Sandbox-based inherent data protection method and system
A data protection and sandbox technology, applied in digital data processing, platform integrity maintenance, program control design, etc., can solve problems such as high cost and inability to actually solve the problem of acquiring and tracking and identifying user identity of inherent data of terminal equipment. , to achieve the effect of data security and reliability, ensuring data isolation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
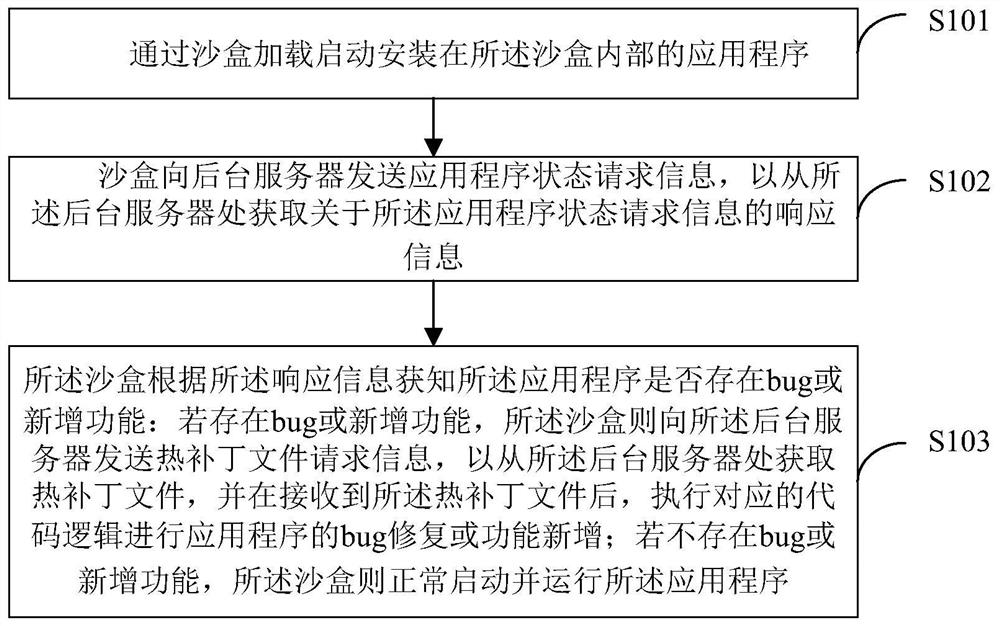
[0054] Such as figure 1 As shown, the present invention proposes a sandbox-based inherent data protection method, comprising the following steps:
[0055] S101: Install a sandbox on the terminal device, install an application program inside the sandbox, and start the application program installed inside the sandbox by loading the sandbox;
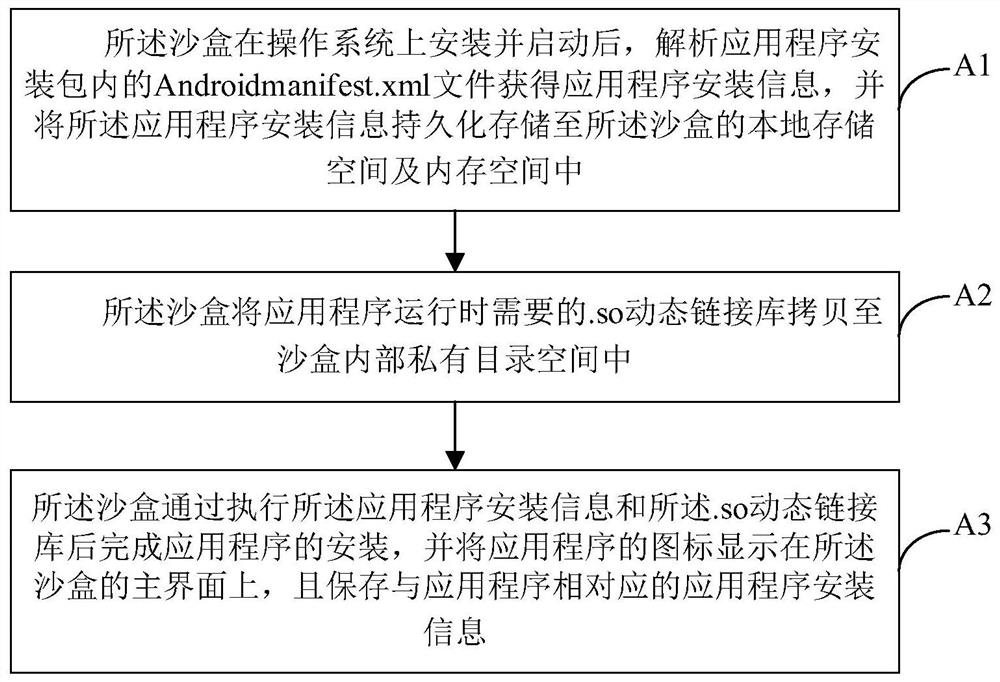
[0056] Specifically, as a third-party application, the sandbox must be installed on the terminal device before it can run. As a security sandbox, the sandbox has its own closed private space and must have applications running in the sandbox, so running in The applications in the sandbox must be installed inside the sandbox, so as to ensure that the content belonging to the application only exists inside the sandbox and will not be accessed by applications outside the sandbox, and the data inside and outside the sandbox are isolated , making sandbox data safe and reliable.
