TEE-based operating system application integrity measurement method and system
An integrity measurement, operating system technology, applied in the field of TEE-based operating system application integrity measurement, can solve problems such as plaintext data interception and security risks, and achieve the effects of strong scalability, comprehensive protection, and good versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
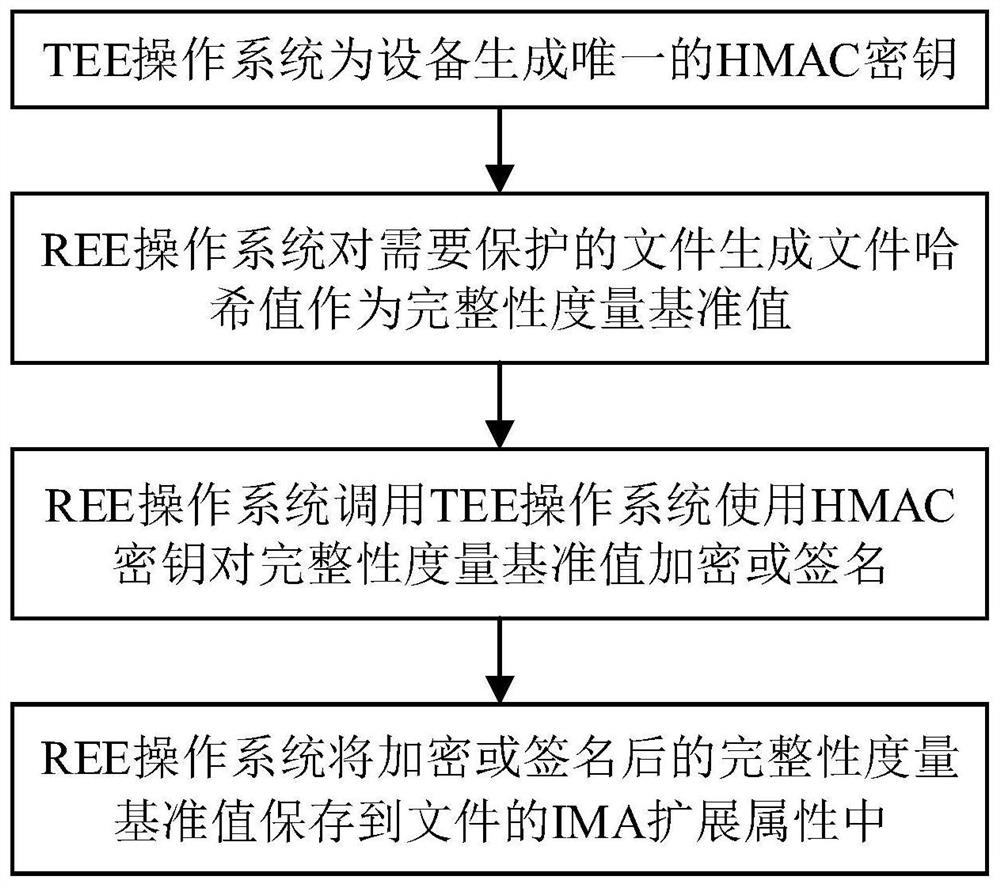
[0035] Such as figure 1 As shown, the TEE-based operating system application integrity measurement method in this embodiment includes:
[0036] 1) The TEE operating system generates a unique HMAC key for the device;
[0037]2) The REE operating system generates a file hash value for the file to be protected as the integrity measurement benchmark value;
[0038] 3) The REE operating system calls the TEE operating system to use the HMAC key to encrypt or sign the integrity measurement benchmark value;
[0039] 4) The REE operating system saves the encrypted or signed integrity measurement reference value into the IMA extended attribute of the file.
[0040] In this embodiment, in step 2), the REE operating system generates a file hash value for the file to be protected means that the REE operating system uses the modified evmctl execution program to generate a file hash value for the file to be protected.
