IPv6 network intrusion detection method and system based on data mining technology
A technology of network intrusion detection and intrusion detection, applied in the direction of transmission system, electrical components, etc., can solve the problems that the host and network cannot be detected, and the data packets that cannot be encrypted cannot be detected, so as to simplify the detection complexity and improve the intrusion detection ability , the effect of improving the detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
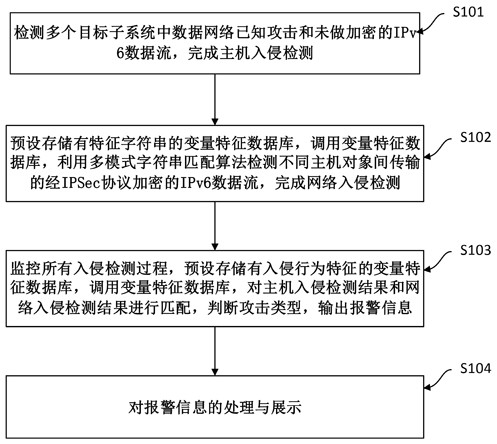
[0055] Embodiment 1: as attached figure 1 As shown, the embodiment of the present invention discloses a kind of IPv6 network intrusion detection method based on data mining technology, comprising:
[0056] Step S101, detecting known attacks on the data network and unencrypted IPv6 data streams in multiple target subsystems to complete host intrusion detection;
[0057] Here, the host intrusion detection is mainly to perform security detection on log files, misoperation behaviors, redundant data, etc. in the IPv6 network, so as to ensure the interconnection and intercommunication of data between hosts.
[0058] Step S102, presetting the variable feature database stored with feature strings, calling the variable feature database, using a multi-mode string matching algorithm to detect IPv6 data streams encrypted by the IPSec protocol transmitted between different host objects, and completing network intrusion detection;
[0059] Here, the IPv6 data stream encrypted by IPSec prot...
Embodiment 2
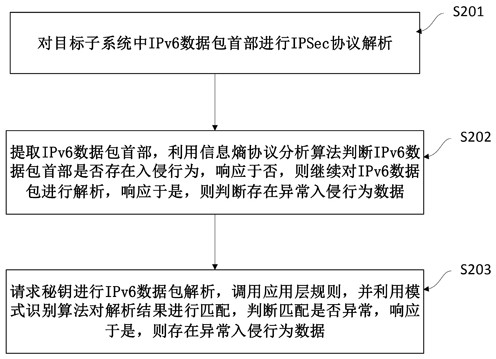
[0064] Embodiment 2: as attached figure 2 As shown, the embodiment of the present invention discloses a kind of IPv6 network intrusion detection method based on data mining technology, wherein detection of known attacks on data networks in multiple target subsystems and unencrypted IPv6 data streams further includes:
[0065] Step S201, performing IPSec protocol analysis on the IPv6 packet header in the target subsystem; where the IPv6 packet in the target subsystem is the host IPv6 packet;
[0066] Step S202, extracting the header of the IPv6 data packet, using the information entropy protocol analysis algorithm to determine whether there is an intrusion behavior in the header of the IPv6 data packet, if the response is no, continue to analyze the IPv6 data packet, and if the response is yes, it is judged that there is abnormal intrusion behavior data;
[0067] Here, step S202 specifically includes:
[0068] 1. Extract the IPv6 packet header;
[0069] 2. Calculate its corr...
Embodiment 3
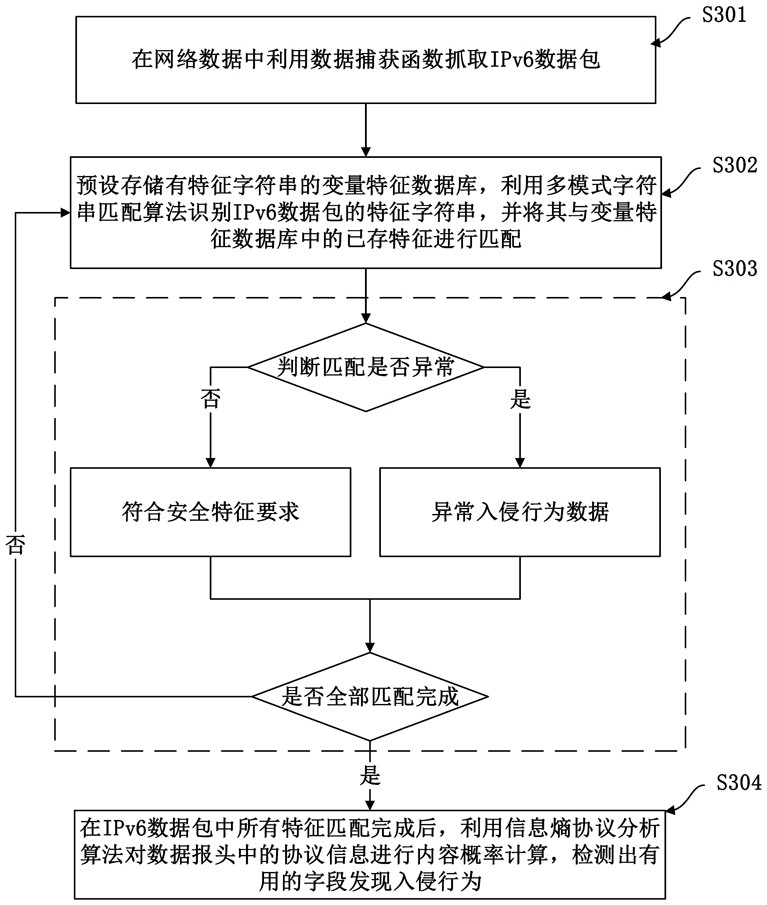
[0075] Embodiment 3: as attached image 3 , 4 As shown, the embodiment of the present invention discloses an IPv6 network intrusion detection method based on data mining technology, in which a variable feature database storing feature strings is preset, the variable feature database is called, and a multi-pattern string matching algorithm is used to detect different hosts The IPv6 data flow encrypted by the IPSec protocol transmitted between objects further includes:
[0076] Step S301, using a data capture function to capture IPv6 data packets in network data, wherein the data capture function includes filtering rules in data address format;
[0077] Here specifically include:
[0078] 1. Use the data capture function to capture IPv6 data packets in the network data;
[0079] 2. Obtain the network address and mask information from the IPv6 data packet, compare the network address and mask information with the filtering rules of the data address format, extract the consiste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com