Access authentication method, authentication server and system based on MQTT protocol
A technology of authentication server and authentication method, applied in transmission systems, digital transmission systems, instruments, etc., can solve problems such as uselessness and spam, and achieve the effect of preventing confusion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
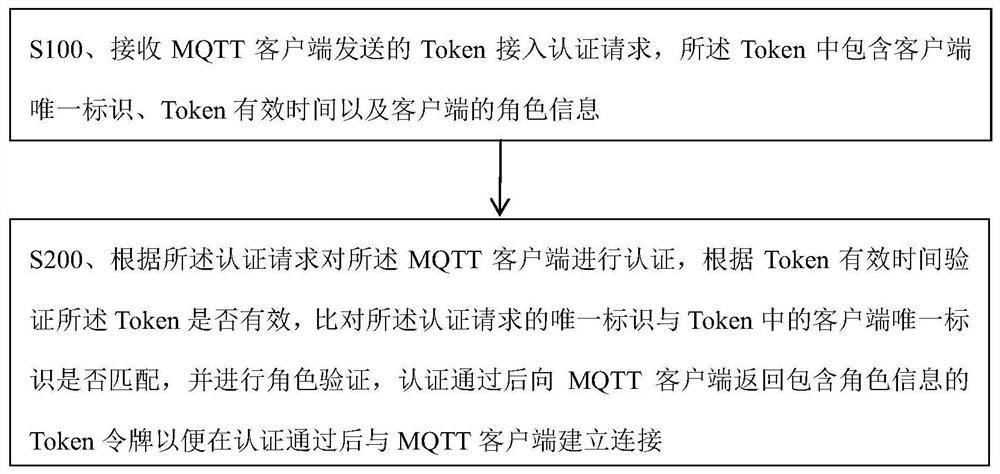
[0027] like figure 1 As shown, this embodiment proposes an access authentication method based on the MQTT protocol, the method is executed by an authentication server, and the authentication server is an IDS4 authentication server. Specifically, the method includes:
[0028] S100. Receive a Token access authentication request sent by an MQTT client, where the Token includes a unique identifier of the client, valid time of the Token, and role information of the client.
[0029] The MQTT client includes a message publisher and a message subscriber. The message publishing end and the message subscribing end perform message publishing and obtain subscription messages pushed by the server respectively according to the subscription topic.
[0030] Further, the method further includes: assigning a unique identifier to the MQTT client device by the IDS4 authentication server.
[0031] In this embodiment, the access authentication request is generated based on the access key, the enc...
Embodiment 2
[0038] Corresponding to Embodiment 1 above, this embodiment proposes an authentication server, where the authentication server includes:
[0039] The authentication request receiving module is used to receive the Token access authentication request sent by the MQTT client, and the Token includes the unique identification of the client, the effective time of the Token and the role information of the client;
[0040] The client authentication module is used to authenticate the MQTT client according to the authentication request, verify whether the Token is valid according to the valid time of the Token, and compare whether the unique identifier of the authentication request and the unique identifier of the client in the Token Match and perform role verification. After the authentication is passed, a Token token containing role information is returned to the MQTT client to establish a connection with the MQTT client after the authentication is passed.
[0041] The functions perfo...
Embodiment 3
[0043] Corresponding to the above embodiments, this embodiment proposes a computer storage medium, which contains one or more program instructions, and one or more program instructions are used to be executed by an access authentication system based on the MQTT protocol As the method of embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com