Network terminal port scanning method and network terminal port scanning system
A network terminal and port scanning technology, applied in the field of information security, can solve problems such as long scanning time and unfavorable security vulnerability discovery, and achieve the effect of reducing scanning time, improving scanning efficiency, and fast and efficient discovery.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
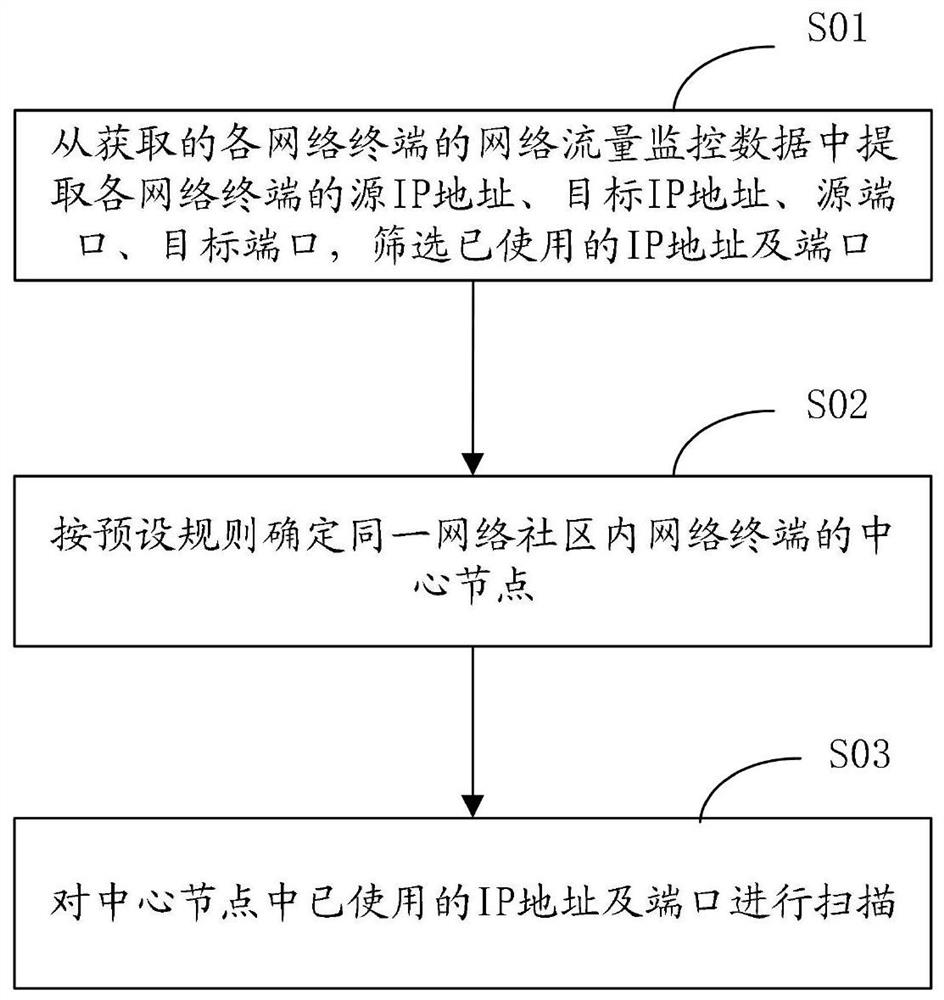
[0041] In some embodiments, a network terminal port scanning method, such as figure 1 shown, including the following steps:
[0042] S01. Extract the source IP address, target IP address, source port, and target port of each network terminal from the acquired network traffic monitoring data of each network terminal, and filter used IP addresses and ports.
[0043] In this embodiment, the network terminal may be a server or a client, and may be a PC or a mobile terminal device. These network terminals are mainly managed by a network terminal management device, using hardware probes, traffic mirroring analyzers or SNMP (Simple Network Management Protocol)-based traffic analyzers to monitor network traffic data. Specifically, the hardware probe is serially connected to the link that needs to capture the flow, and the flow data is obtained by shunting the digital signal on the link. Traffic mirroring analysis is to mirror the traffic of a certain link of the network terminal to ...
Embodiment 2
[0068] In order to further optimize the network terminal port scanning method and improve scanning efficiency, in some embodiments, a network terminal port scanning method, such as Figure 4 shown, including the following steps:
[0069] S01a. Obtain the source IP address, target IP address, source port, and target port of each network terminal, and filter the used IP addresses and ports.
