Digital asset management method capable of realizing anonymous transaction
A technology of digital assets and management methods, applied in digital data processing, digital data protection, instruments, etc., can solve problems such as inability to distinguish user account information from user usage data, personal sensitive data leakage, etc., and achieve high computing power requirements, The effect of low concurrency and low scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
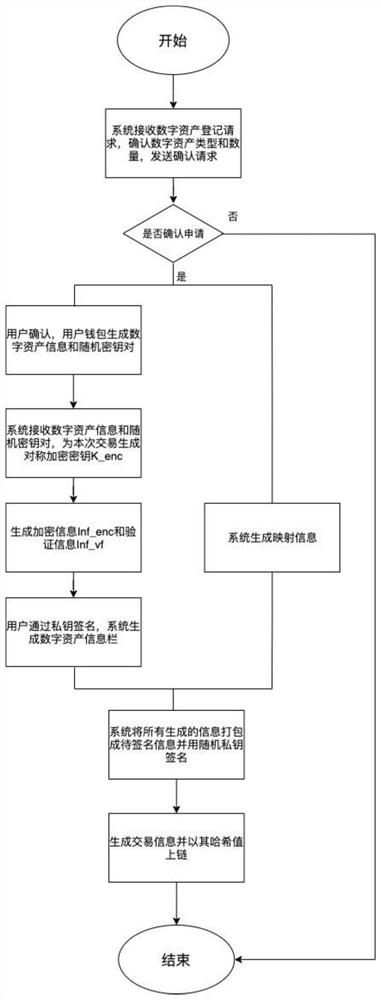
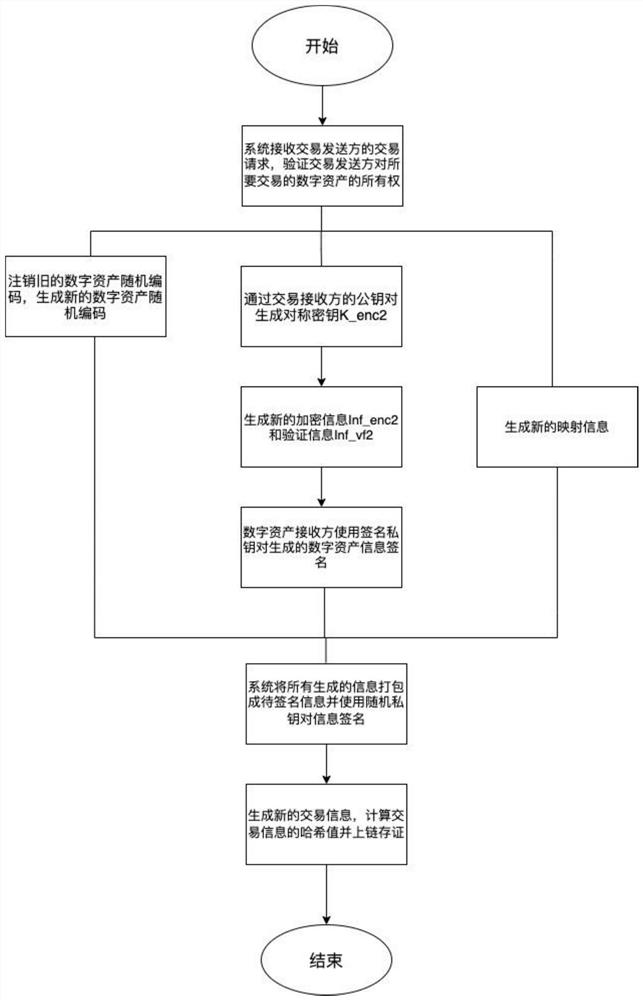
[0065] Embodiment 1: A digital asset management method that can realize anonymous transactions, such as figure 1 and figure 2 shown, including the following steps: including the following steps:
[0066] Obtain the asset owner registration request, and when receiving the asset owner's registration request, obtain a unique seed and store it in the asset owner's wallet;
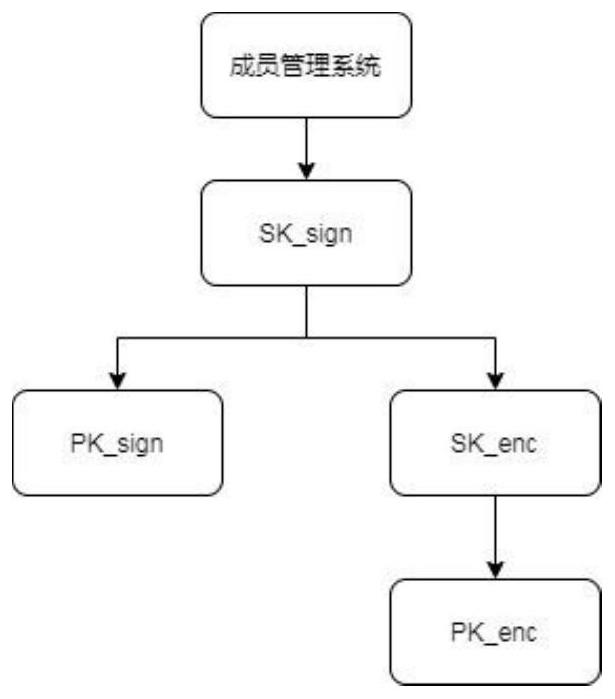
[0067] Using the unique seed to derive two key pairs, the two key pairs are the user signature key pair and the user transaction key pair;
[0068] Obtain a digital asset registration request, generate digital asset information, and use the user transaction key pair and random key pair to generate a symmetric key;
[0069] Encrypting the digital asset information with the symmetric key and the user signature key pair to generate first verifiable information and first encrypted information;
[0070] Casting the digital asset information into the first NFT, generating the first transaction information and upl...
Embodiment 2
[0146] Embodiment 2: A digital asset management device that can realize anonymous transactions, including
[0147] User registration module: obtains the registration request of the asset owner, and when receiving the registration request of the asset owner, obtains a unique seed and stores it in the wallet of the asset owner; derives two key pairs from the unique seed , the two described key pairs are respectively the user signature key pair and the user transaction key pair;
[0148] Digital asset registration and verification module: obtain digital asset registration request, and generate digital asset information, use the user transaction key pair and random key pair to generate a symmetric key; use the symmetric key and the user signature key Encrypting the digital asset information to generate first verifiable information and first encrypted information; casting the digital asset information into the first NFT, generating the first transaction information and upload...
Embodiment 3
[0151] Embodiment 3: An electronic device for digital asset management that can realize anonymous transactions, comprising: a memory and a processor, the processor and the memory communicate with each other through a bus; The program instructions executed by the processor can be invoked by the processor to execute the method described in any one of Embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com