Big data particle algorithm system
A big data and computing system technology, applied in data mining, electrical digital data processing, special data processing applications, etc., can solve the problems of missing effective data information, resource loss, etc., to avoid resource loss, facilitate observation and analysis, and improve effective The effect of information acquisition rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only some, not all, embodiments of the present invention.
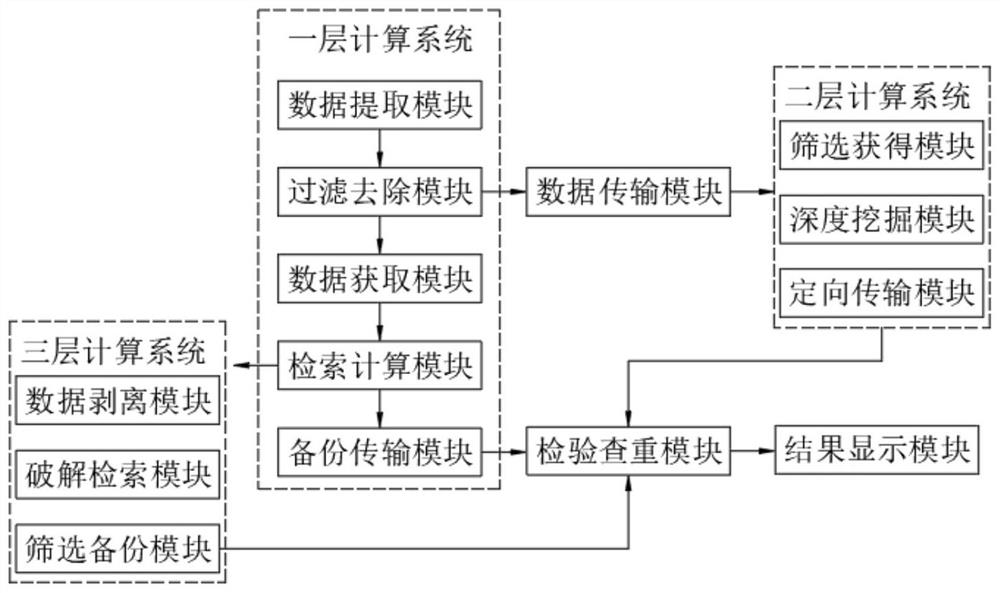
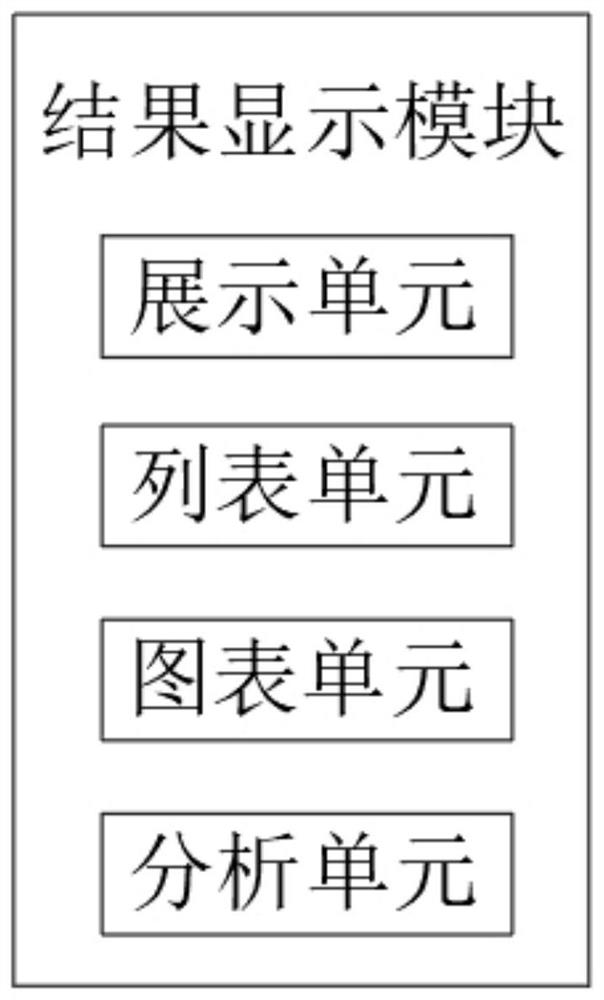
[0017] refer to Figure 1-2 , a big data granular algorithm system, including a first-tier computing system, a second-tier computing system, and a third-tier computing system, the first-tier computing system includes a data extraction module, the output of the data extraction module is connected to a filter removal module, and the filter removal module The output end of the data acquisition module is connected with a data acquisition module, the output end of the data acquisition module is connected with a retrieval calculation module, the output end of the retrieval calculation module is connected with a backup transmission module, and the output end of the backup tr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com