A Trusted Channel Authentication System Based on Protecting Sensitive Data of Disappeared Members
An authentication system and sensitive data technology, applied in the transmission system, digital data protection, electronic digital data processing, etc., can solve the problems of sensitive data leakage of disappearing users, insufficient protection mechanism, etc., and achieve the effect of avoiding data theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
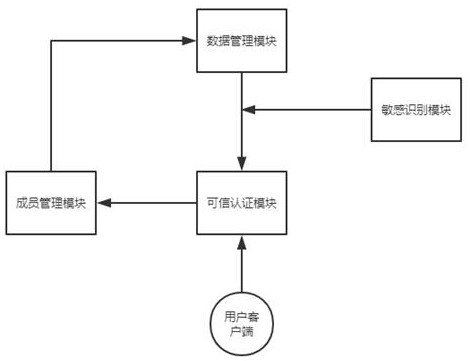
[0030] This embodiment provides a trusted channel authentication system based on protecting sensitive data of vanishing members, including a member management module, a data management module, a trusted authentication module and a sensitive identification module, and the member management module is used to save basic information of members And judge whether the member disappears, the data management module is used to save the data information of the member, the trusted authentication module is used to obtain the data information of the member and perform credible authentication, and the sensitive identification module is used to verify the data information Sensitivity identification of the data items in;
[0031] The member management module monitors the activity of each member, and the calculation formula of the activity H is:
[0032] ;
[0033] Among them, T i Indicates the time interval from the last ith login system to the current time, t i Indicates the activity dur...
Embodiment 2
[0044] This embodiment includes all the content of Embodiment 1, combined withfigure 1 , this embodiment provides a trusted channel authentication system based on protecting sensitive data of vanished members, including a member management module, a data management module, a trusted authentication module and a sensitive identification module, the member management module is used to store basic member information , the data management module is used to store data information of members, the trusted authentication module is used to obtain data information of corresponding members and perform credible authentication, and the sensitive identification module is used to verify the data in the data management module carry out sensitivity identification;
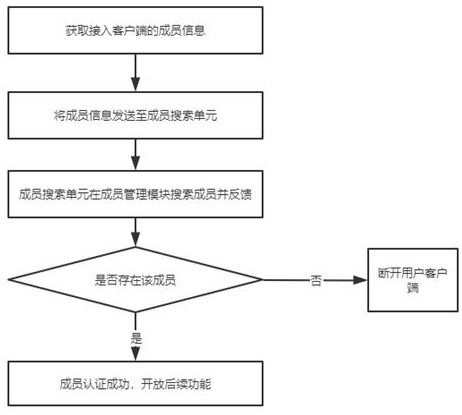
[0045] The system also includes a user client. The user client is used for user registration and login. After a new user registers, the basic information of the new member is generated in the member management module. After the new u...
Embodiment 3
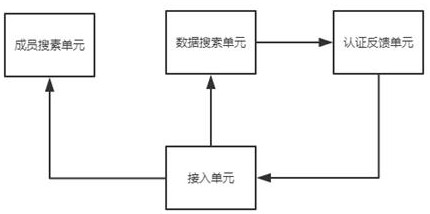
[0057] This embodiment includes all the content of the above-mentioned embodiments. The data storage code in this embodiment is generated by the data management module, stored in the member management module, and used to search for corresponding members after being acquired by the trusted authentication module. The data, the data storage code is encrypted and protected by encryption technology when circulating in the above three modules;
[0058] combine Figure 4 , the data management module generates a verification code after the member uploads the data information for the first time, and the verification code and the first address of the stored data information are combined into a first encryption code, and the first encryption code is sent to the member management module and combined with The ID information of the corresponding member synthesizes a second encrypted code, and the member search unit of the trusted authentication module obtains the second encrypted code and u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com