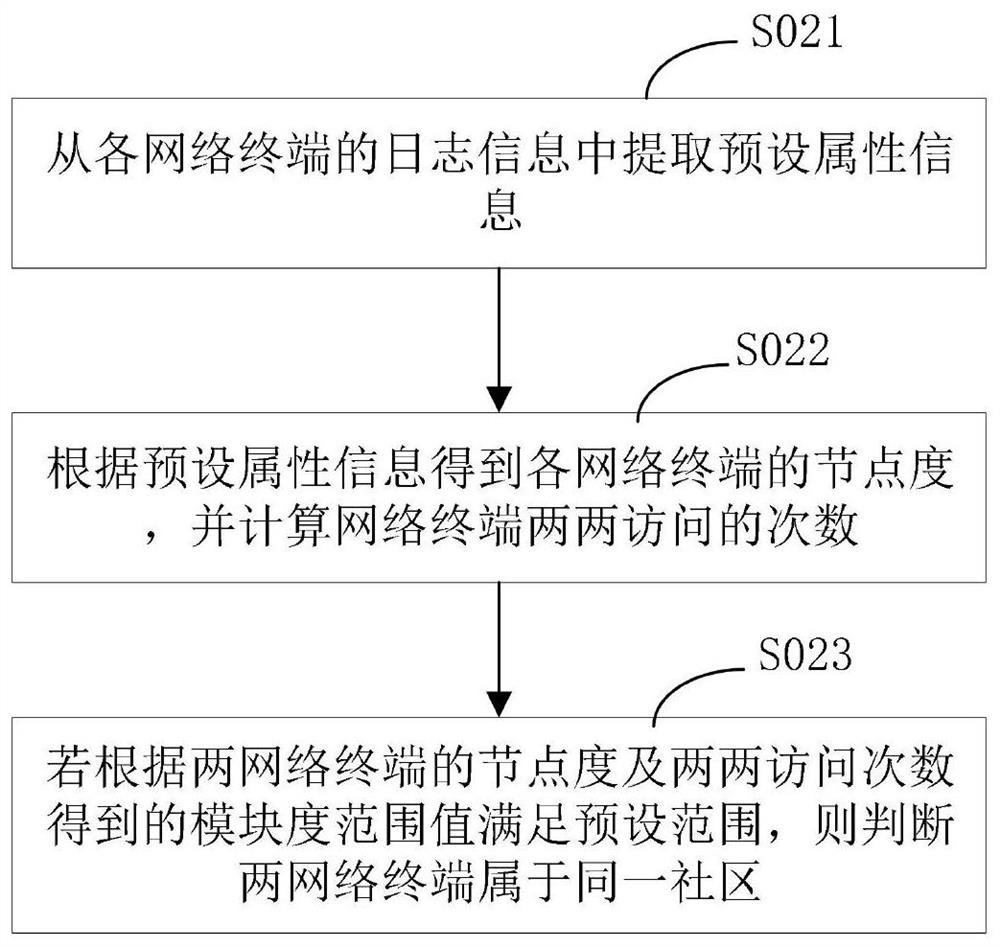
[0070] S02a. Determine the central node of the network terminal in the same network community according to preset rules.
[0071] For the specific content of steps S01a and S02a, reference may be made to Embodiment 1, which will not be repeated here.
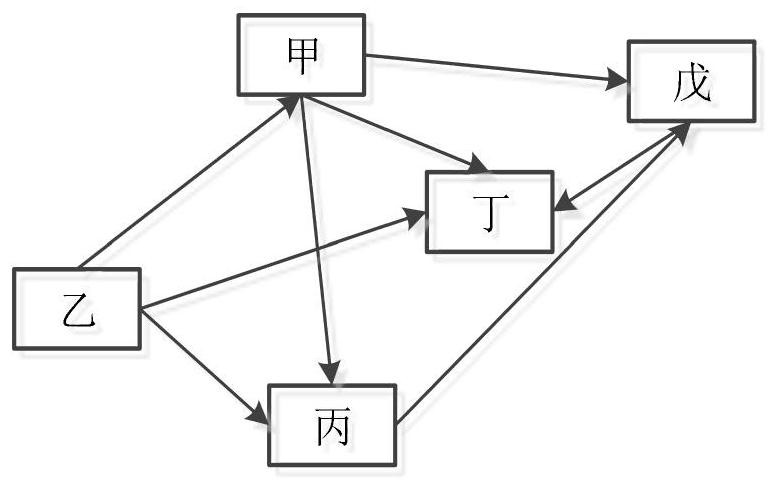
[0072] S03a, looking for a first-degree node of the central node.
[0073] For a network community, in addition to the central node, it also includes edge nodes. The edge nodes can at least include first-degree nodes, second-degree nodes, and third-degree nodes. The first-degree nodes are network terminals that have a direct access relation...
Embodiment 3
[0106] The embodiment of the invention also discloses a network terminal port scanning system, which combines Figure 8 As shown, at least include screening module 11, priority determination module 12, scanning module 13, wherein:
[0107] The screening module 11 is used to extract the source IP address, target IP address, source port, and target port of each network terminal from the obtained network traffic monitoring data of each network terminal, and filter the used IP addresses and ports.
[0108] The screening module 11 can obtain network traffic data monitored by a hardware probe, a traffic mirroring analyzer, or a traffic analyzer based on SNMP (Simple Network Management Protocol). A traffic log information file is generated according to the detected network traffic data, and the traffic log information generally includes at least a source IP address, a destination IP address, a source port, a destination port, and the like.
[0109] The priority determination module ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com