Industrial protocol protection method based on iptables u32
An industrial protocol and protocol technology, applied in the field of network security, can solve problems such as inability to recognize protocols or fields, inability to process industrial Internet SCADA messages, etc., to achieve flexible analysis and filtering, and prevent abnormal attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
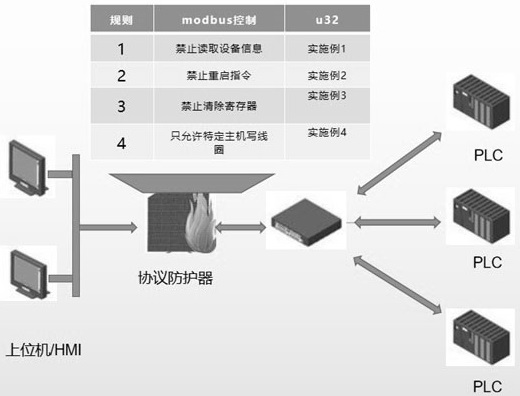
[0056] Embodiment 1: The untrusted network node executes the operation of reading the device identification, but refuses to execute it. Match by filtering modbusfunction 43, MEI 14, READ DEVICE ID(2), OBJECT ID(0).
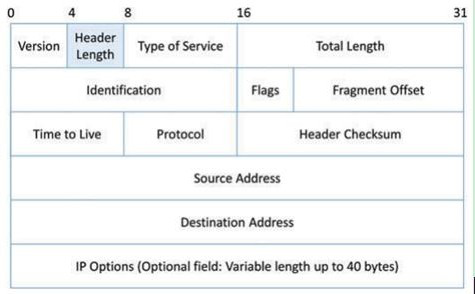
[0057] 1. The system receives the Modbus bytes: 00 04 00 00 00 05 01 2b 0e 02 00. According to the rules, the content is parsed as follows: the transaction identifier is 4 (0x0004), the protocol identifier is 0, and the field length is 5 (0x0005), the unit identifier is 1 (0x01), the function code is 43 (0x2b), and the content is 0x0e0200 (0x0e stands for MEI to read the device identity, 0x02 reads the general product information, 0x00.
[0058] 2. The IP protocol identification module generates a message search pointer string S1="0>>22&0x3c".
[0059] 3. The TCP protocol identification module generates a message search pointer string S2="@12>>26&0x3c".
[0060] 4. The SCADA protocol reading module generates a message search pointer string. When searching for fu...
Embodiment 2
[0063] Embodiment 2: For the Modbus protocol, it is prohibited to restart the service. The command passes through the protocol protector and accurately detects the application layer content in the Modbus data packet to block. The behavior of clearing the diagnostic register value is blocked, and the request rule for filtering the modbus restart service is blocked. function 8 sub fun 01, clear Modbus diagnostic register value function8 sub fun 10:
[0064] 1. The system receives the Modbus bytes: 00 04 00 00 00 06 01 08 00 01 00 00. According to the rules, the content is parsed as follows: the transaction identifier is 4 (0x0004), the protocol identifier is 0, and the field length is It is 6 (0x0006), the unit identifier is 1 (0x01), the function code is 8 (0x08), and the subfuction is 1 (0x01).
[0065] 2. The IP protocol identification module generates a message search pointer string S1="0>>22&0x3c".
[0066] 3. The TCP protocol identification module generates a message sear...
Embodiment 3
[0070] Embodiment 3: block the behavior of clearing the value of the PLC diagnostic register, fun 8 sub fun 10 (0x0A).
[0071] 1. The protocol protection system receives an instruction from a certain address (supplementary instruction example). The Modbus byte received by the system is: 00 04 00 00 00 06 01 08 00 01 00 00. ) is 4 (0x0004), the protocol identifier is 0, the field length is 6 (0x0006), the unit identifier is 1 (0x01), the function code is 8 (0x08), and the subfuction is 1 (0x01).
[0072] 2. The IP protocol identification module generates a message search pointer string S1="0>>22&0x3c".
[0073] 3. The TCP protocol identification module generates a message search pointer string S2="@12>>26&0x3c".
[0074] 4. The SCADA protocol reading module generates a message search pointer string S3="@7>>8&0xffffff=0x08000A".
[0075] 5. The protocol protection module generates an instruction string (changed to an instruction to modify the source address) --- S4="-j DROP"....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com