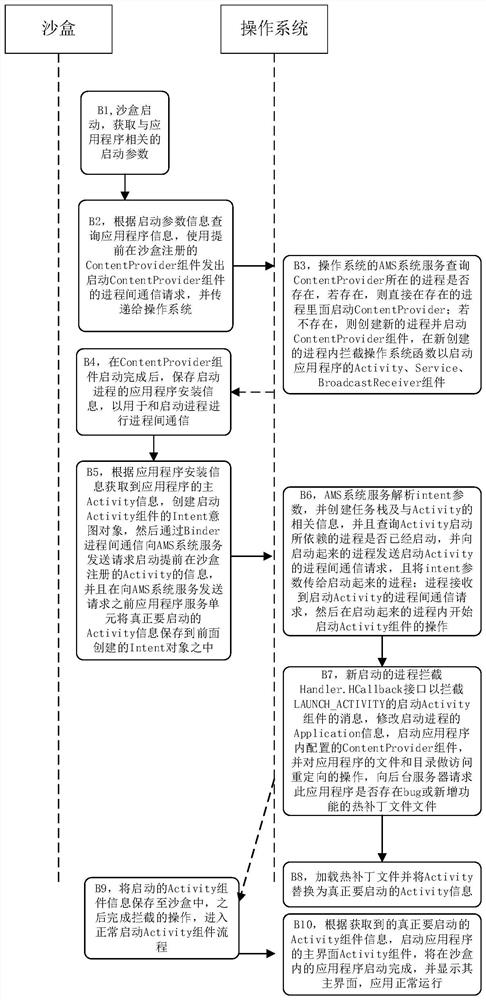
[0057] S102: When the application program inside the sandbox obta...
Embodiment 2
[0063] On the basis of the above-mentioned embodiment, the difference from the above-mentioned embodiment is that in the embodiment of the present invention, the sandbox uses the Java reflection technology and the set dynamic proxy method to call the virtual device information service to generate information about the first The first virtual data of the inherent data specifically includes:
[0064] Java reflection technology is adopted in the application program inside the sandbox, so that the application program is transferred to the dynamic proxy method provided when obtaining the first intrinsic data of the terminal device;
[0065] calling a virtual device information service set in the sandbox by using an inter-process communication mechanism through a dynamic proxy method to generate first virtual data about the first inherent data, and returning the first virtual data to the dynamic proxy method;
[0066] An application program inside the sandbox obtains the first virtu...
Embodiment 3
[0070] On the basis of the above-mentioned embodiments, the difference from the above-mentioned embodiments is that in the embodiments of the present invention, the first information about the second inherent data is generated by loading the system information class through the sandbox and using the Java reflection technology. 2. Virtual data, specifically including:
[0071] During the process startup process of the application program inside the sandbox, the system information class of the terminal device is loaded through the sandbox, and then the static member variables of the second inherent data of the system information class are replaced and protected by using Java reflection technology Second dummy data is generated with respect to the second intrinsic data.
[0072] Specifically, when the method of the present invention is not used, that is, under normal circumstances, a third-party application program running on a terminal device directly calls the static member var...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com