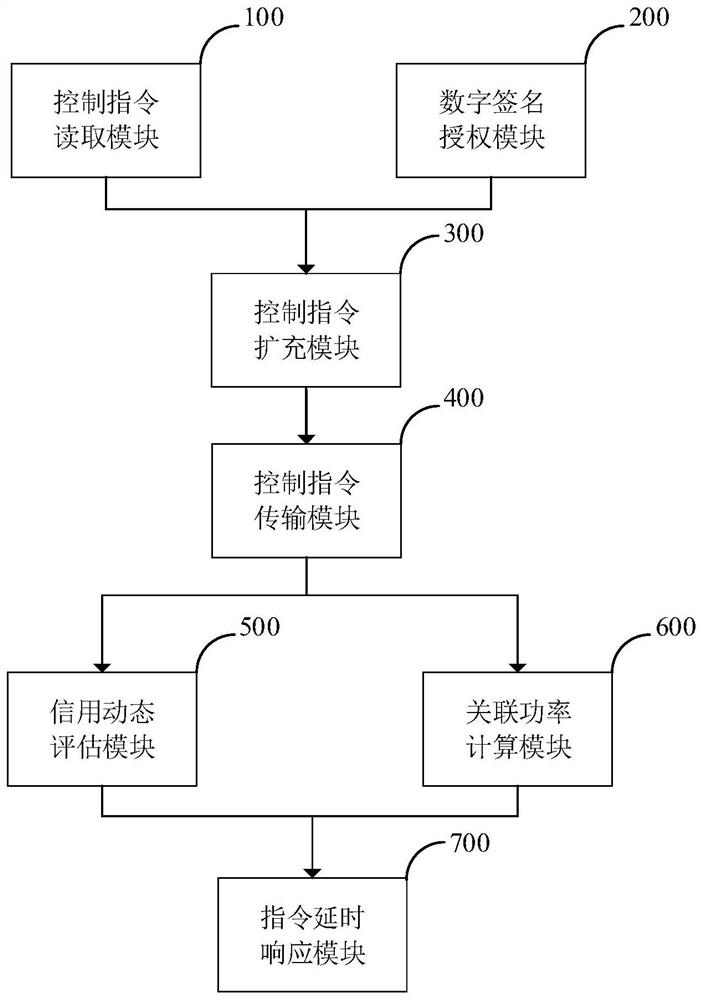
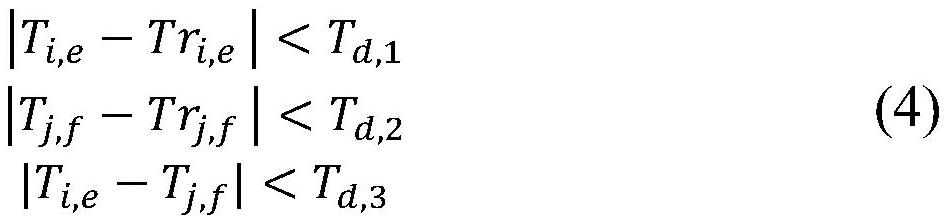Method and system for dynamically executing control commands of power heterogeneous equipment
A technology of equipment control and execution method, applied in the field of power system, can solve the problems of neglecting the security of remote control system, frequency offset of power system, affecting the security of target system, etc., and achieve the effect of reducing information security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
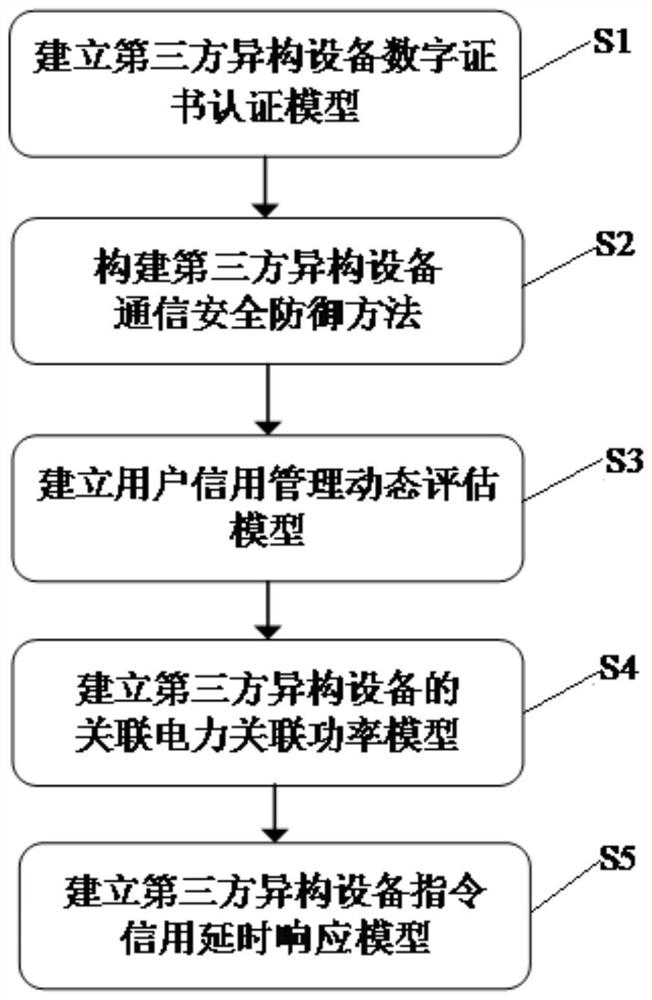
[0118] Further as a preferred embodiment, the step S1 includes:
[0119] Step S11: User U i Choose your own user ID i and password PW i . To protect the password PW i security, choose a random number, and calculate the random password RPW containing the random number i , the specific calculation formula is as follows:
[0120] RPW i =h(a t ||PW i ) (1)
[0121] Among them, i is the user number, a t is a random number at time t, || is a connection, h(.) is a one-way hash function, and the algorithm for generating random passwords in the present invention adopts the national secret SM3 hash algorithm.
[0122] In one embodiment, user U 1 Set your own user ID 1 For CXSG2021, password PW i For GXJDDNN, random number a t is E8, then the random password RPW 1 for h(E8GXJDDNN).
[0123] Step S12: according to user identification ID i and random password RPW i , add user time freshness factor T i,e And the third-party heterogeneous device identifier TID j , Constru...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com