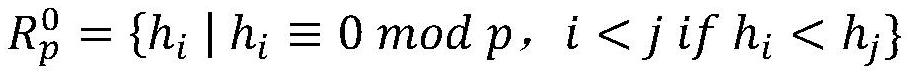Privacy-intersection-oriented data interaction method
A data interaction and privacy technology, applied in the field of data interaction, can solve the problems of complex encryption and decryption, low security, etc., and achieve the effect of avoiding security risks, high security, and narrowing the scope of comparison
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
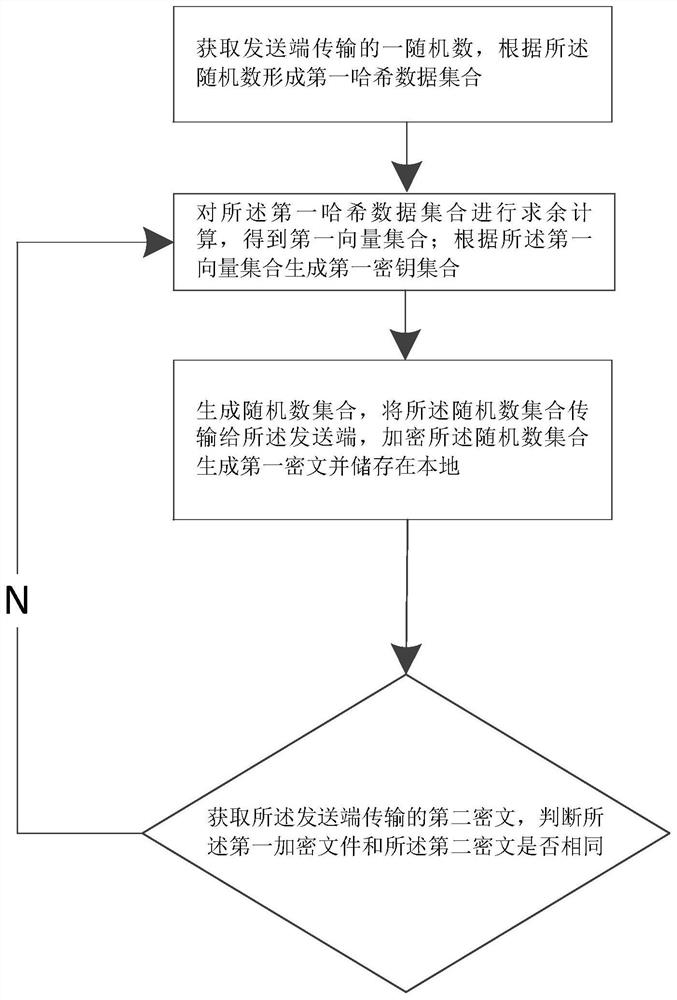
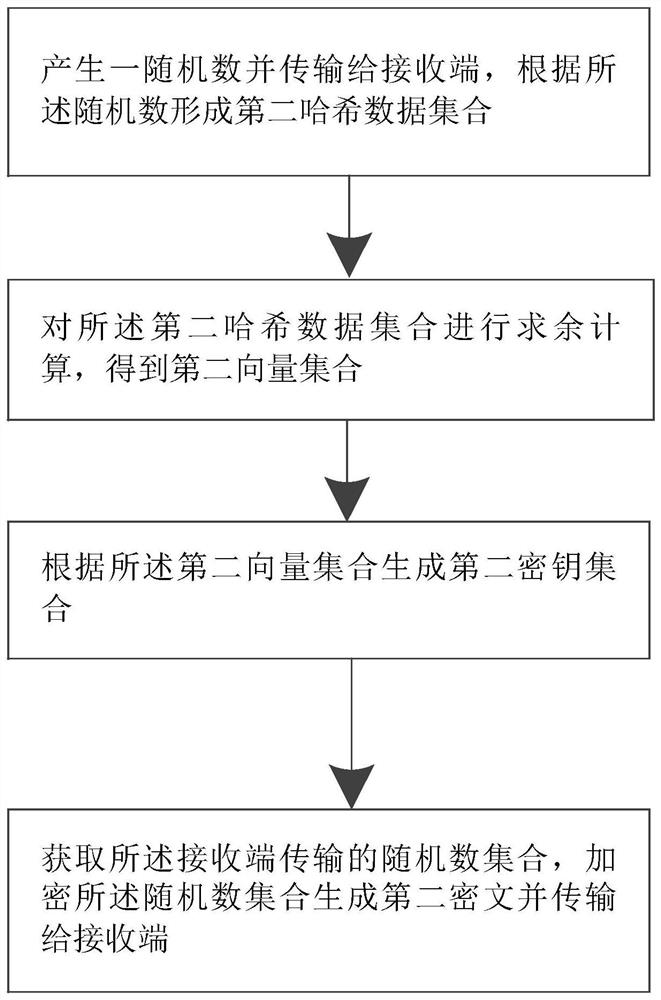
[0058] like figure 1As shown, the present embodiment includes a privacy-oriented data interaction method, including the following steps: obtaining a random number transmitted by the sending end, forming a first hash data set according to the random number; Calculate the remainder to obtain a first vector set; generate a first key set according to the first vector set; generate a random number set, transmit the random number set to the sender, encrypt the random number set to generate a first ciphertext and store it locally; Obtain the second ciphertext transmitted by the sender, and judge whether the first ciphertext and the second ciphertext are the same, and if not, repeat the remainder calculation of the first hash data set and subsequent steps.
[0059] Obtaining a random number transmitted by the sender, and forming a first hash data set according to the random number, specifically includes the following steps: obtaining a random number transmitted by the sender, using th...
Embodiment 2
[0095] A computer-readable storage medium. Computer instructions are stored on the computer-readable storage medium. When the computer instructions are executed by a processor, the steps of the method in Embodiment 1 are implemented.
[0096] Those skilled in the art should understand that the embodiments of the present invention may be provided as methods, apparatuses, or computer program products. Accordingly, the present invention can take the form of an entirely hardware embodiment, an entirely software embodiment, or an embodiment combining software and hardware aspects. Furthermore, the present invention may take the form of a computer program product embodied on one or more computer-usable storage media (including but not limited to disk storage, CD-ROM, optical storage, etc.) having computer-usable program code embodied therein.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com