Energy control terminal strategy file security reinforcement method and system
A policy file and energy control technology, applied in computer security devices, program/content distribution protection, instruments, etc., can solve problems that affect the experience of authorized users, authorized programs cannot run normally, and cannot return correct results, etc., to reduce downtime The effect of service probability, reduction of hardware cost investment, and reduction of leakage risk
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
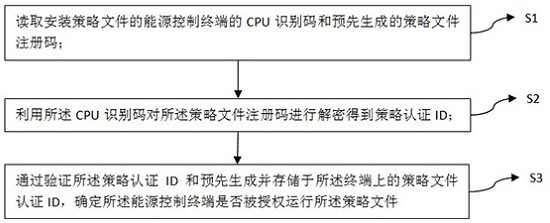
[0045] A security reinforcement method for an energy control terminal policy file proposed by the present invention is a security reinforcement method for a policy file independently running on a new type of energy control terminal with edge computing capabilities, such as figure 1 shown, including:
[0046] S1. Read the CPU identification code of the energy control terminal where the policy file is installed and the pre-generated policy file registration code;
[0047] S2. Using the CPU identification code to decrypt the policy file registration code to obtain a policy authentication ID;
[0048] S3. Determine whether the energy control terminal is authorized to run the policy file by verifying the policy authentication ID and the policy file authentication ID generated in advance and stored on the terminal;
[0049] Wherein, the policy file registration code is generated based on the identity authentication ID corresponding to the policy file and the CPU identification code...
Embodiment 2
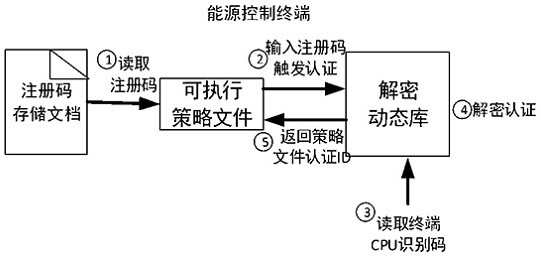
[0062] The following uses a specific example to introduce the security reinforcement method of an energy control terminal policy file proposed by the present invention from the registration code generation to the final authentication stage. It specifically includes four steps: preparation, encryption, policy delivery, and decryption. Figure 4 shown.
[0063] In the first preparation stage, the policy generator (strategy development unit) needs to send the policy information (unit number, classification number, policy number) to the security administrator (policy management unit), and the security administrator will enter the policy information into the policy file for authentication. The ID generator is used to generate the policy identity authentication ID, and the security administrator returns the generated authentication ID together with the decrypted dynamic library program and the calling example to the policy generator. The policy generator realizes the self-authenticat...
Embodiment 3
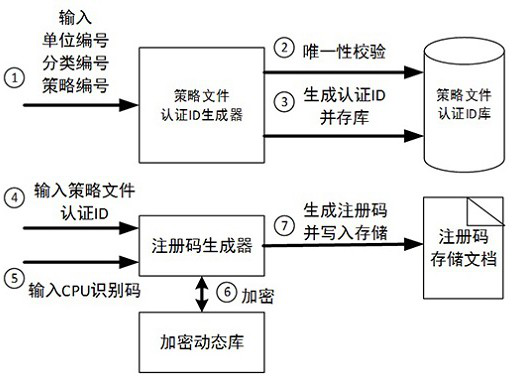
[0068] In order to realize the above method, the present invention also proposes an energy control terminal policy file security reinforcement system, which includes a registration code generation module, a decryption dynamic library, a registration code storage file and a policy file authentication ID library. Wherein, the registration code generating module is used to generate a policy file registration code based on the identity authentication ID corresponding to the policy file and the CPU identification code of the policy terminal, which specifically includes a policy file authentication ID generator, a registration code generator and Encrypted dynamic library; specific as Figure 5 shown.
[0069] The detailed functions of each component include:
[0070] (1) Policy file authentication ID generator
[0071] The strategy file authentication ID generator is to generate a unique identity authentication information ID for a certain or a certain batch of strategy files that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com