Illegal application software identification method and device, medium and electronic equipment
A technology of application software and identification method, which is applied to electrical components, transmission systems, digital data authentication, etc., can solve the problems of low software identification rate and failure to obtain application type fields, etc., and achieve the effect of improving detection rate and accuracy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
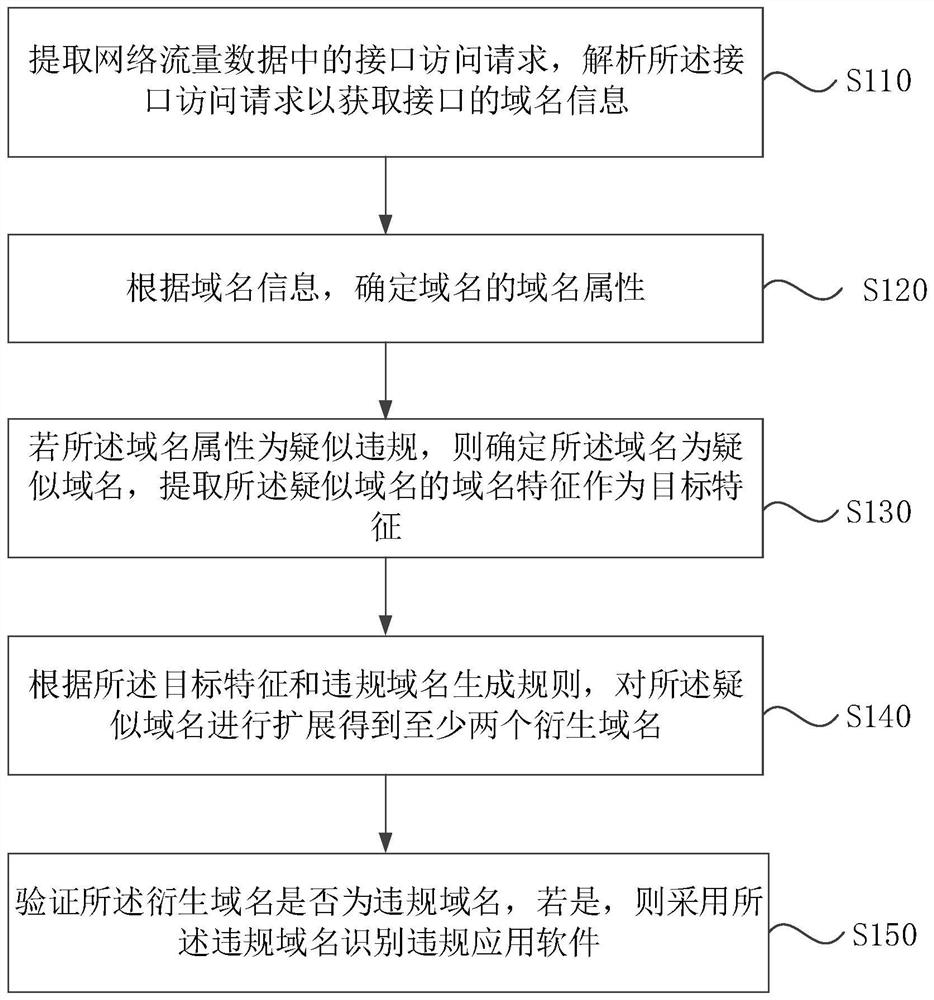
[0028] figure 1 It is a flow chart of a illegal application software identification method according to the embodiment of the present application, and this embodiment can be applied to the case of identifying the illegal application software. The method can be performed by the illegal application software recognition apparatus provided in the present application embodiment, which can be implemented by software and / or hardware, and can be integrated into the electronic device running this system.
[0029] like figure 1 As shown, the illegal application software recognition method includes:
[0030] S110, extract interface access requests in network traffic data, parse the interface access request to obtain domain information of the interface.
[0031] Among them, the network traffic data is passed through the capture tool, which is intercepted to send and receive data packets transmitted in network transmission. Network traffic data may include an interface access request, where...
