Anomaly detection method and device, electronic equipment and computer readable storage medium
A technology of anomaly detection and anomaly score, applied in the field of anomaly detection, can solve problems such as low accuracy and poor real-time performance, and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
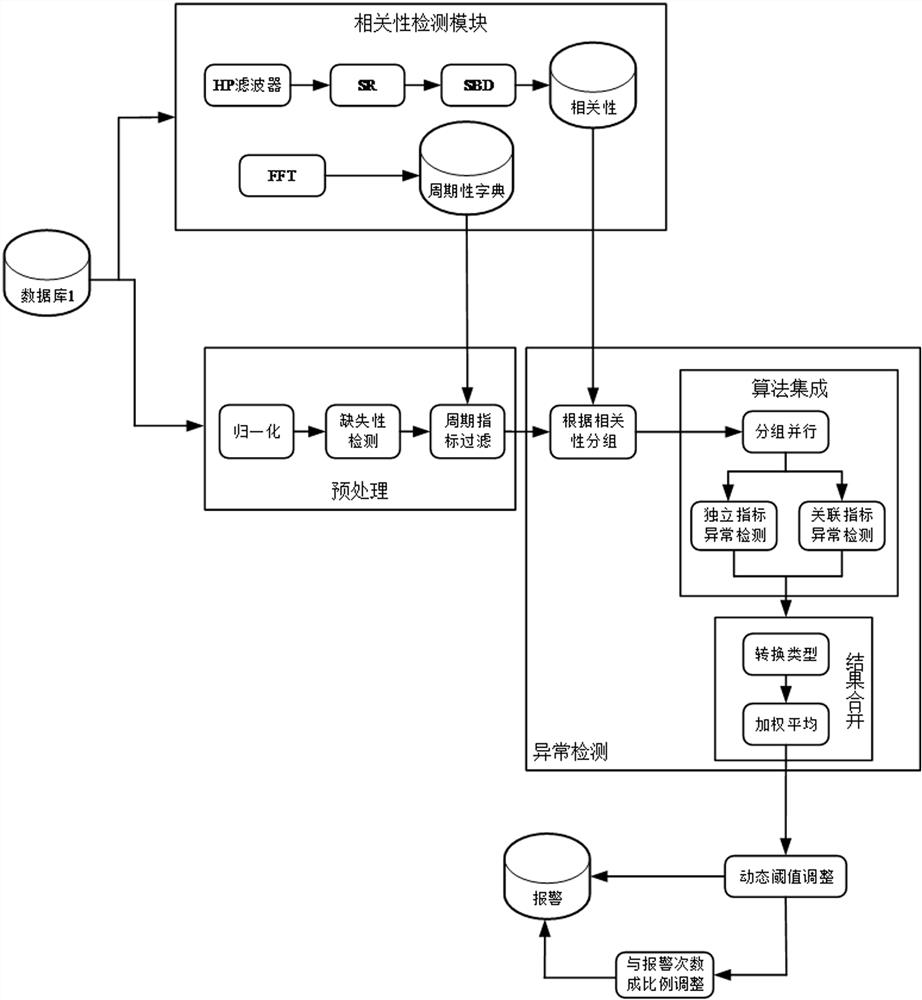
[0029] The solution provided by the embodiment of the present application can be applied to any system with anomaly detection, such as a server system including a chip with anomaly detection function and related components. figure 1 It is a schematic diagram of the application scenario of the anomaly detection scheme provided by the embodiment of the present application, figure 1 The shown scene is only one of the applicable examples of the technical solution of the present application.
[0030] With the development of cloud technology, more and more jobs are changed from offline to online execution. Then, with the increase of online services, users have higher and higher requirements for the quality of online services, especially for the continuity and stability of online services. Users hope to keep abreast of various abnormal events, especially sudden Abnormal events that affect the operation of online services. Especially when online services are becoming more and more c...
