Resource access control method, system and device, equipment and medium
A technology of resource access and control methods, applied in the field of devices, electronic equipment and storage media, resource access control methods, and systems, capable of solving problems affecting application performance and increasing pressure on databases, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
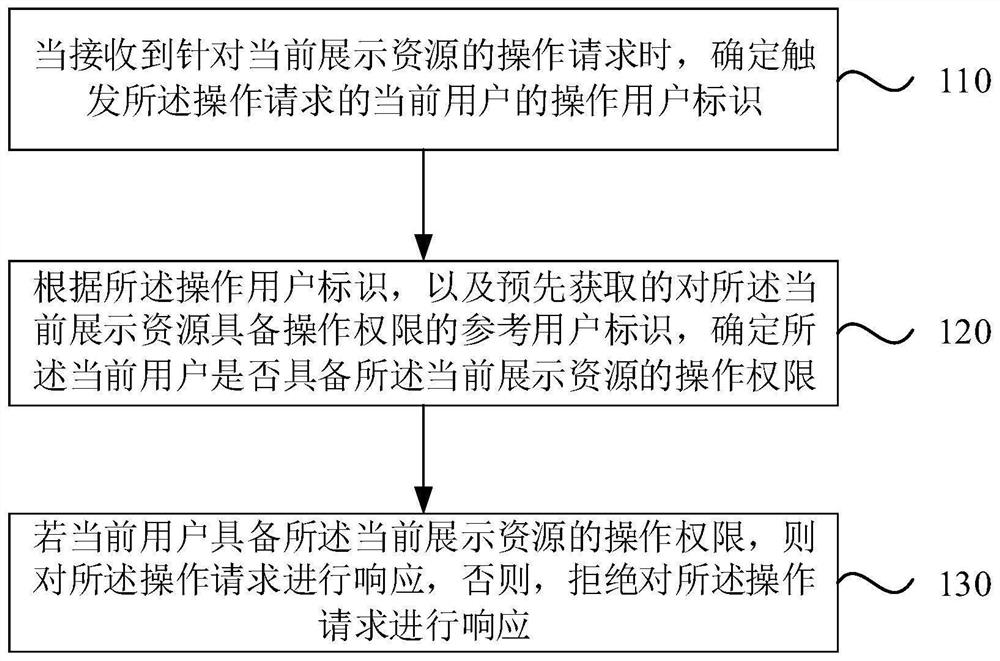
[0041] figure 1 It is a flow diagram of a resource access control method provided by Embodiment 1 of the present invention. This method is applicable to when a Web application requests resources from a server, and the server checks the requester's access rights to prevent requests without access rights from The emergence of unauthorized access to resources. The resource access control method can be executed by a resource access control device, and the device can be implemented in the form of software and / or hardware.
[0042] like figure 1 As shown, the resource access control method provided in this embodiment includes the following steps:
[0043] Step 110: When receiving an operation request for the currently displayed resource, determine the operating user identifier of the current user who triggers the operation request.
[0044]Wherein, the currently displayed resource may specifically be an article displayed on a terminal interface, or an operation page of a specific...
Embodiment 2
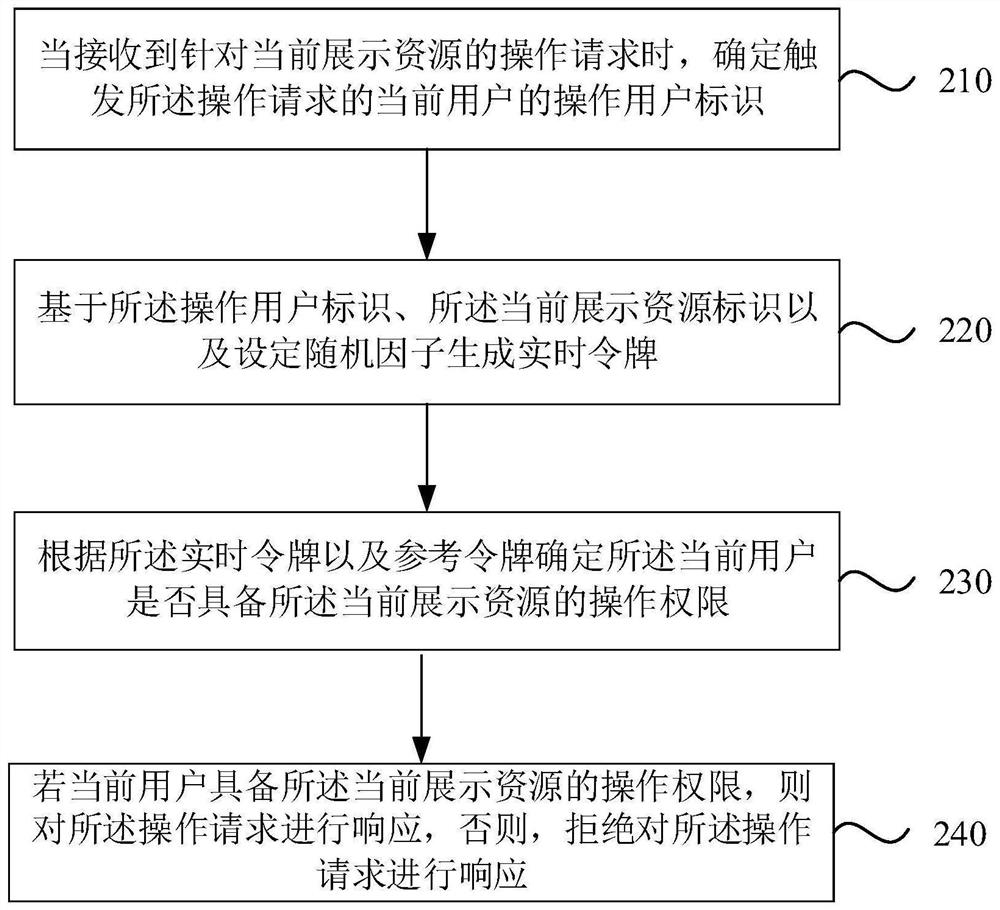
[0061] figure 2 It is a schematic flowchart of a resource access control method provided in Embodiment 2 of the present invention. On the basis of the above embodiments, this embodiment further optimizes the solution, specifically for the above step 120 "according to the operating user ID and