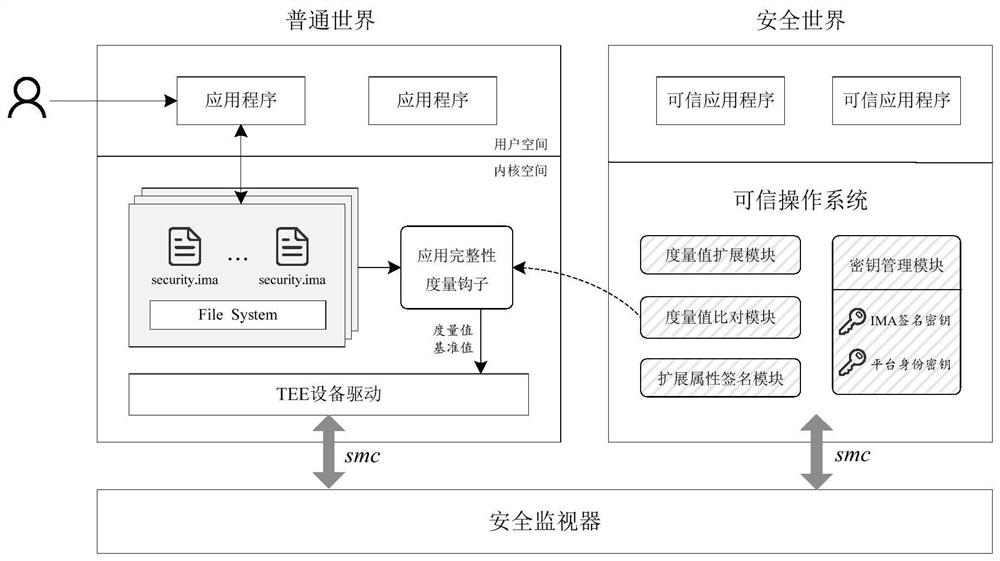
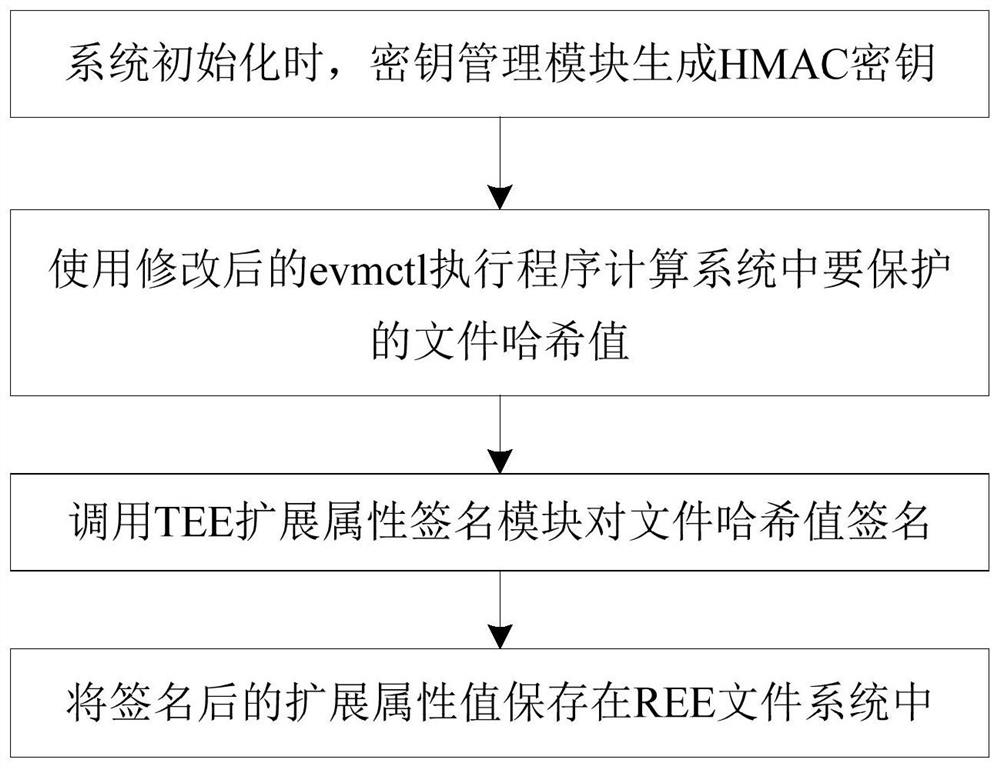
[0041] see figure 2 In this embodiment, when the system is deployed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com