Data encryption or decryption method, device and system
A data encryption, encryption and decryption technology, applied in the computer field, can solve the problems that affect the efficiency of data processing, and the processing capacity cannot meet the delay of data encryption or decryption processing, so as to achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
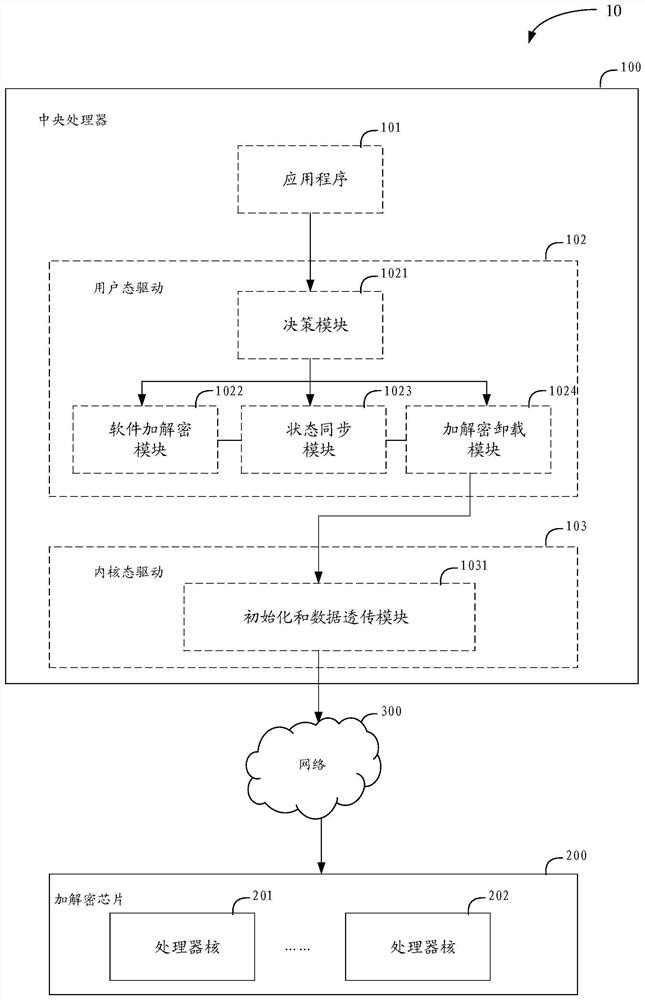
[0036] For ease of understanding, the terms involved in this application are explained first.
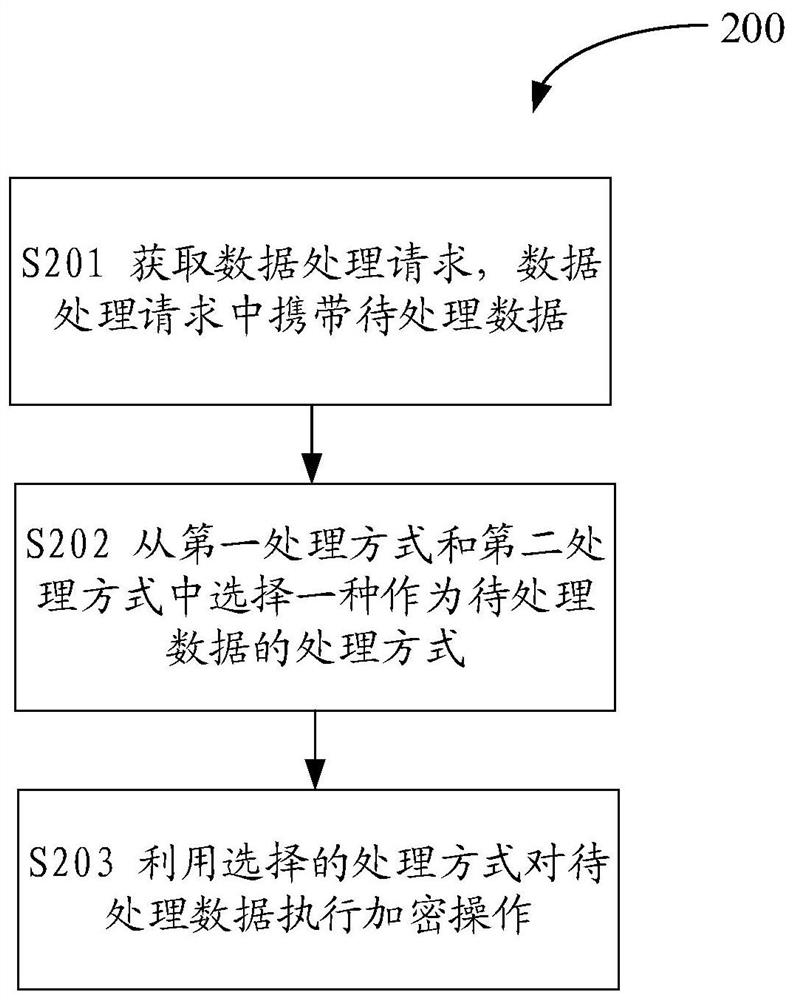
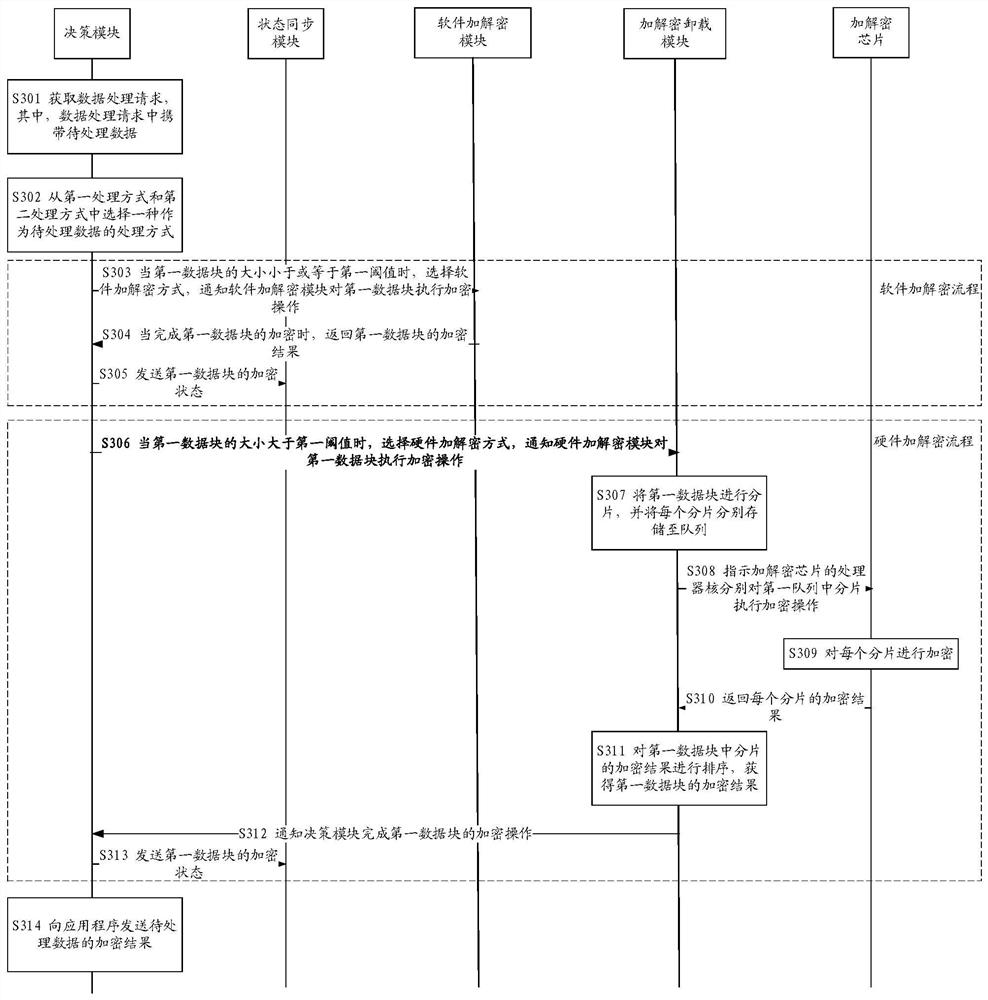
[0037] Stream cipher (stream cipher), also known as data stream encryption, is a symmetric encryption and decryption (also called encryption or decryption) algorithm. Specifically, each execution subject that performs encryption or decryption uses the same key, for example, a pseudo-random encrypted data stream (pseudo-random stream) is used as a key, and the encrypted execution subject uses the key to treat encrypted data (also called plaintext data ) encryption to obtain the encrypted result of the data to be encrypted (also called ciphertext data). Correspondingly, after obtaining the ciphertext data, the decryption subject can use the same key to decrypt the ciphertext data. For example, taking the symmetric encryption and decryption algorithm as block cipher (also known as block cipher or block cipher) as an example, the execution subject of encryption and decryption can divid...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com