High-efficiency safe multi-party computing method
A secure multi-party computing, high-efficiency technology, applied in the field of high-efficiency and secure multi-party computing, can solve problems such as low efficiency, achieve the effect of protecting privacy, ensuring data security, and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
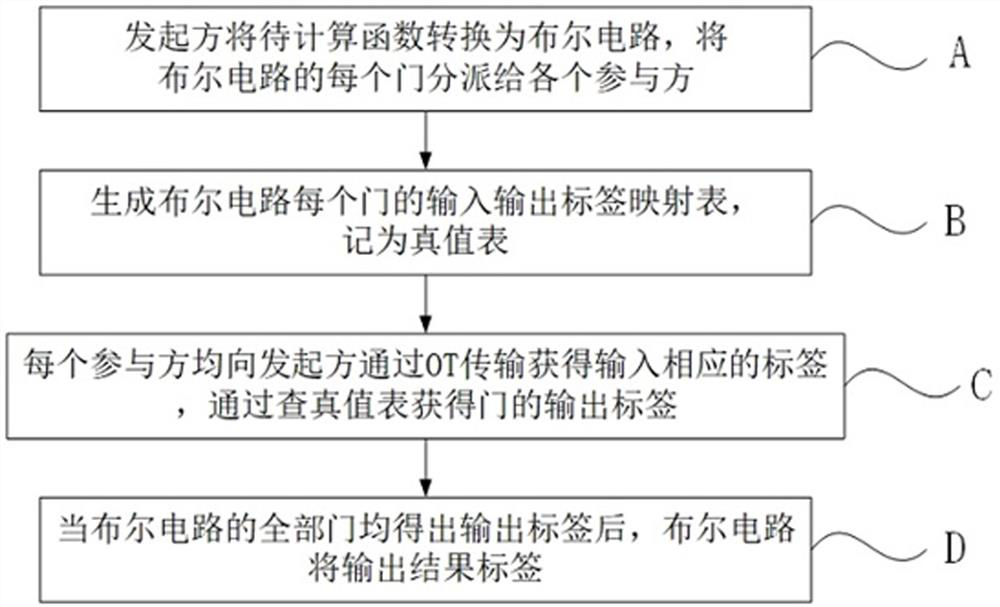
[0023]A high-efficiency safety multi-party calculation method for multi-party calculations with N participants, initiating the participant of security and multi-party calculations, and the initiator will sort the rest of the participants, please refer tofigure 1 This embodiment includes the following steps:
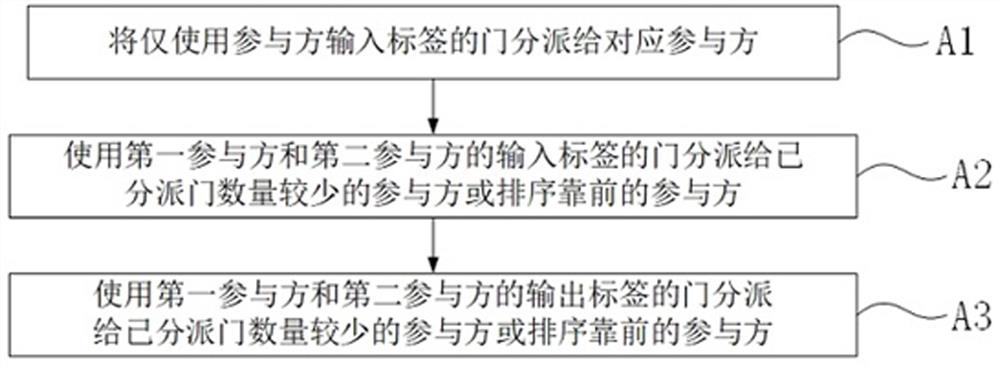
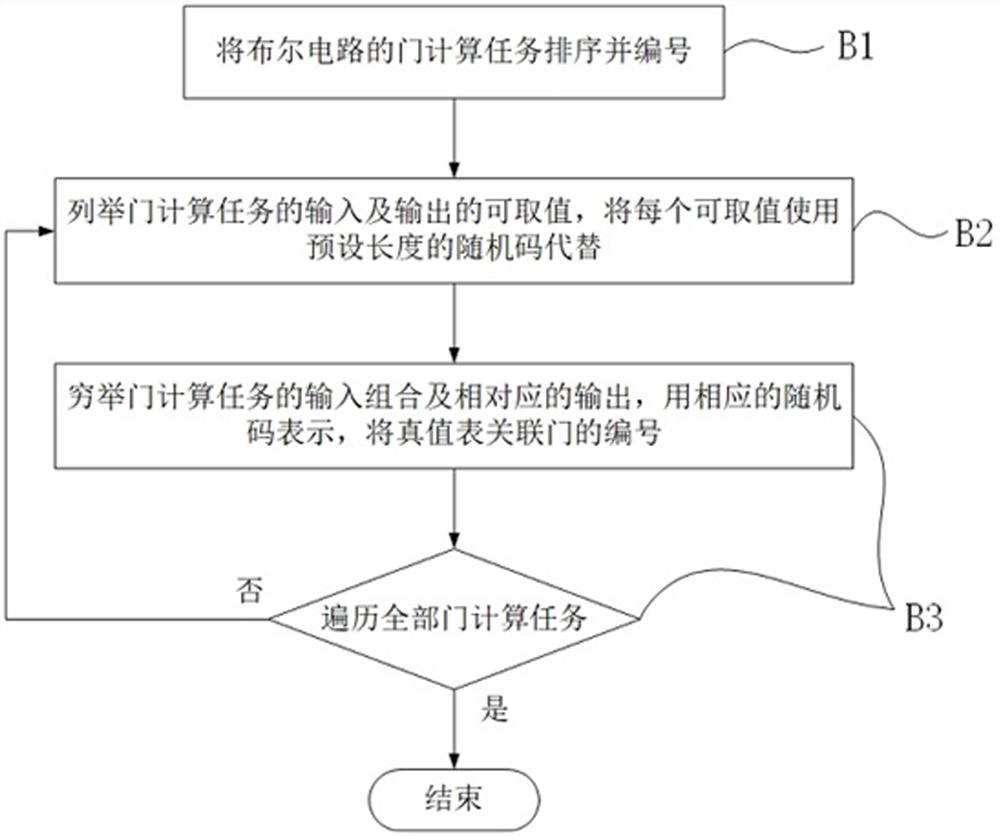
[0024]Step a) The initiator will be calculatedConvert to Boolean circuit,ParticipantInput, initiator Boolean circuitEach door is assigned to each participant.
[0025]In theory, any function can be converted to a Boolean circuit, that is, the Boolean circuit can implement the calculation of complex functions. For example, the rule function of the electronic election is to be calculated, converted to the Boolean circuit., Each participant will vote for the Boolean value of the candidate., Final Boolean circuitWhether the current candidate is successfully selected as a result. You can also convert the summary function to the Boolean circuit, and each participant converts its own sales ...
Embodiment 2
[0043]A high efficiency safety multi-party calculation method, this embodiment has been further improved relative to Examples, and in Example No. 1, the participant needs to bePerform credible contract restrictions to generate and transfer encryption codingAfter, the encryption code will be encrypteddelete. In this embodiment, another embodiment is used, and the participation is improved.Do not save encryption coding Credibility. In this embodiment, the participantGenerate encryption codingAfter, the encryption code will be encryptedAnd the corresponding marking random numberSend to the participant,participantsAccording to the number of random numbersWill march the random numberMedium bit value 0 correspondenceThe bit value is randomly changed, and the random numberMedium-bit value 1 correspondenceBit value does not work, will change the encryption code after the changeSend it to the initiator. Due to participantsI don't know more, so I can't learn any useful information, and only t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com