Trusted cryptographic module security management method and system
A cryptographic module and security management technology, applied in computer security devices, electronic digital data processing, instruments, etc., can solve the leakage of key security parameters in the module, the lack of a perfect management system for multiple types of keys, and the existence of trusted cryptographic modules. Security and other issues, to achieve the effect of improving credibility, generating security, and achieving encryption protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
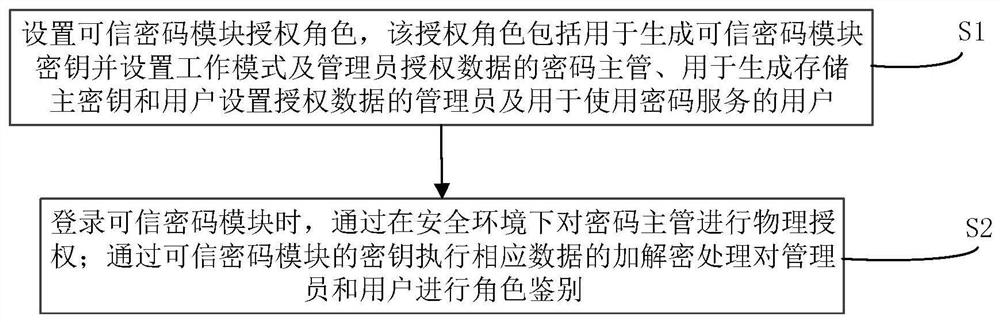
[0034] Embodiment of the present invention, see figure 1 As shown, a trusted cryptographic module security management method is provided, including:
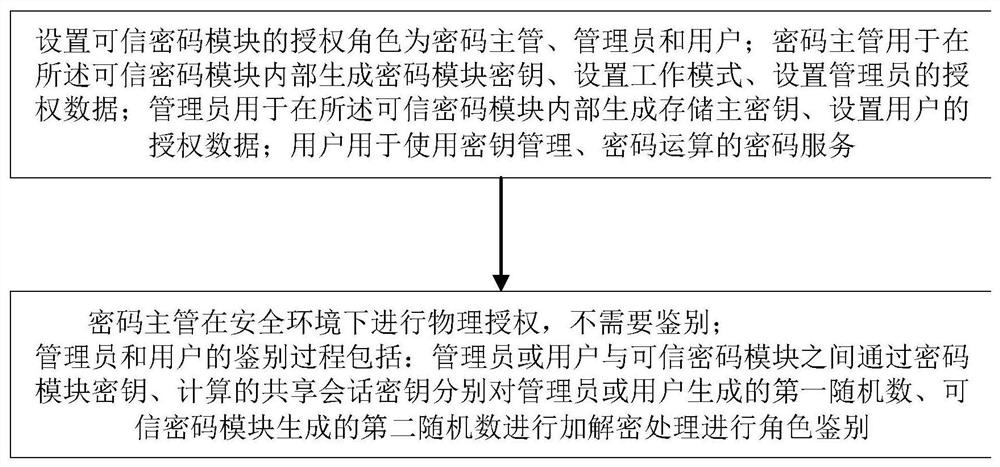
[0035] S1. Set up the trusted cryptographic module authorization role, which includes the cryptographic supervisor for generating the trusted cryptographic module key and setting the working mode and administrator authorization data, and the management for generating and storing the master key and user setting authorization data members and users of password services;
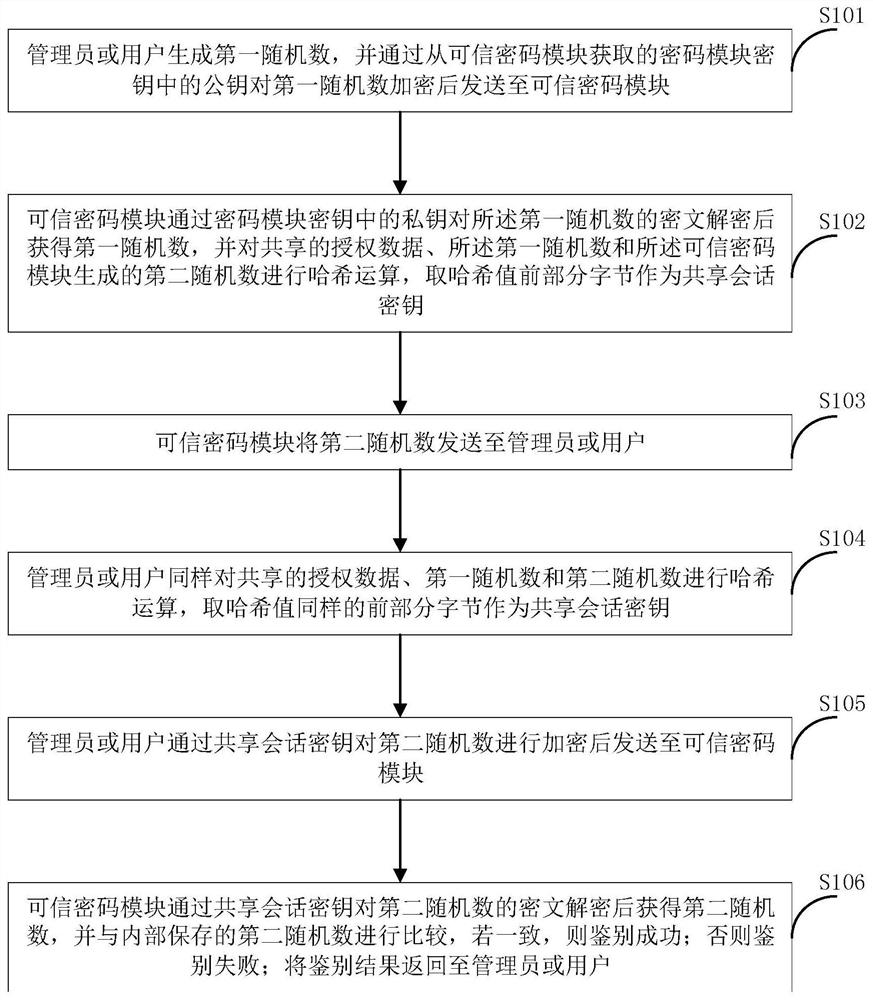
[0036] S2. When logging in to the trusted cryptographic module, physically authorize the cryptographic supervisor in a safe environment; perform encryption and decryption of corresponding data through t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com