Chain code management method and device of alliance chain and terminal equipment
A management method and chain code technology, applied in the chain code management method, device and terminal equipment field of the alliance chain, can solve the problem of low reliability of container management corresponding to the chain code, improve management reliability, and achieve simple and simple interception operations. Easy to combine effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
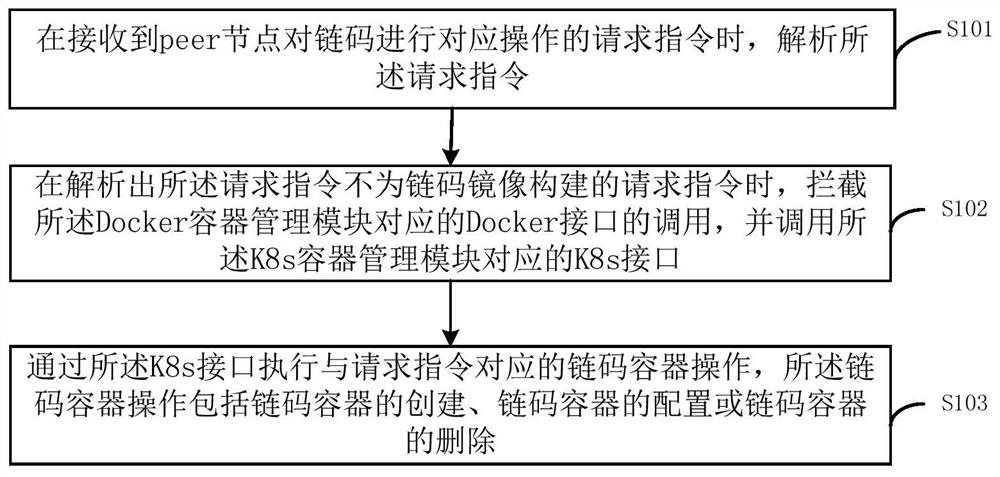
[0056] This embodiment provides a chain code management method of an alliance chain, which is applied to a chain code management system. The chain code management system includes a Docker container management module created based on Docker container technology, and the chain code management system includes K8s based on K8s container technology. Container management modules such as figure 1 As shown, the method includes steps S101 to S103:
[0057] Specifically, the Docker container management module is used to run the chaincode container of the alliance chain based on the docker service, and the K8s container management module of the K8s container technology is used to use the Kubernetes platform to realize the operation method of the chaincode container. The operation method of the chain code container includes creating, running, shutting down or removing the chain code container, etc. The K8s container management module is also used for accessing the K8s API provided by the...
Embodiment 2
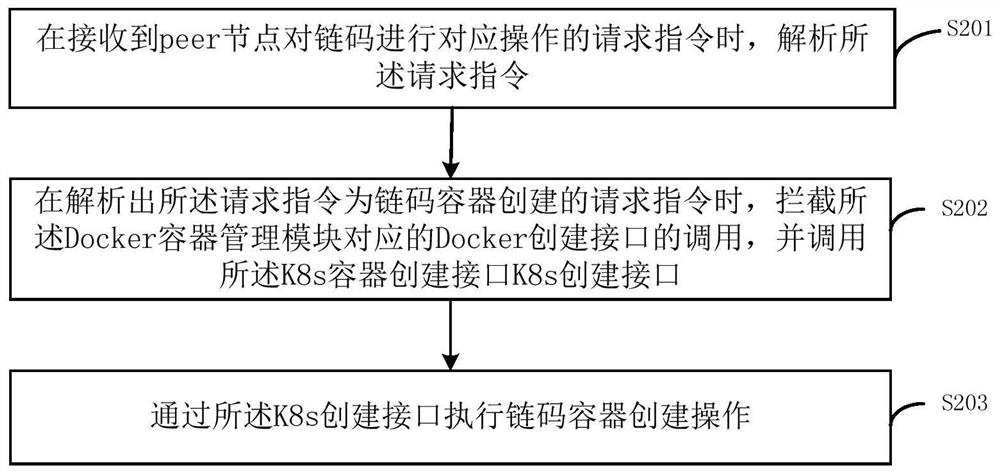
[0069] This embodiment is a further description of Embodiment 1. For the same or similar parts as Embodiment 1, please refer to the relevant description of Embodiment 1 for details, and details will not be repeated here. Such as figure 2 As shown, the above step S102 includes step S202, and step S103 includes step S203. The chain code management method of the consortium chain provided by the embodiment of the present application includes:
[0070] Step S201, when receiving a request instruction from a peer node to perform a corresponding operation on the chain code, analyze the request instruction.
[0071] Specifically, where step S201 is the same as or similar to the above-mentioned step S101, please refer to the relevant description of step S101 for details, and details are not repeated here.
[0072] Step S202, when parsing out that the request instruction is a request instruction for chaincode container creation, intercept the invocation of the Docker creation interface...
Embodiment 3
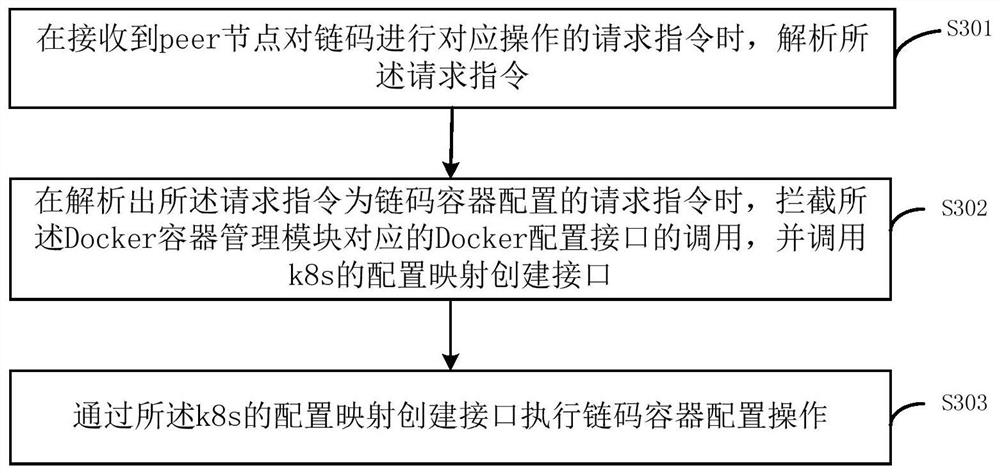
[0084] This embodiment is a further description of Embodiment 1. For the same or similar parts as Embodiment 1, please refer to the relevant description of Embodiment 1 for details, and details will not be repeated here. Such as image 3 As shown, the above step S102 includes step S302, and step S103 includes step S303. The chain code management method of the consortium chain provided by the embodiment of the present application includes:
[0085] Step S301, when receiving a request instruction from a peer node to perform a corresponding operation on the chain code, analyze the request instruction.
[0086] Specifically, where step S301 is the same as or similar to the above-mentioned step S101, please refer to the relevant description of step S101 for details, and details are not repeated here.
[0087] Step S302, when parsing out that the request instruction is a request instruction for chaincode container configuration, intercept the invocation of the Docker configuration ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com