User identity authentication method and device, electronic equipment and readable storage medium
A technology of user identity and verification method, which is applied in the fields of devices, electronic equipment and readable storage media, and user identity verification methods, and can solve the problems of inability to confirm key login, user economic or other losses, and inability to judge whether a product processing instruction is for the user Personal real wishes and other issues to achieve the effect of ensuring authenticity and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
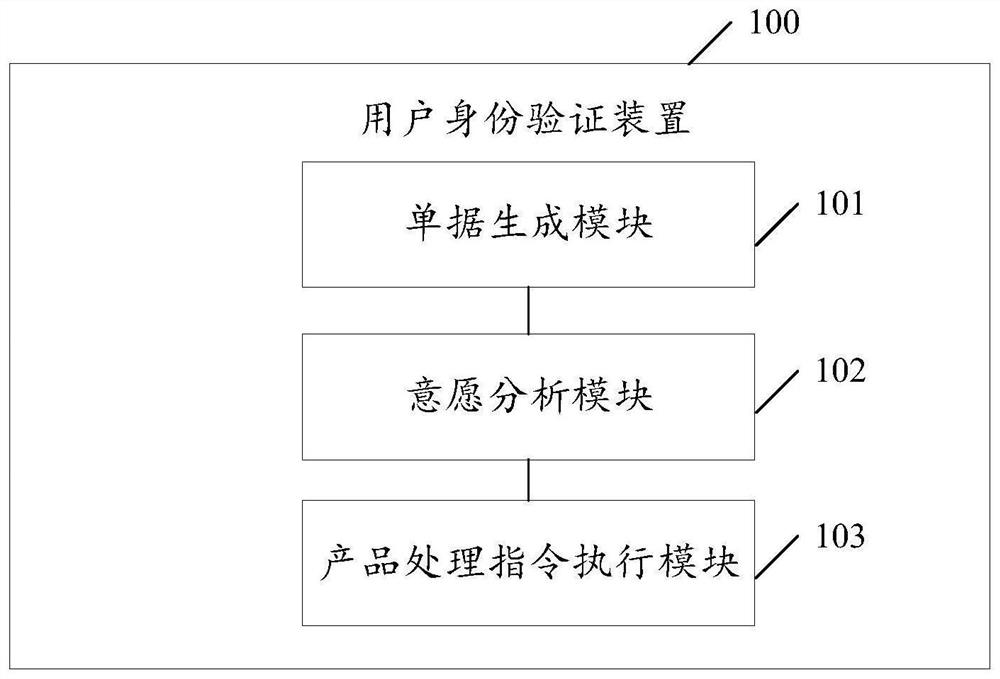
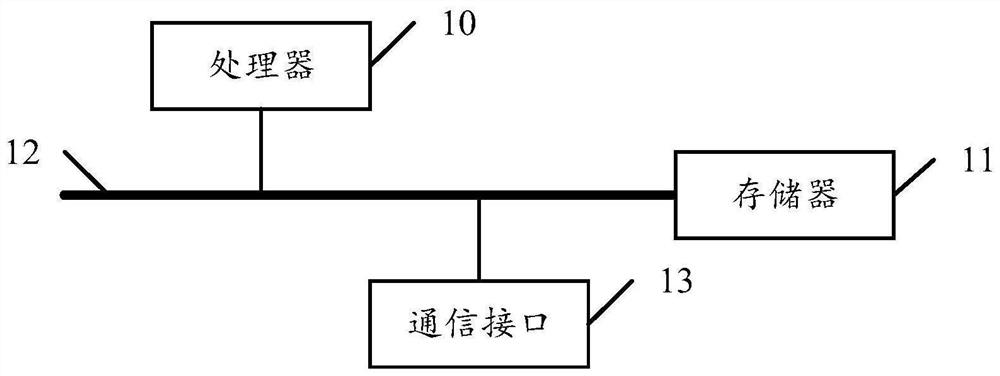
Image
Examples
Embodiment Construction
[0046] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
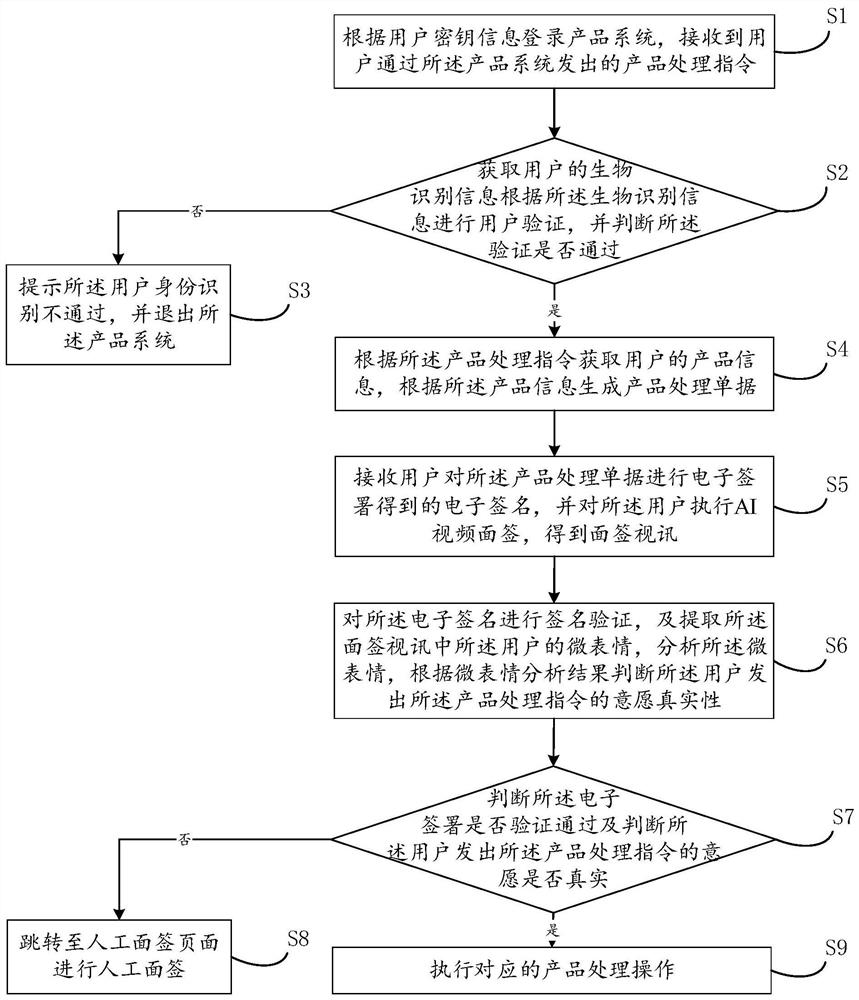
[0047] An embodiment of the present invention provides a user identity verification method. The subject of execution of the user identity verification method includes, but is not limited to, at least one of electronic devices such as a server and a terminal that can be configured to execute the method provided by the embodiment of the present application. In other words, the user identity verification method can be executed by software or hardware installed on the terminal device or server device, and the software can be a block chain platform. The server includes, but is not limited to: a single server, a server cluster, a cloud server or a cloud server cluster, and the like.
[0048] refer to figure 1 Shown is a schematic flowchart of a user identity verification method provided by an embodiment of the present inv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com