Device and method for generating SM2 signature private key capable of secretly sharing and hiding identity
A technology for generating device and secret sharing, which is applied in the field of cryptographic engineering and can solve the problems of limited computing power of terminals, difficulty in protecting secure data, and difficulty in protecting signature private keys.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The device and method for generating a secret-shared hidden identity SM2 signature private key of the present invention will be further described in detail in conjunction with the embodiments below.
[0030] The hidden identity SM2 signature private key generation device of the present invention can verify the identity and timeliness of the digital certificate corresponding to the private key of the client in an offline manner, and at the same time support the splitting of the private key into two parts, one for storage On the client side, another copy is stored on the server side, and the data is signed by means of joint signature.
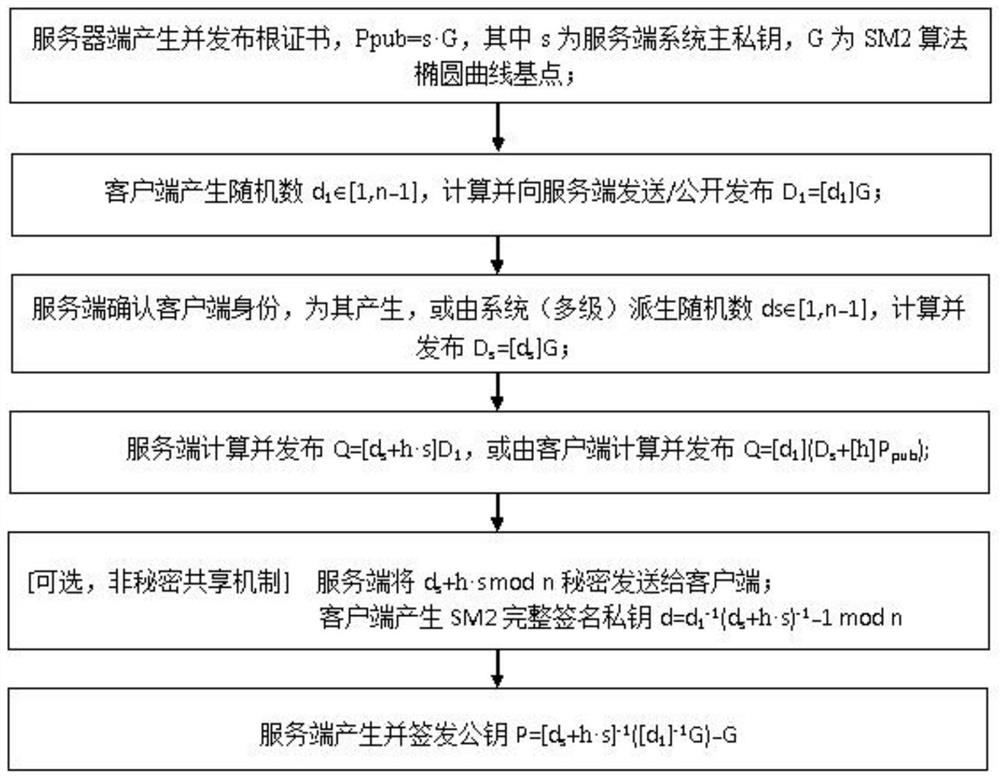
[0031] figure 1 It is a diagram of the generation process of the SM2 signature public and private key that hides the identity of the client in the present invention.
[0032] The specific process is as follows:
[0033] Step 1: The server generates and publishes the root certificate, P pub =s G, where s∈[1,n-1], s is the master private ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com