Malicious code detection method for safety protection of power enterprise
A malicious code detection and security protection technology, applied in neural learning methods, computer security devices, platform integrity maintenance, etc., can solve problems such as weak protection capabilities, and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be described in further detail in conjunction with the specific implementation of the accompanying drawings.
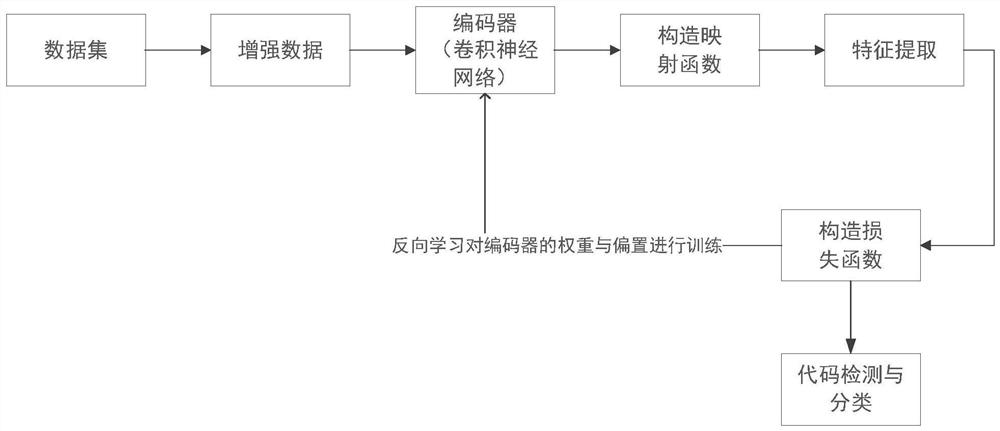
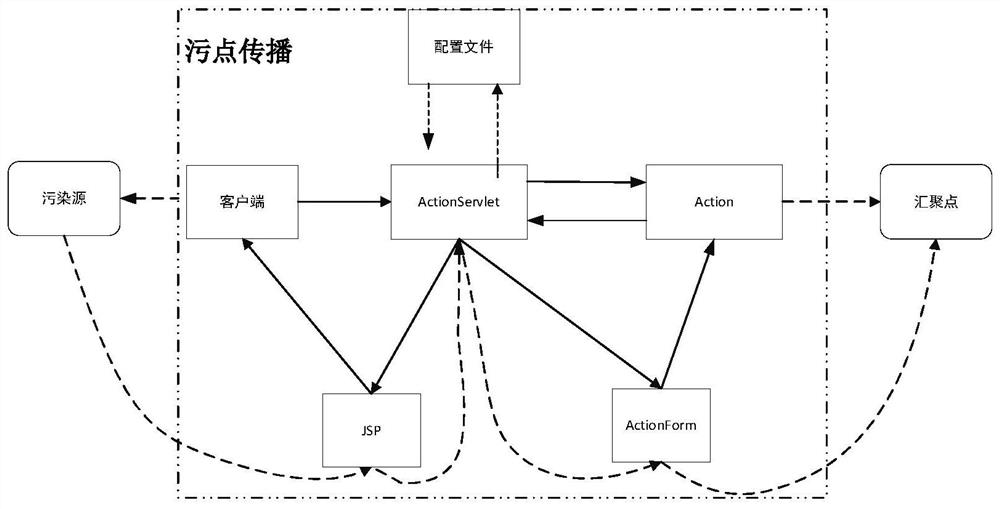
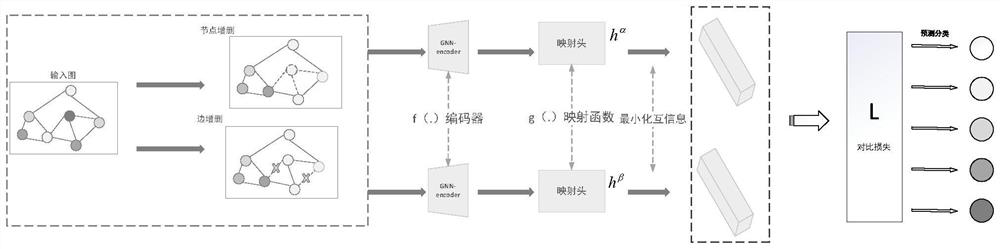
[0035] Such as figure 1As shown, aiming at the problem of weak protection ability of power enterprise security protection, the present invention proposes a malicious code detection method suitable for enterprise security protection, analyzes the instruction set generated by the system program, and according to the characteristics of the data and the instruction set, Use the taint propagation analysis algorithm to taint the instruction set, build a behavior dependency graph, enhance the constructed behavior dependency graph, construct positive and negative samples, and generate enough samples by comparing and learning the positive and negative sample data. Then the newly generated sample data and the original data set are combined to form an enhanced data set; then a differentiable classification algorithm is used to estimate the proba...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com