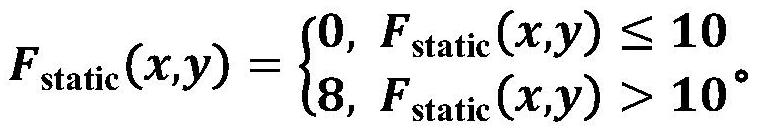A method for detecting the loss of items in security monitoring
A loss detection and security monitoring technology, applied in image analysis, image enhancement, instruments, etc., can solve the problems of poor background modeling, false positives and false negatives, the time required for the foreground and the uncertainty of the foreground duration, etc., to achieve The effect of overcoming the effect of motion occlusion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0039] Embodiment: a method for detecting items left behind and lost in security monitoring.
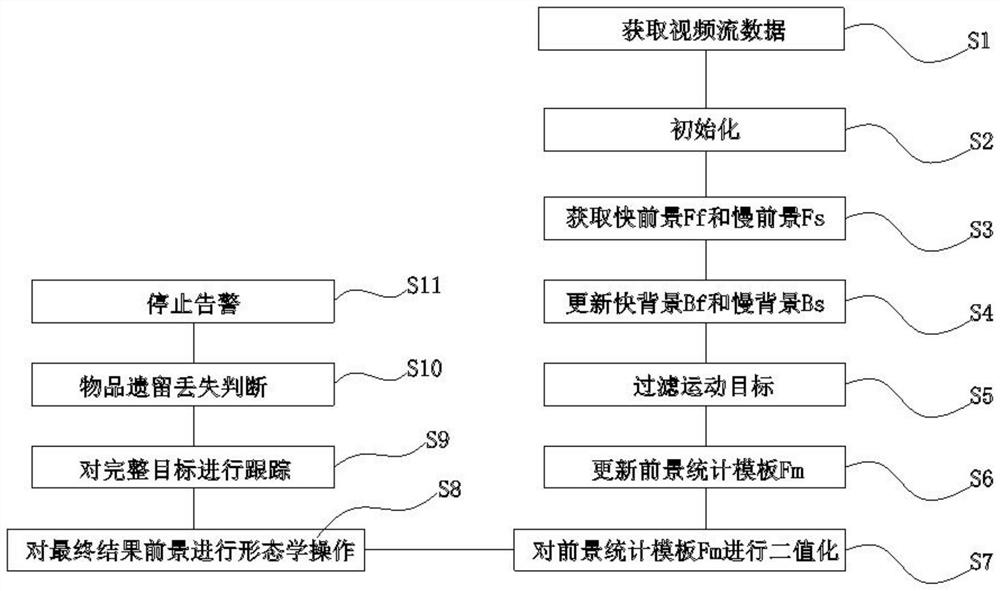
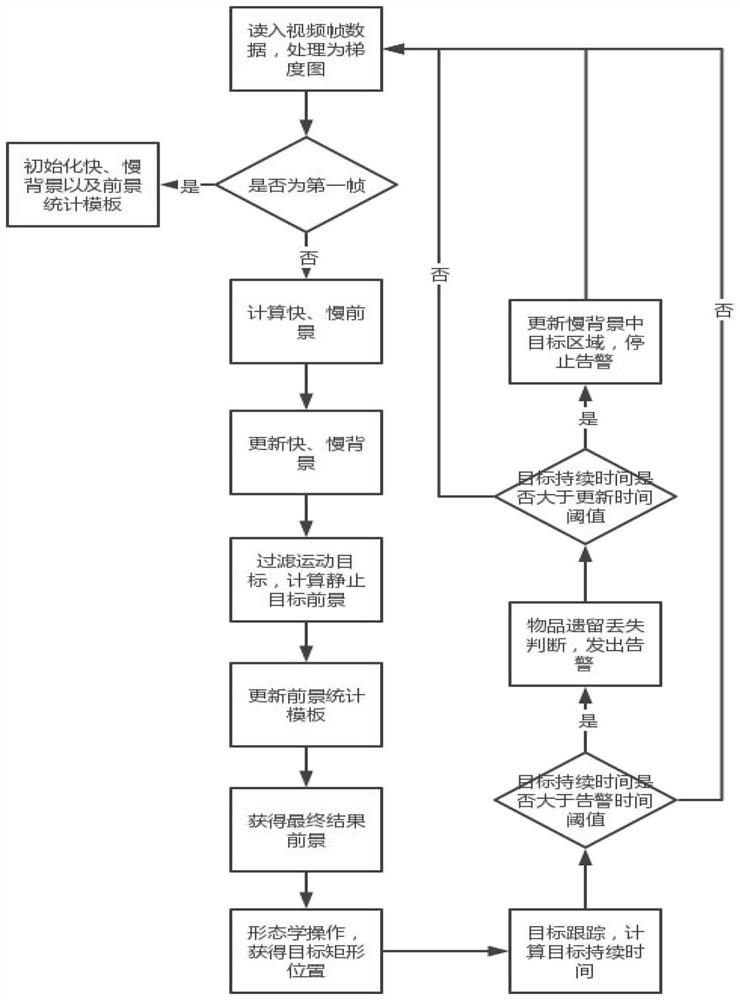
[0040] refer to figure 1 with figure 2 As shown, a method for detecting the loss of items in security monitoring, specifically includes the following steps:
[0041] S1. Obtain video stream data: read in each frame of image I in sequence s , if the image size is large, appropriate scaling can be performed on the premise of meeting the detection accuracy requirements, which will help reduce performance consumption, and then process the image I by using an edge detection operator such as a Sobel operator s Get the gradient map I g , one of the benefits of using a gradient map is that it can avoid the problem of false positives caused by care changes in the scene to a certain extent.
[0042] S2, initialization, use the gradient map I of the first frame g Initialize fast background B f and slow background Bs, ie B f =I g , B s =I g , and at the same time initialize a foregrou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com