Attack-aware mMTC slice resource allocation method and apparatus, and electronic device
A resource allocation device and attack-aware technology, applied in the field of device and electronic equipment, attack-aware mMTC slice resource allocation method, can solve the problems of single-point attack, low delay sensitivity, difficult to find and take defensive measures, etc. The effect of mitigating DDoS attacks and ensuring network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
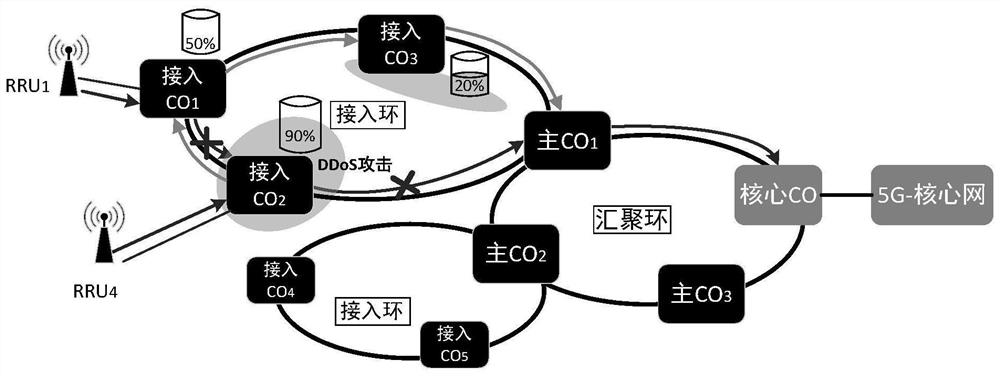
[0073] Such as figure 2 As shown, a group of IoT devices totaling 1,000 are randomly connected to the network through the base station, 300 of which are directly connected to the CO1 node for processing at RRU1, and 700 are directly connected to the CO2 node for processing at RRU4. , the access CO2 node and the access CO2 node belong to the same primary CO. Set the resource utilization thresholds of the access CO and the main CO to 80%, and set the waiting time period to 5s. When some of the 1,000 IoT devices are attacked by DDoS and become controlled zombie devices, the resource utilization rate of access to CO1 nodes becomes 50%, and the resource utilization rate of access to CO2 nodes becomes 90%. The resource utilization rate of the node exceeds the preset threshold. At this time, it is considered that there is a risk of a DDoS attack on the access CO2 node, and the service offloading plan for the access CO2 node is started. First, other available access CO2 nodes on the...
Embodiment 2
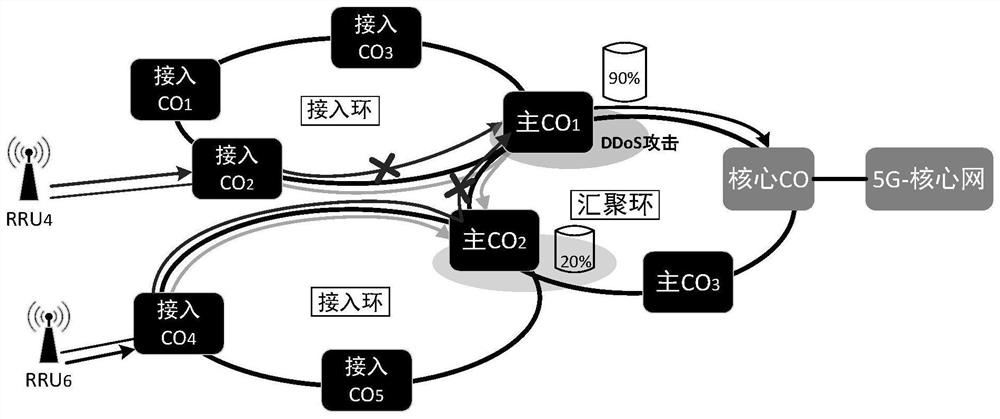
[0075] Such as image 3 As shown, a group of 1,000 IoT devices randomly access the network through the base station, 300 of which are directly connected to the CO2 node at RRU4, and 700 are directly connected to the CO4 node at RRU6. Set the resource utilization thresholds of the access CO and the primary CO to 80%. The access CO2 node and the access CO4 node belong to different primary COs, namely primary CO1 and primary CO2. Concentrate on the master CO1 with the lowest comprehensive transmission traffic consumption to implement request processing. Similarly, when it is attacked by DDoS, the resource utilization rate of the master CO1 becomes 90%, which exceeds the preset threshold. In the business offloading scheme, firstly, among other available main CO nodes on the convergence ring, the main CO2 node with the lowest resource utilization rate (its resource utilization rate is 20%) is selected to implement request processing.
[0076] In another case, if no available prim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com