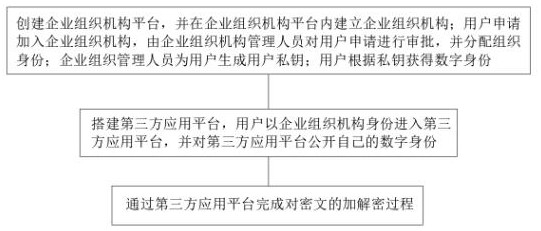
An organization identity encryption and decryption method
An encryption and decryption, identity technology, applied in user identity/authority verification, digital transmission systems, secure communication devices, etc., can solve problems such as leakage, users are not prudent in using their own information, data leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] User and authority management of traditional application systems usually uses username and password to verify user identity, and then determines the user's identity in the organization according to the user's role or group, and performs authorization and access control based on this. The following questions:
[0020] 1. The problem of repeated authentication and multi-site authentication
[0021] The identity system built by multiple heads wastes resources, but also has many obstacles in data sharing and use. The data information between different enterprise entities is stored separately and cannot be used comprehensively.
[0022] 2. Identity data privacy and security issues
[0023] User identity information is scattered in the hands of managers of various enterprises and organizations. Users are not careful enough to use their own information, or enterprises verify user identity information, which will lead to exposure of identity information and even serious violat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com