Automatic electricity stealing identification method based on data mining technology
A technology of data mining and identification methods, which is applied in the field of electric stealing identification, can solve problems such as low intelligence, lack of deep mining of electric power data, and long promotion cycle, so as to improve extraction efficiency, improve machine learning effect, and improve identification accuracy. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
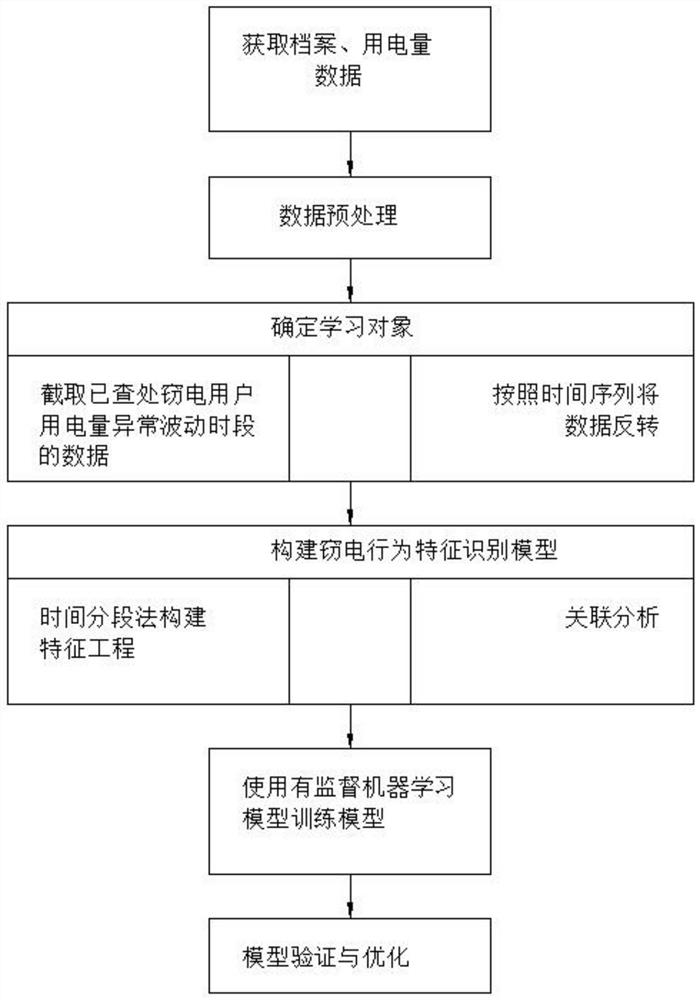
[0047] refer to Figure 1-4 , a kind of automatic electric stealing identification method based on data mining technology, comprises the following steps:
[0048] S1: Obtain files and power consumption data;
[0049] S2: Data preprocessing: Data preprocessing handles the missing values, 0 values and obvious wrong data in the daily frozen display of the user's electric energy meter;
[0050] S2: Data preprocessing: first, intercept the data during the periods of abnormal fluctuations in power consumption of users who have been investigated and dealt with, and second, reverse the data according to the time series;
[0051] S4: Build a feature recognition model for electricity stealing behavior. The model is built using: first, time-segmented method to build a feature engineering model, and second, correlation analysis;
[0052] S5: Use supervised machine learning model, training model;
[0053] S6: Model validation and optimization.
[0054] In this embodiment, S2 specifical...
