation actuationAlarm messageBehavior recognition
The invention provides an early warning method and a device. The method comprises the following steps: acquiring a first video shot at an operation site; determining a first geographical range definedby a plurality of target objects based on the first video, wherein the first geographical range is an operation area in the operation site, and the target objects are specific objects used for surrounding the operation site; determining whether a violation behavior exists in the first geographical range or not; if the violation behavior exists in the first geographical range, generating first alarm information according to the violation behavior; and outputting the first alarm information. By means of the method, the violation behavior of the operation site can be intelligently recognized, early warning is conducted in time on the operation site, and the violation behavior recognition efficiency and the violation behavior early warning real-time performance are improved.
Owner:ZHEJIANG DAHUA TECH CO LTD
Conversational natural language processing method and device
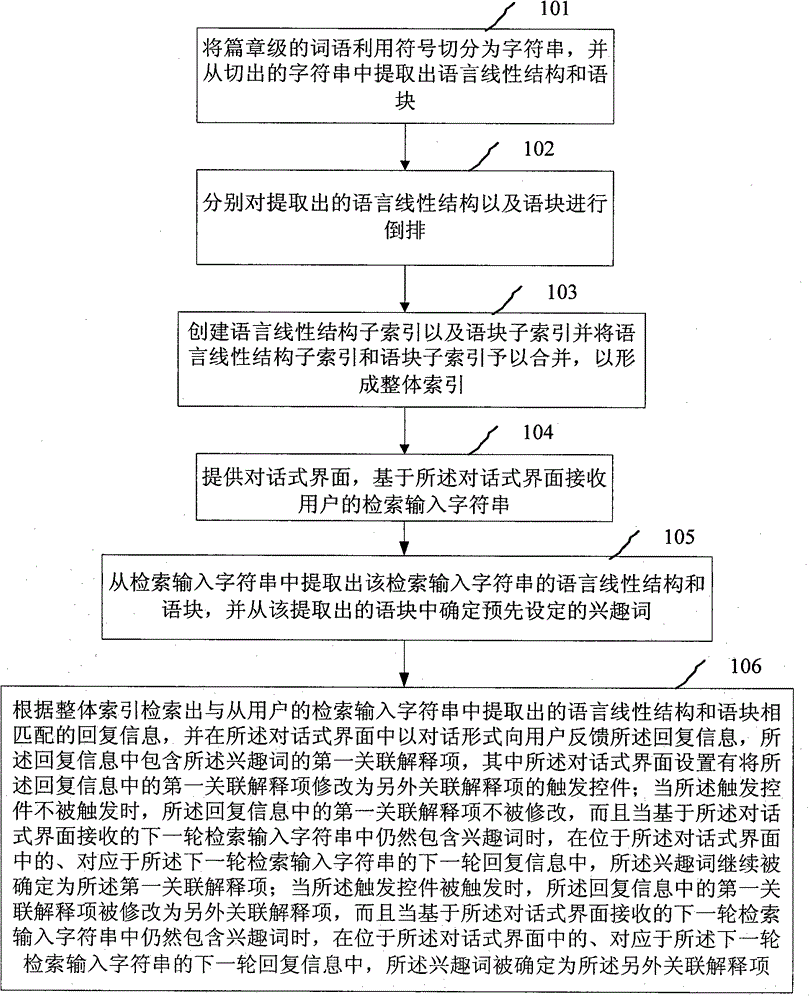
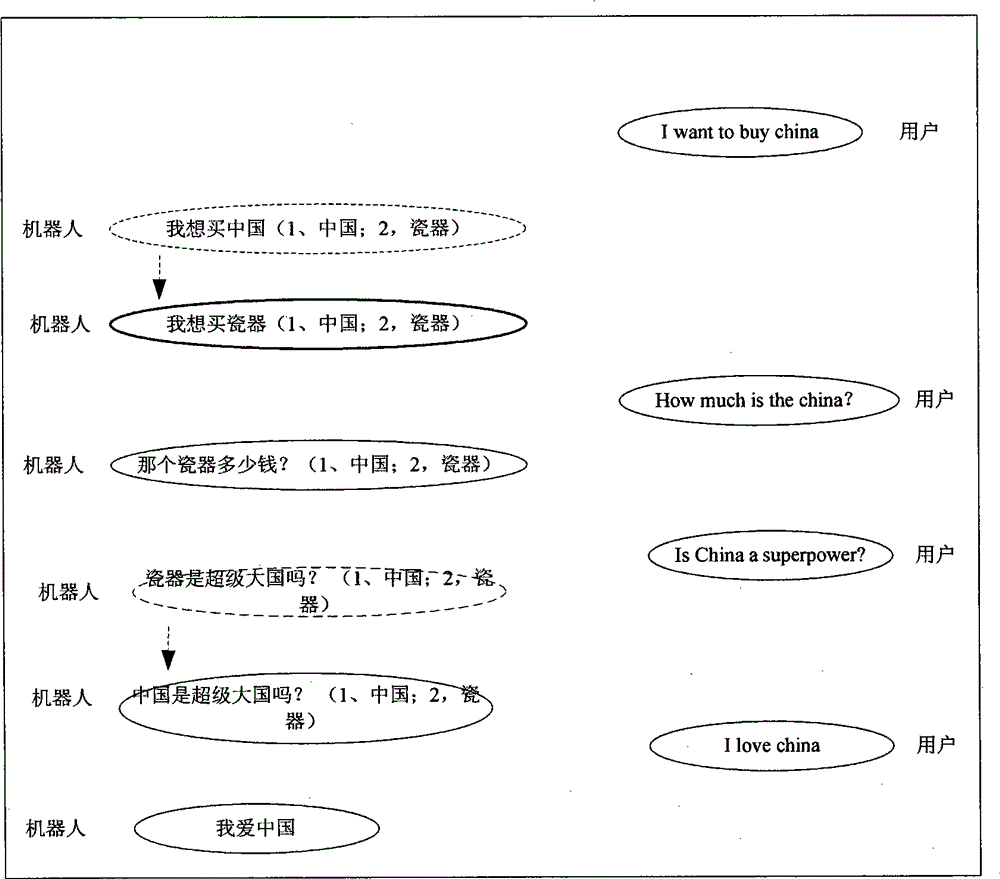
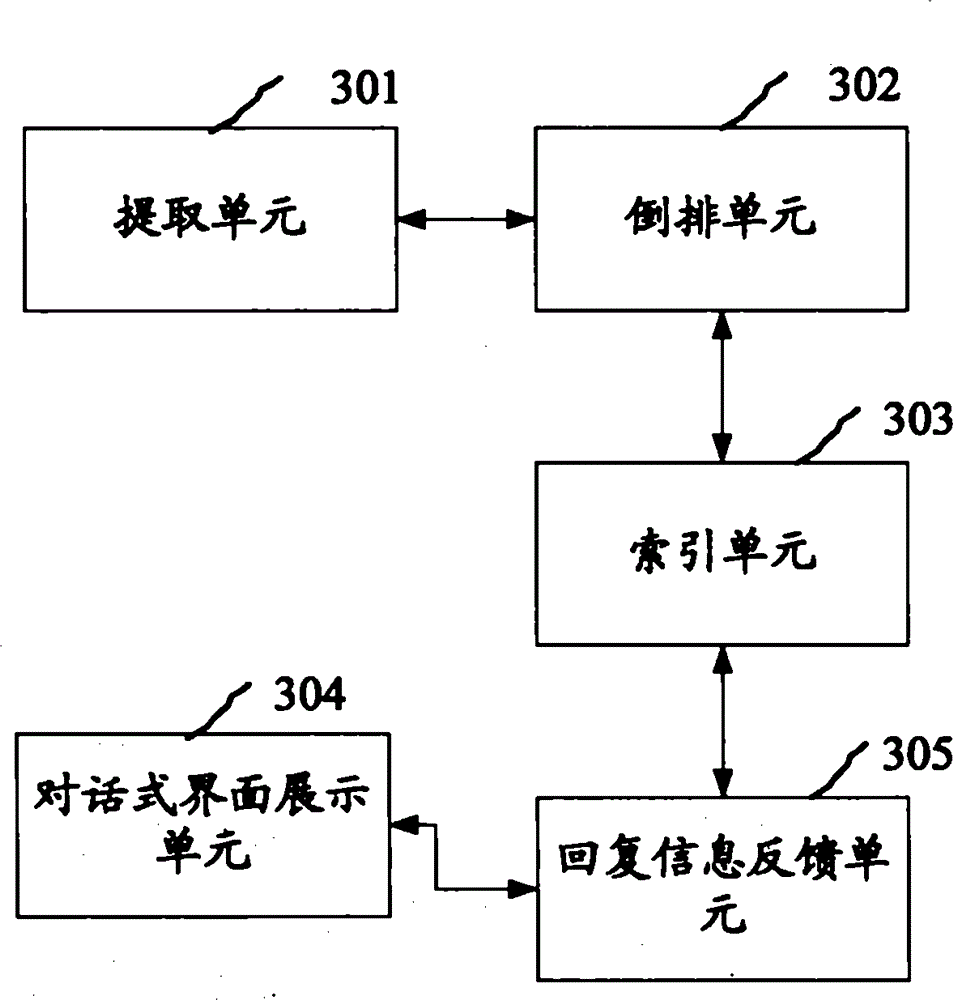
InactiveCN105488035AIntelligent RecognitionImprove processing accuracySpecial data processing applicationsProcessing accuracyHuman language
The invention discloses a conversational natural language processing method and device. The method comprises the following steps: segmenting chapter-level words into a character string by utilizing symbols, extracting language linear structures and language chunks from the segmented character string, respectively carrying out inverted arrangement on the extracted language linear structures and language chunks, creating sub-indexes of the language linear structures and the language chunks and forming a holistic index; providing a conversational interface and receiving a retrieve input character string of a user on the basis of the conversational interface; extracting the language linear structure and the language chunk of the retrieve input character string from the retrieve input character string and confirming a preset interest word from the extracted language chunk; and retrieving reply message matched with the language linear structure and the language chunk which are extracted from the retrieve input character string of the user according to the holistic index. By applying the method disclosed by the invention, the correlation interpretant of the interest word in the next round of conversation is confirmed through memorizing the trigger operation of a trigger control, so that the natural language processing accuracy is increased.
Owner:陈伯妤
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com