Embodiment 2
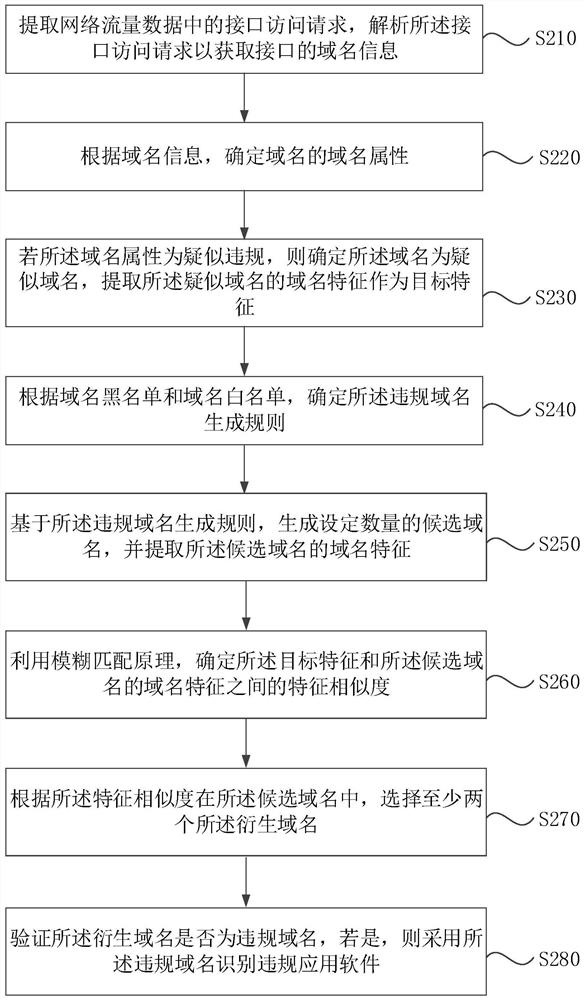
[0065] figure 2 The present application is a flowchart of another method of identifying illegal application software according to a second embodiment. This embodiment will be further optimized based on the above-described embodiments. Specifically optimized according to the characteristics and the target domain name generation rule violation, the pseudo domain to obtain at least two extended-derived domain, comprising: domain according to the domain whitelist and blacklist, determining the domain name generation rule violation; based on the wherein similarity between the domain characteristic fuzzy matching principle, characterized in determining the target candidate and the domain name;; said domain name generation rule violation, generating a set number of candidates domain, and extracts the candidate feature of the domain name the feature similarity domain at the candidate selecting at least two of the domain name is derived.
[0066] like figure 2 As shown in the illegal appl...
Embodiment 3
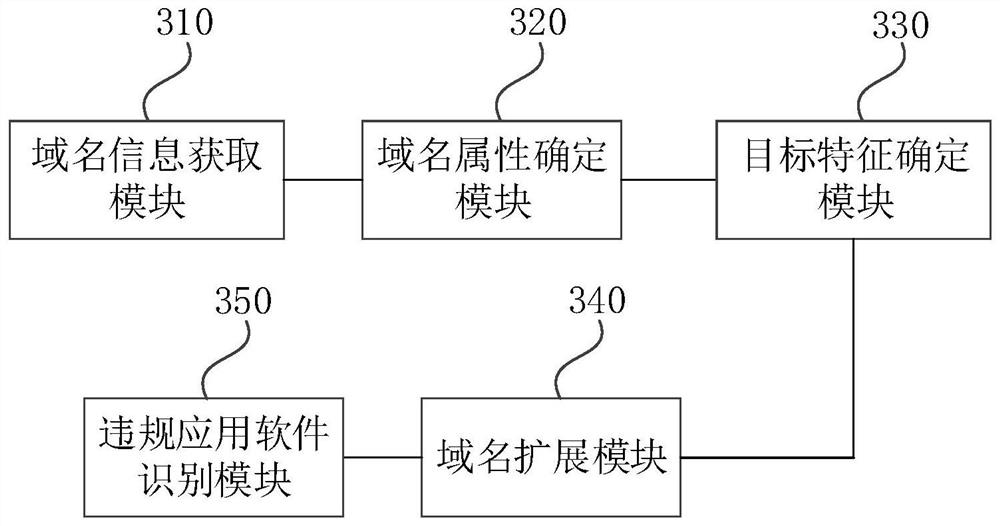
[0086] image 3 It is an illegal application software identification device provided in the third embodiment of the present application, which may be applied to the case where the illegal application software is identified. The device can be implemented by software and / or hardware and can be integrated into an electronic device such as a smart terminal.
[0087] like image 3 As shown, the apparatus can include: domain name information acquisition module 310, domain name property determining module 320, target feature determination module 330, domain name extension module 340, and illegal application software identification module 350.
[0088] Wherein, the domain information acquisition module 310 is used to extract interface access requests in network traffic data, parse the interface access request to obtain domain name information of the interface;
[0089] The domain name property determines module 320 for determining the domain name attribute of domain names based on domain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com