A Verifiable Privacy Preserving Method for Encrypted Image Retrieval
A privacy protection and image encryption technology, which is applied in still image data retrieval, still image data indexing, digital data protection, etc., to achieve the effect of feasibility and privacy protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with specific examples.
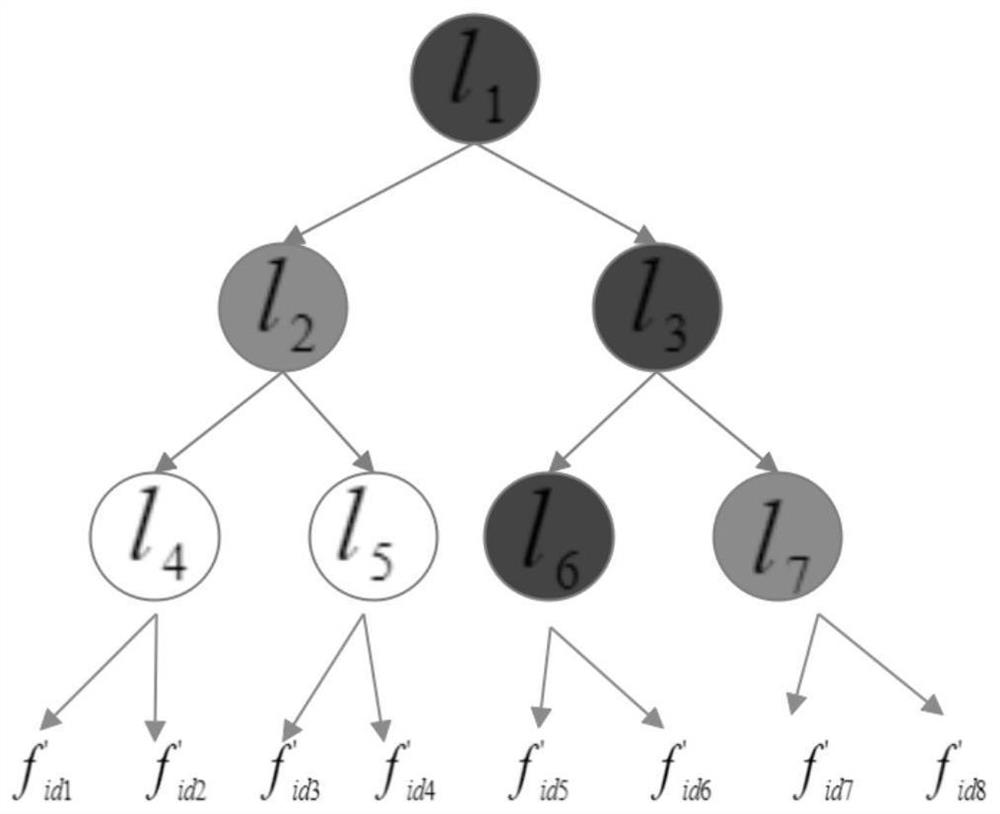
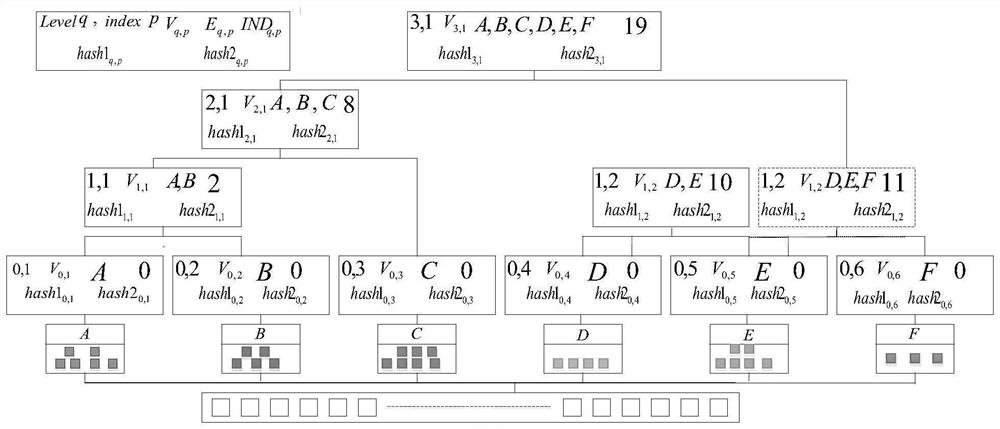
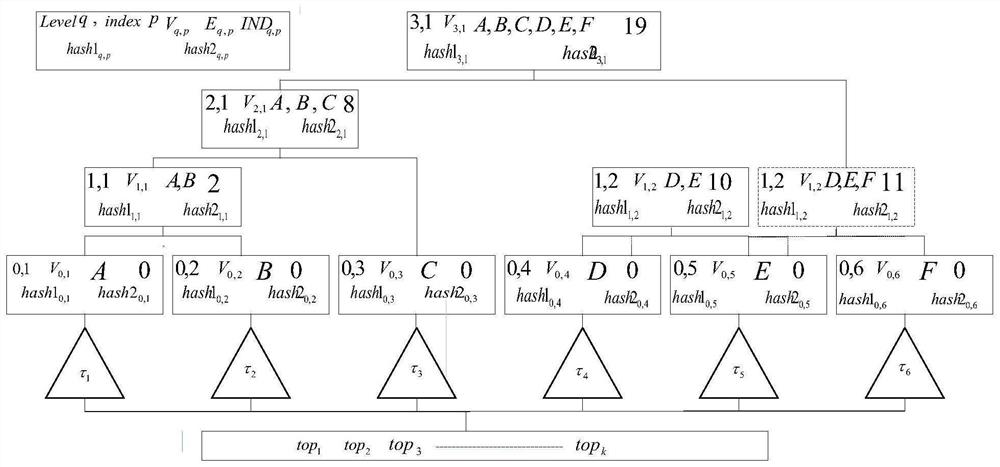
[0049] In order to ensure verifiable query of encrypted pictures in cloud scenarios, the present invention proposes a new query authentication scheme to defend against untrustworthy cloud service providers. The key to realize query verification is to design query verification index structure by integrating existing indexes and cryptographic tools. The image retrieval verification index structure consists of two parts: Merkel hierarchical clustering index tree and MRKD tree construction. The present invention allows image owners to outsource their image databases to cloud-based service providers and ensure the integrity and correctness of query processing. Like other common data-as-a-service (DaaS) systems, it consists of three parties: (i) the image owner who outsources ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com