Embodiment 2
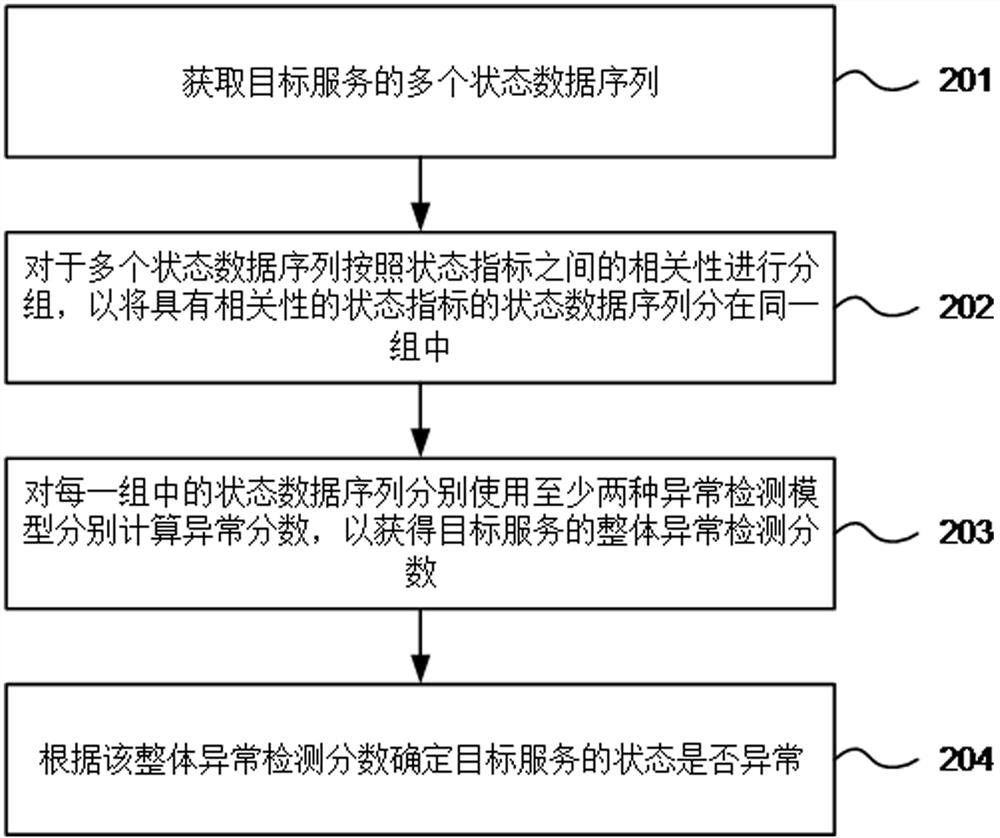
[0094] figure 2 It is a flow chart of an embodiment of the anomaly detection method provided in this application. The method may be executed by various terminals or server devices with anomaly detection capabilities, or devices or chips integrated on these devices. like figure 2 As shown, the anomaly detection method may include the following steps:
[0095] S201. Acquire multiple state data sequences of a target service.
[0096] In the embodiment of this application, it can be obtained from, for example, figure 1 For example, the operation data of the server system is acquired in the database 1 shown in . In particular, multiple state data sequences of the target service within a certain period of time may be acquired, and each state data sequence may correspond to an indicator characterizing the target service.
[0097] S202. Group the multiple state data sequences according to the correlation between the state indicators, so as to group the state data sequences of th...
Embodiment 3
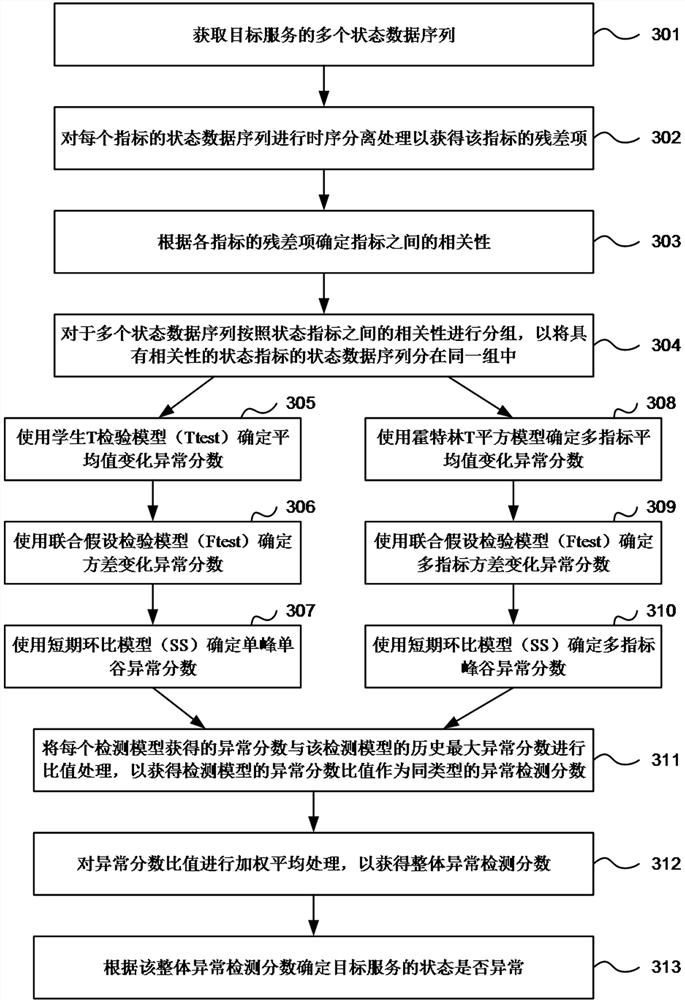
[0110] image 3 It is a flow chart of an embodiment of the anomaly detection method provided in this application. The execution body of the method may be various terminals or server devices with anomaly detection capability, or may be devices or chips integrated on these devices. like image 3 As shown, the anomaly detection method may include the following steps:
[0111] S301. Acquire multiple state data sequences of a target service.
[0112] In the embodiment of this application, it can be obtained from, for example, figure 1 For example, the operation data of the server system is acquired in the database 1 shown in . In particular, multiple state data sequences of the target service within a certain period of time may be acquired, and each state data sequence may correspond to an indicator characterizing the target service.
[0113] S302. Perform time-series separation processing on the status data sequence of each indicator to obtain a residual item of the indicator....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com