DDOS attack detection method based on software defined network
A software-defined network and attack detection technology, applied in electrical components, digital transmission systems, security communication devices, etc., can solve the problems of reduced detection accuracy, misjudgment of suspicious traffic, invalid detection, etc., to improve detection accuracy, reduce The effect of detecting delay and avoiding double counting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Below in conjunction with accompanying drawing and specific embodiment, the present invention is described in further detail:
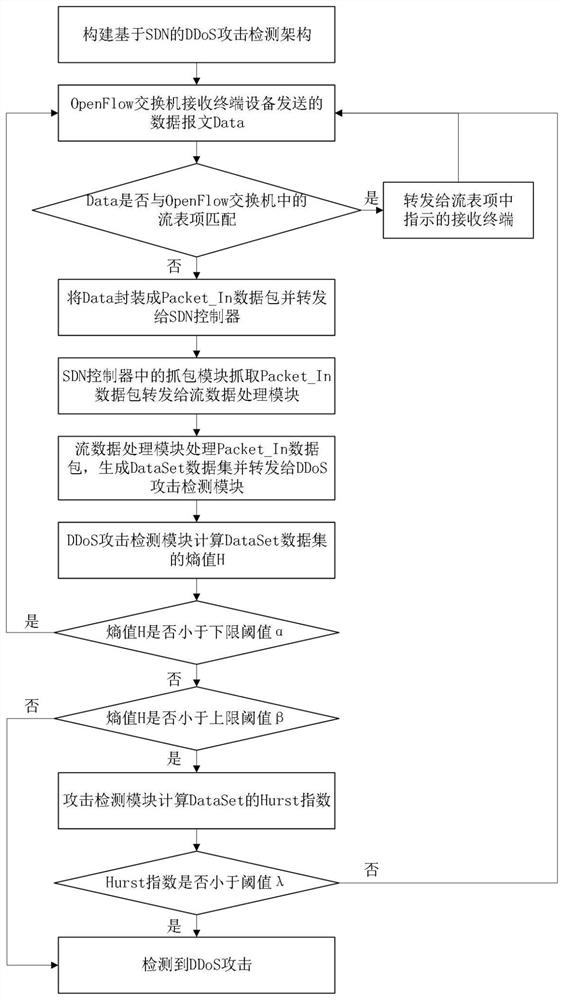
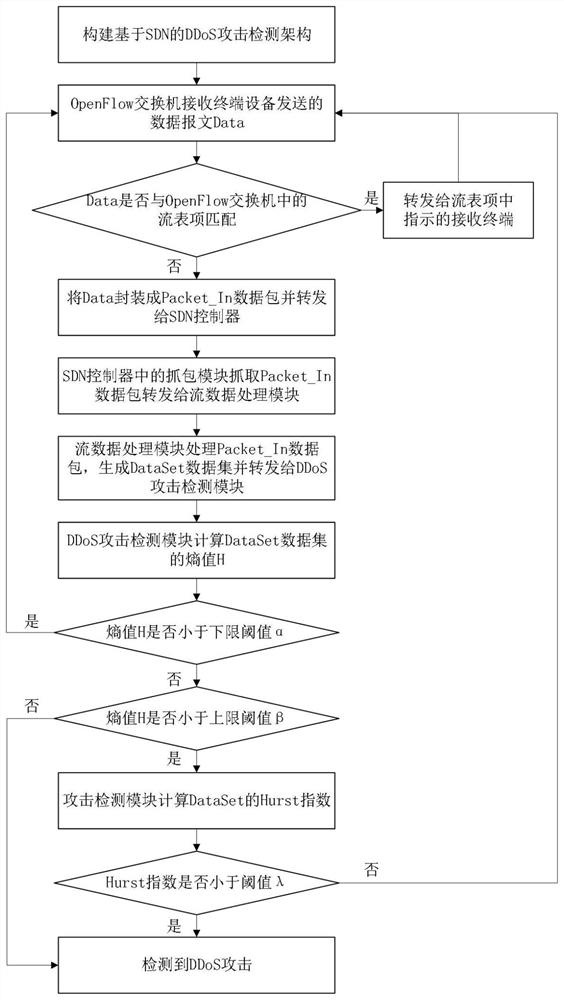
[0032] refer to figure 1 , the present invention comprises the steps:
[0033] Step 1) Build a distributed denial of service DDoS attack detection architecture based on software-defined network SDN:
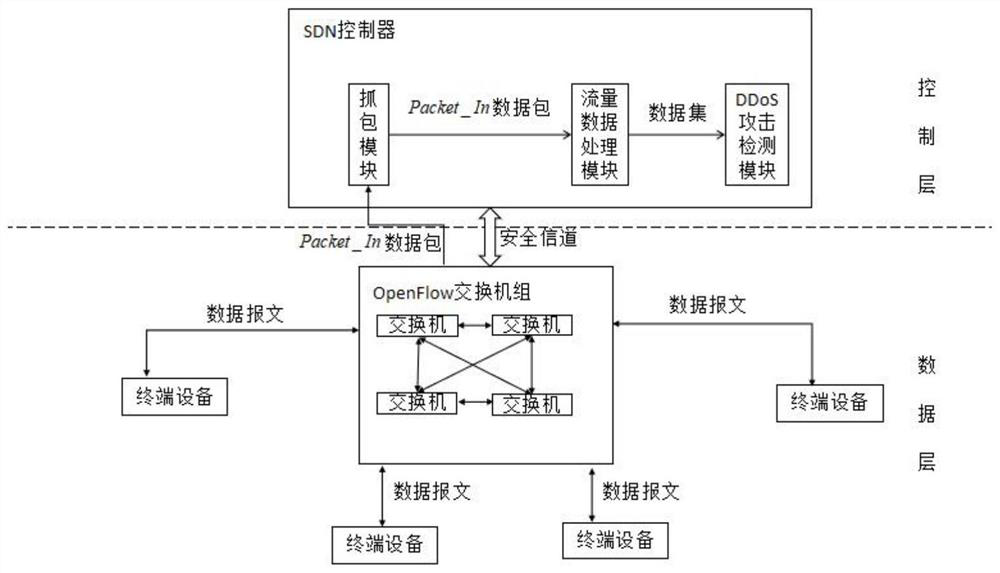
[0034] A distributed denial of service DDoS attack detection architecture based on software-defined network SDN is constructed, including a control layer and a data layer; the control layer adopts an SDN controller including a packet capture module, a stream data processing module and a DDoS attack detection module, and the data The layer includes M OpenFlow switches S=[S 1 ,...,S m ,...,S M ], per OpenFlow switch S m Include OpenFlow flow table K m , K m Contains flow entry matching rules and R flow entries [k m1 ,k m2 ,...,k mr ,...,k mR ], each flow entry k mr Contains matching fields and processing instructions; where M≥1, S m rep...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com