Integrity protection with message authentication codes having different lengths
A technology of integrity protection and message authentication code, which is applied in the field of integrity protection of wireless communication, and can solve problems such as unverified/authenticated messages and communication failures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
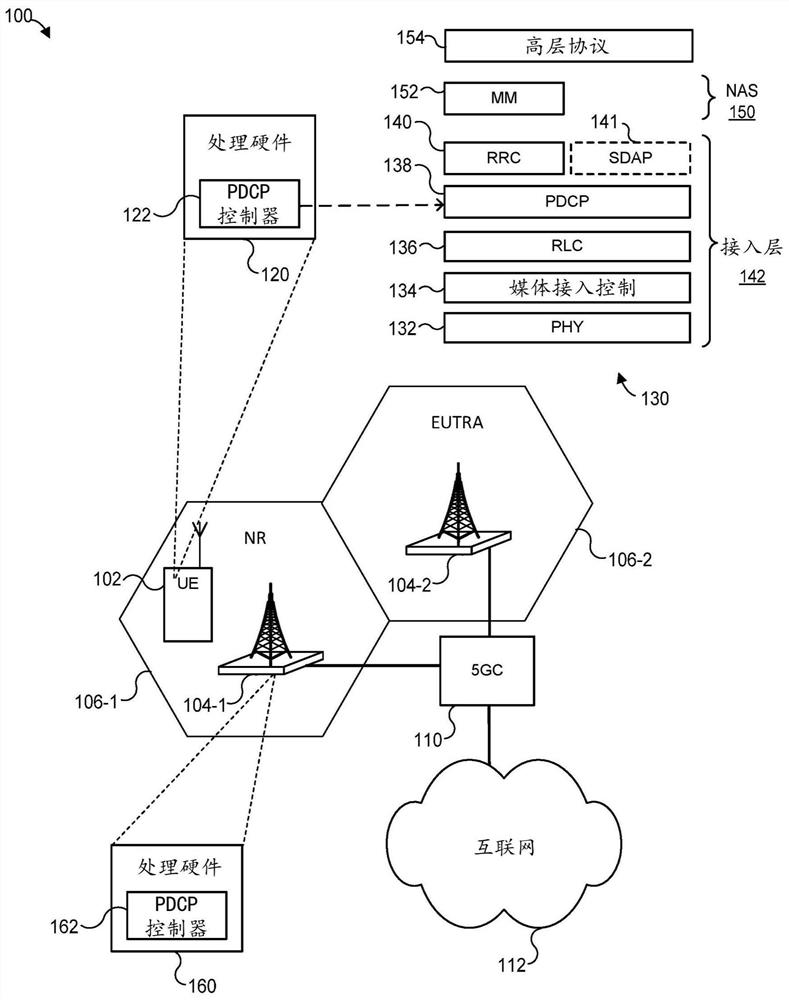
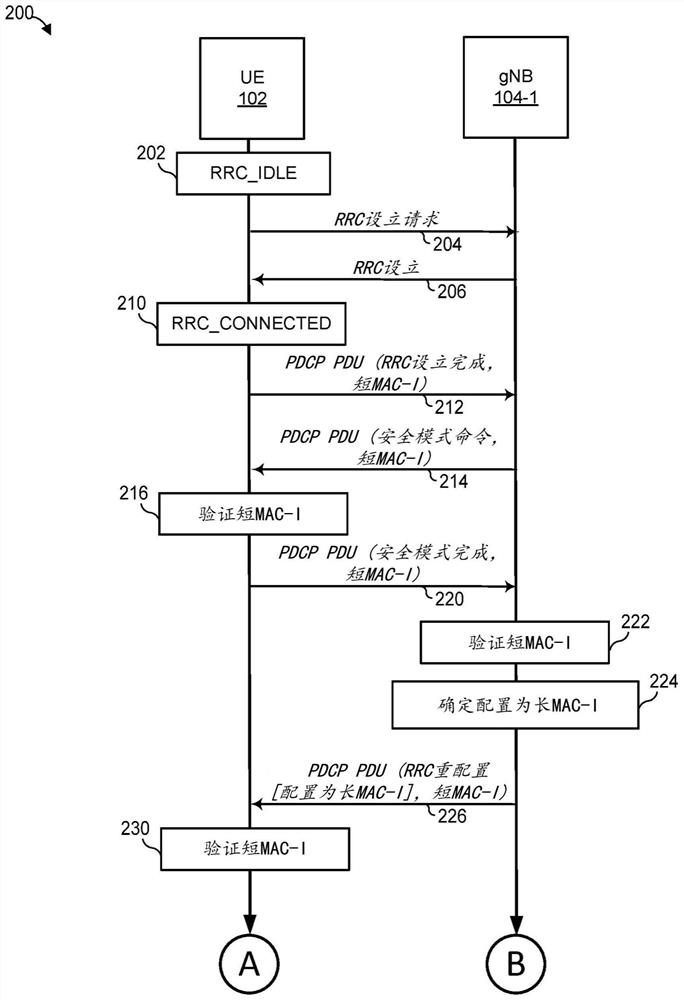
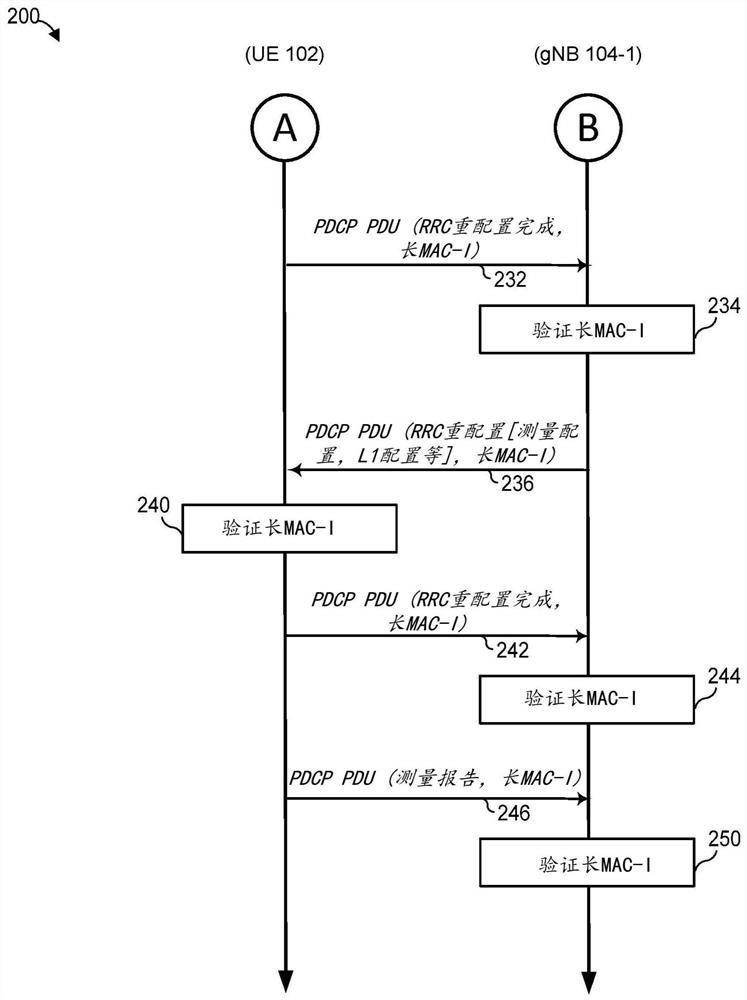
[0018] In general, the techniques of this disclosure allow user equipment (UE) and base stations to use consistent message authentication code (MAC) lengths for integrity protection, thereby allowing authentication / verification of messages in wireless communication networks. Thus, the disclosed technique avoids scenarios where communication is not possible due to lack of authentication. Furthermore, the disclosed techniques can avoid suboptimal system design in which all user equipments and base stations must use a default, relatively short MAC length regardless of their MAC length capabilities. Therefore, in scenarios where both the user equipment and the base station support more robust integrity protection, the integrity protection can be enhanced.
[0019] These techniques are discussed below with reference to fifth generation (5G) radio access ("NR") networks and sometimes Evolved Universal Terrestrial Radio Access (EUTRA) networks as examples. Furthermore, these example...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap