Industrial control communication encryption system and method based on load balancing
A technology of load balancing and industrial control, applied in the field of communication, can solve problems such as large increase in traffic, inconsistent data communication security index, misjudgment, etc., and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
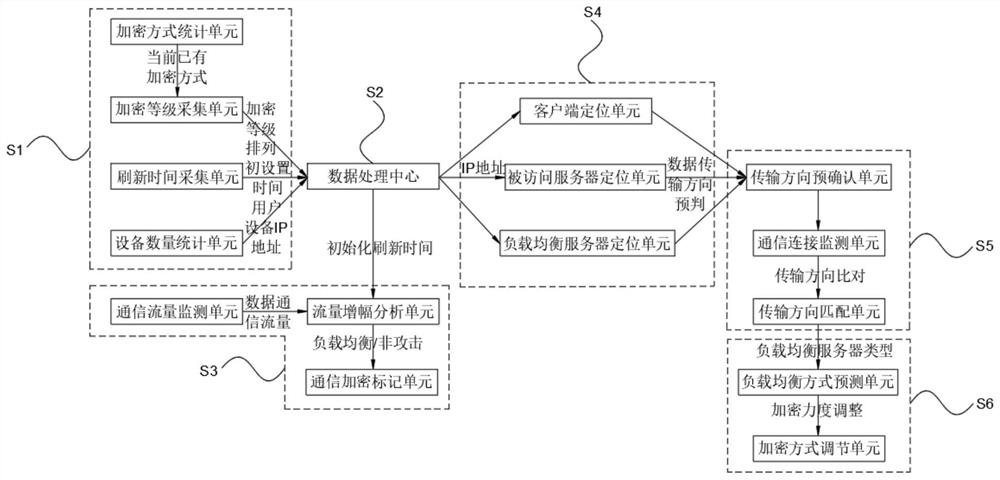
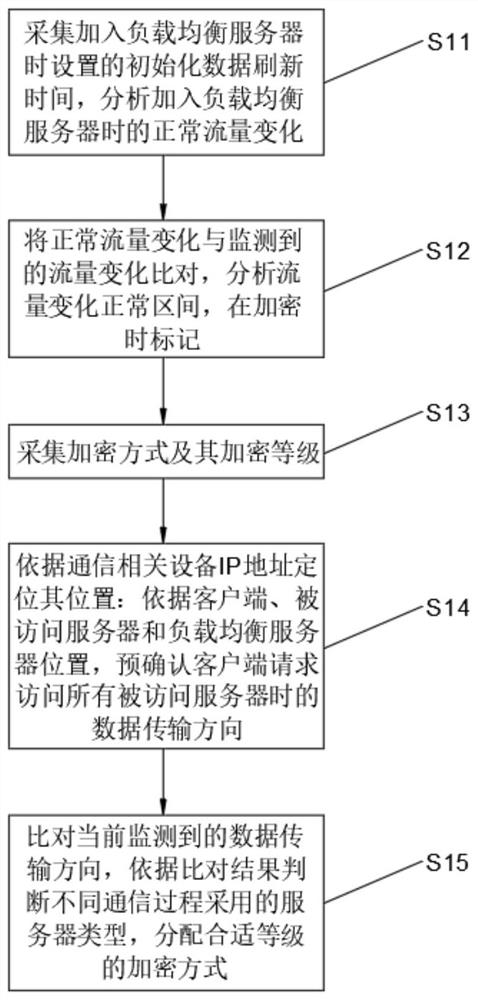
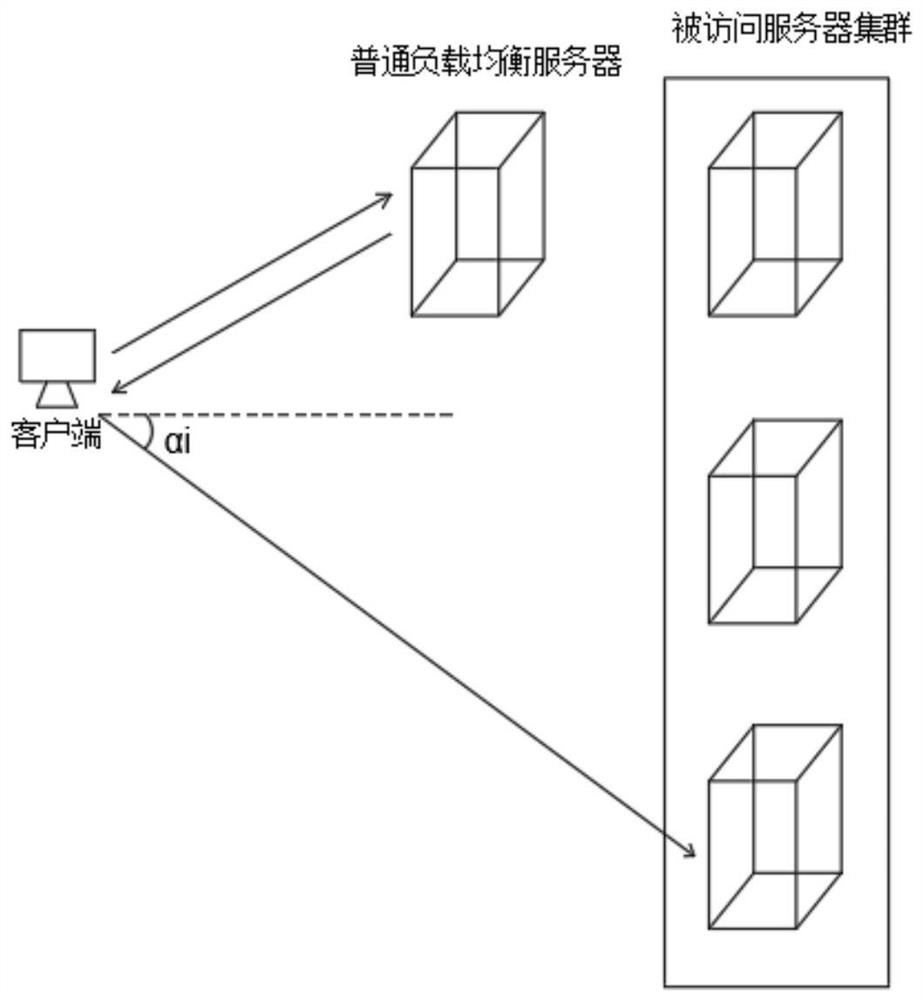
[0060] Embodiment 1: Use the encryption method statistics unit to make statistics on the currently existing encryption method set as A={A 1 , A 2 , A 3 , A 4 , A 5}, the intensity set of the corresponding encryption method collected by the encryption level acquisition unit is 2 k ={2 k1 ,2 k2 ,2 k3 ,2 k4 ,2 k5}={128, 256, 64, 32, 64}, according to the formula Calculate encryption strength benchmark value M=108, compare 2 kj and M: 2 k1 > M, 2 k2 >M, the encryption method A 1 and A 2 It is categorized into the category with high encryption level, and other encryption methods are classified into the category with low encryption level. The client positioning unit locates the location of a random client based on the IP address, and uses the client location as the origin to model the communication environment. Load balancing The location coordinates of the server are (x 负 ,y 负 )=(2, 2), the coordinate set of the accessed server is (X, Y)={(X 1 , Y 1 ), (X 2 , Y ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com