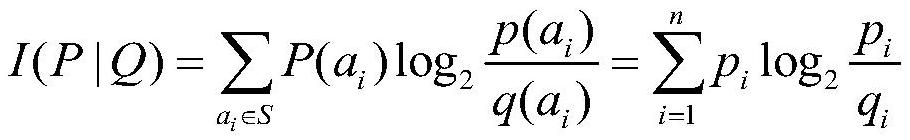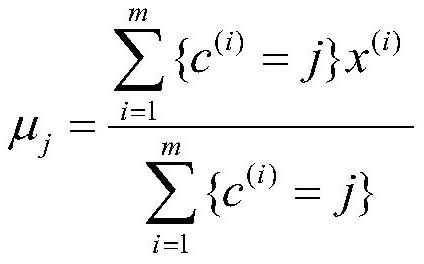Multilayer traffic intrusion detection method based on relative information entropy and semi-supervised clustering
A semi-supervised clustering and relative information technology, applied in the field of network traffic anomaly detection, can solve problems such as difficulty in obtaining the global optimal solution, and achieve the effects of rapid detection, accurate intrusion detection, and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings.
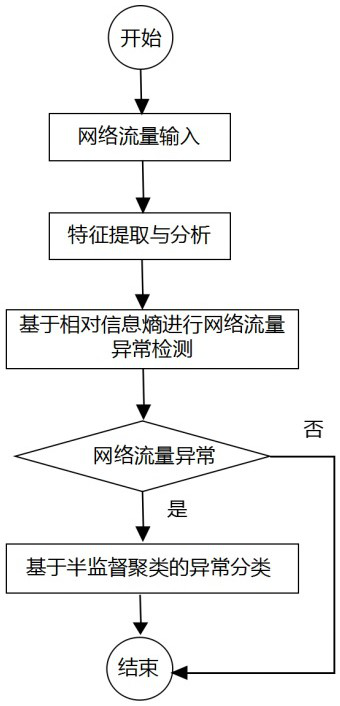
[0024] The present invention designs a multi-layer traffic intrusion detection method based on relative information entropy and semi-supervised clustering, which is used to realize intrusion detection for the network between two target terminals. In practical applications, such as figure 1 As shown, the specific steps are as follows.
[0025] Step A. Sequentially collect the network communication traffic between the two target terminals, and analyze the protocol based on DPI to obtain the traffic log data corresponding to each network communication, and then enter step B.
[0026] Step B. For each network communication flow, obtain the characteristic value corresponding to each specified characteristic attribute of the network flow, and then obtain the characteristic value corresponding to each designated characteristic ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com