Embodiment 2
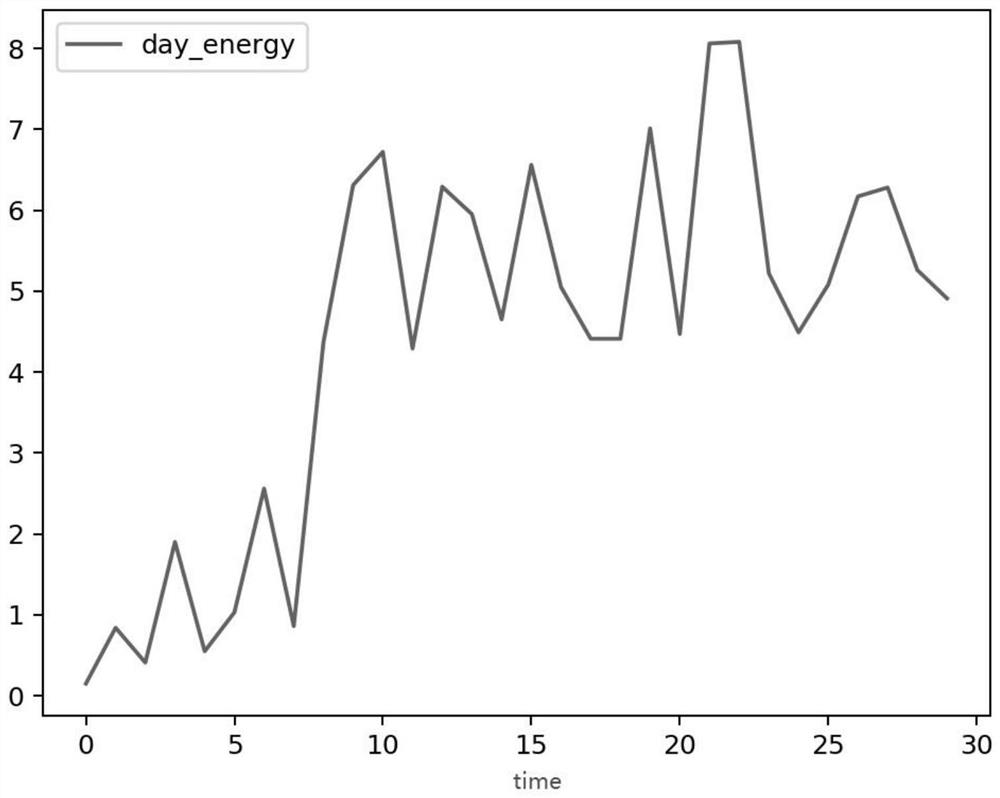
[0078] In this example, figure 1 It is the daily power consumption change curve of a power stealing user for 15 days before and after the date of investigation. Electricity, there should be abnormal fluctuations corresponding to the obvious decline in daily electricity consumption.
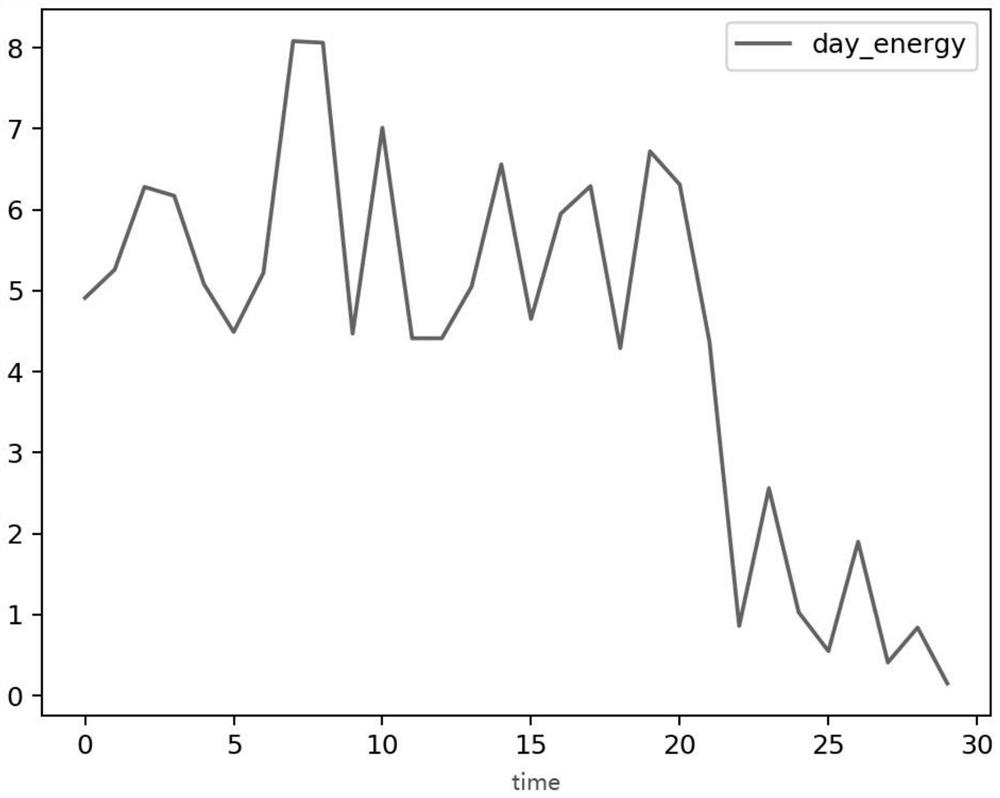
[0079] In this example, for figure 1 The power consumption change curve in is processed according to time reversal, and the abnormal fluctuation curve of power consumption shows a downward trend, simulating the power consumption behavior of power-stealing users, such as figure 2 shown; right figure 2 In the curve construction feature engineering, the data feature extraction of the curve fluctuation is carried out, the daily power change trend of the electricity-stealing users is summarized, and the electricity consumption behavior of the electricity-stealing users is further analyzed.
[0080] In this embodiment, based on the deficiencies in the existing power stealing analysis technology fie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com