Method for processing video in TF card
A video processing and video technology, applied in the field of video processing in TF card, to achieve large application space, protect security and uniqueness, and enhance the effect of expanding space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to describe the present invention more clearly, the present invention will be further described below in conjunction with the accompanying drawings and examples. The specific protection scope of the application belongs to the protection scope of the application under the timely enlightenment of the application and without any creative work.
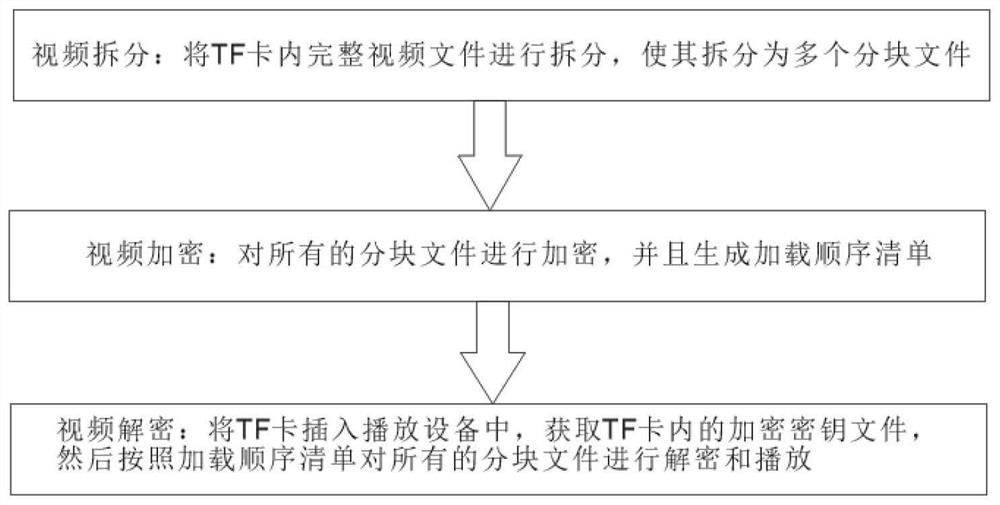
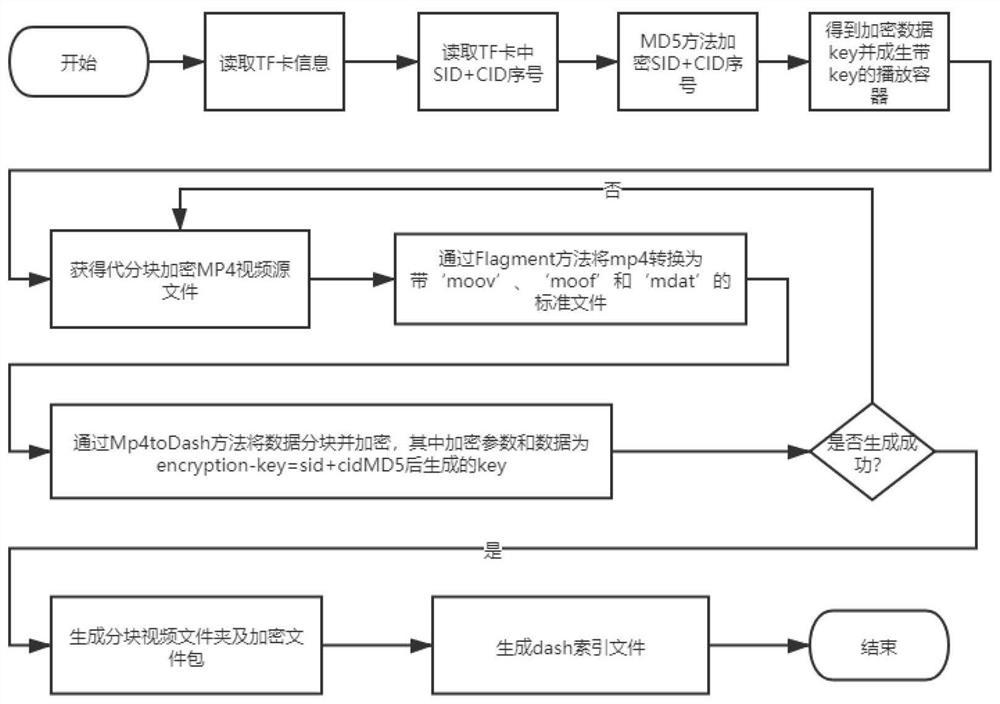
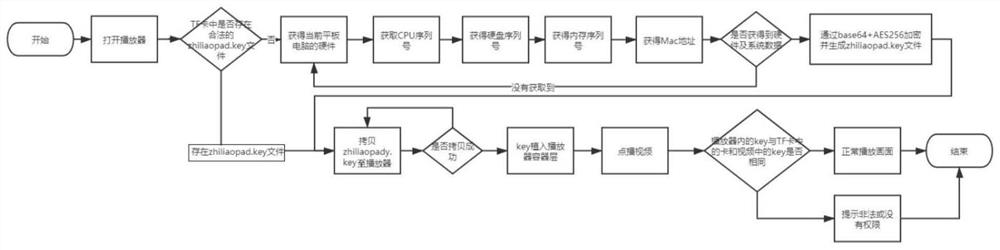
[0021] see figure 1 , the invention discloses a method for processing video in a TF card, comprising the following steps: video splitting: splitting a complete video file in a TF card to split it into multiple block files; video encryption: converting all Encrypt the block files and generate a loading sequence list; video decryption: insert the TF card into the playback device, obtain the encryption key file in the TF card, and then decrypt and play all the block files according to the loading sequence list. In this embodiment, a complete video is first split into a plurality of different block files, and these block file...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com