Long-link internet service multi-mode security verification code technology
An Internet business and security verification code technology, which is applied in the field of multi-mode security verification codes for long-link Internet services, can solve the problems of poor security, transaction data tampering, and low transaction efficiency in long-link Internet services, so as to ensure non-tampering , the effect of ensuring correctness and enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
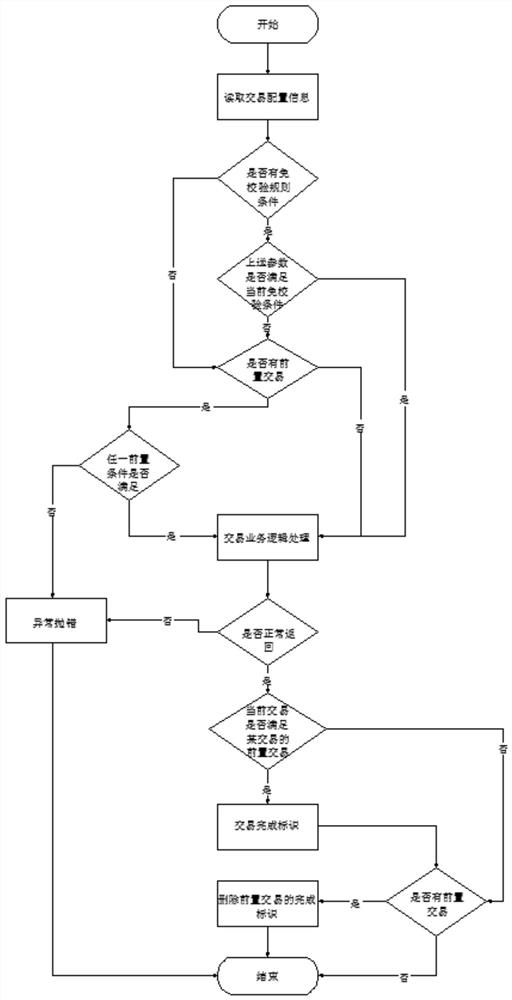
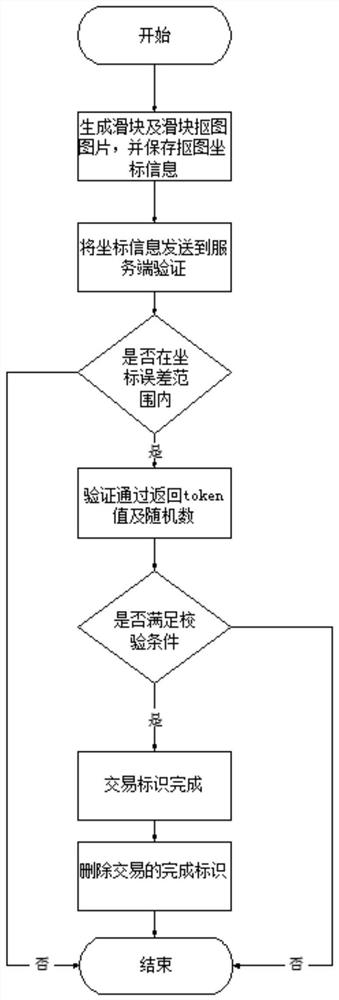
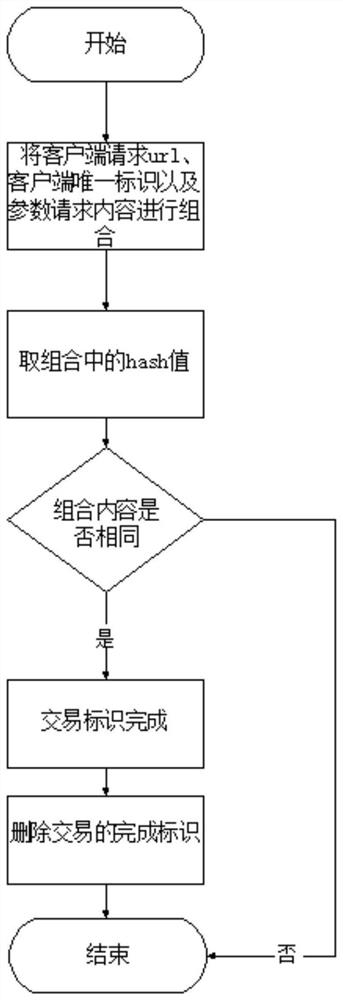
[0018] In the actual Internet business, the implementation steps of the long-link Internet business multi-mode security verification code technology are as follows:
[0019] In the distributed micro-service scenario, the gateway is the gate of specific core business services. All forwarding background transactions need to pass through the gateway. Taking the zuul gateway as an example, the zuul gateway routes user requests. The routing process is divided into pre-routing filters (pre), routing forwarder (routing), post-routing filter (post), and error filter (error), among which the pre-routing filter uses the transaction link control mode to check whether the transaction is necessary to pre-order according to the transaction elements condition, if the matching precondition is completed, it will pass; otherwise, the current transaction will be exited abnormally.
[0020] After the routing forwarder forwards the specific core business service, the post-routing filter will use t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com