Credibility modeling and verification method for industrial control network protocol
An industrial control network and verification method technology, applied in the field of reliability modeling and verification oriented to industrial control network protocols, can solve the problem that there is no credibility modeling and verification method, no credibility verification, industrial control Network untrustworthiness and other issues, to achieve the effect of verifying credibility and reducing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
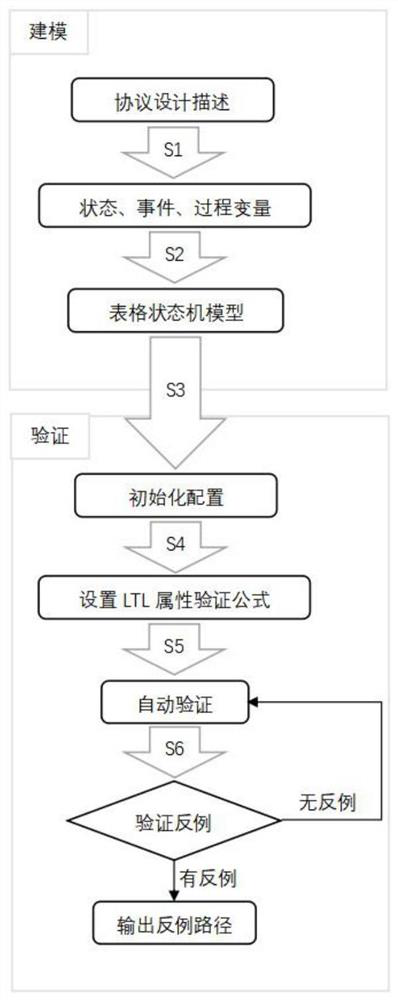
[0039] A reliability modeling and verification method for industrial control network protocols, such as figure 1 The detailed implementation steps are as follows:
[0040] S1, the protocol state, event and process variable characteristics are abstracted from the detailed description of the protocol (such as protocol specification or protocol exchange process), and the event is divided into internal events and external events. All events are interpreted as Boolean variables, meaning the event The trigger state, event variable and process variable definition statements are stored in the ram file, the first letter of the external event variable name begins with x, and the other variable names begin with non-x letters.
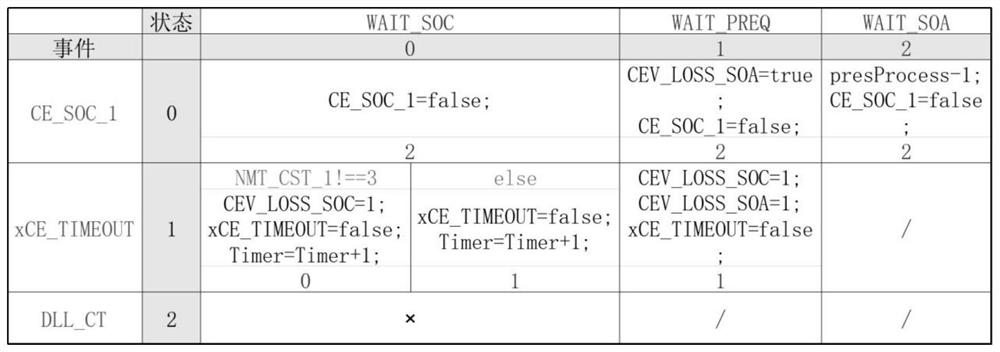
[0041] S2, fill in the abstracted protocol features into the table, and divide the cell in the form of an N-S graph if there is an alternative branch in a certain cell. The cell is divided into two parts: the execution interval and the state jump interval. The e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com