the pre-acquired reference user ID with operation authority on the current display resource, Determining whether the current user has the operation authority of the current display resource" provides an optional implementation manner. Wherein, the same or similar descriptions will not be repeated in this embodiment, and relevant explanations of the foregoing embodiments may be referred to.
[0062] like figure 2 As shown, the resource access control method includes the following steps:
[0063] Step 210: When receiving an operation request for the currently displayed resource, determine the operating user identifier of the current user who triggers the operation request.
[0064] St...
Embodiment 3
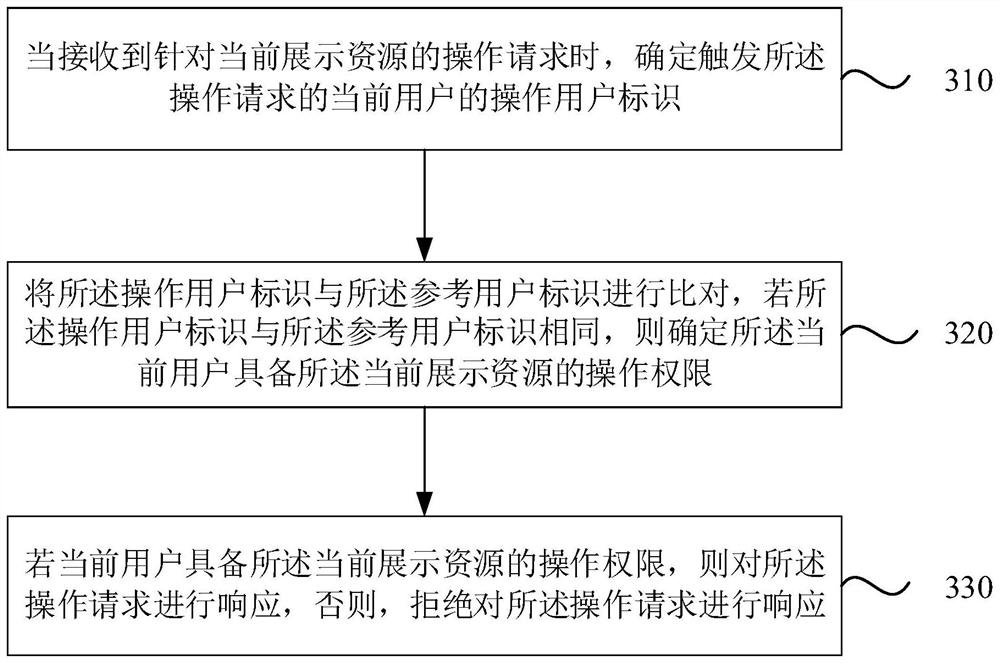
[0083] image 3 It is a schematic flowchart of a resource access control method provided in Embodiment 2 of the present invention. On the basis of the above embodiments, this embodiment further optimizes the solution, specifically for the above step 120 "according to the operating user ID and the pre-acquired reference user ID with operation authority on the current display resource, Determining whether the current user has the operation authority of the currently displayed resource" presents another optional implementation manner. Wherein, the same or similar descriptions will not be repeated in this embodiment, and relevant explanations of the foregoing embodiments may be referred to.
[0084] Such as image 3 As shown, the resource access control method includes the following steps:
[0085] Step 310: When receiving an operation request for the currently displayed resource, determine the operating user identifier of the current user who triggers the operation request.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com