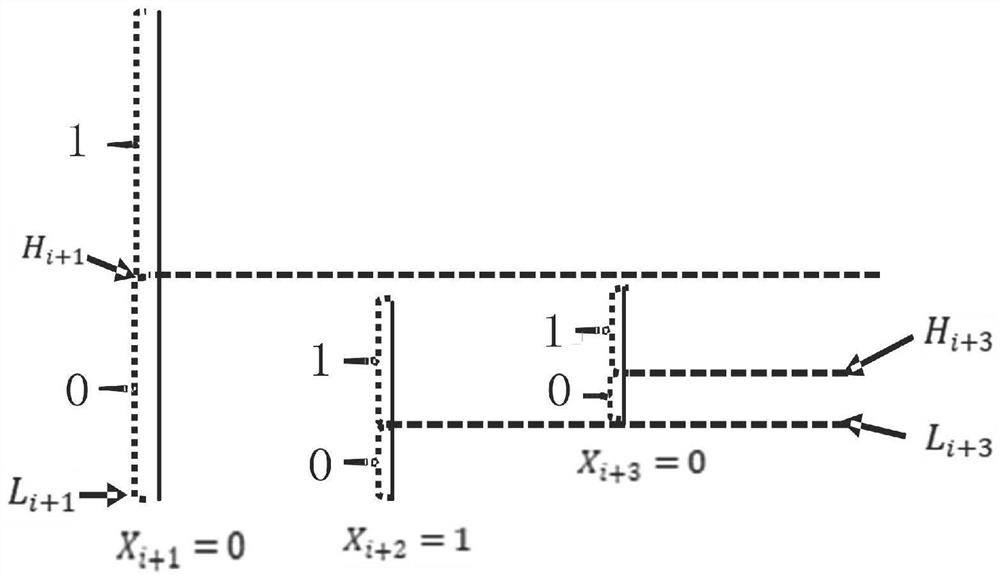A coding method, device, medium and electronic device for preventing quantum attack
A coding method, quantum technology, applied in the field of communication coding, can solve problems such as being unable to resist quantum attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
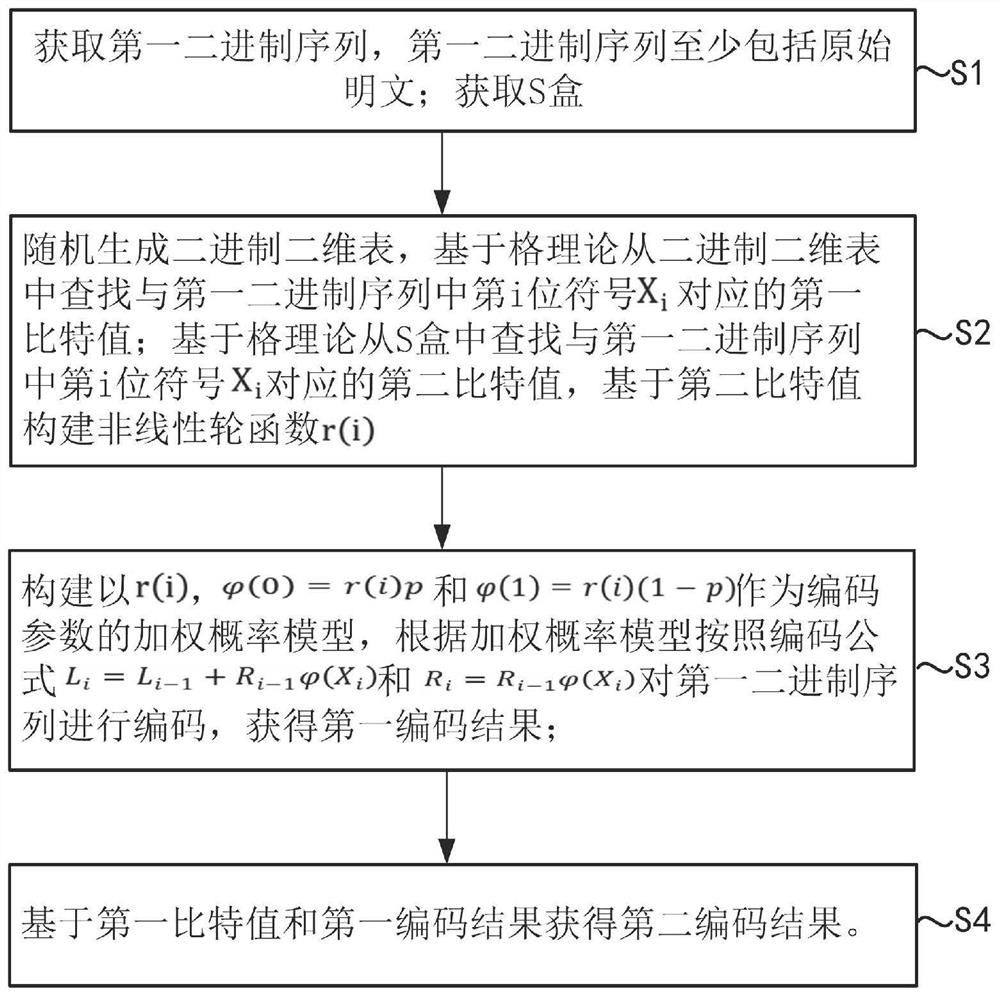
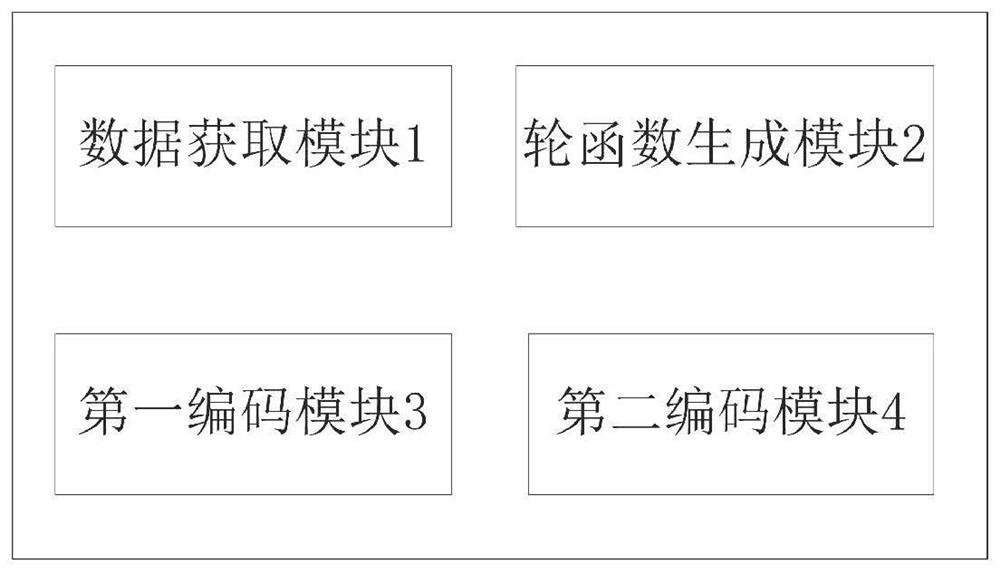
[0108] The first embodiment of the present invention provides an encoding system for preventing quantum attacks. The system includes an encoding end and a decoding end. The embodiment of the present invention does not impose any restrictions on the encoding end and the decoding end. The encoding end and the decoding end can be For arbitrary terminals such as computers and servers, the encoding end implements a quantum attack-proof encoding method. The decoding end implements a quantum attack-proof decoding method, and the decoding method is the inverse process of the encoding method. For ease of understanding, before introducing the method, the round function of the nonlinear weighting coefficient used in the method is introduced.
[0109] First, the round function of the nonlinear weighting coefficient;
[0110] Let the input password (Passwords) have L (L≥6) bytes in total, n is the number of bytes in the sequence X, and B(j) is the jth (j=1, 2, ..., L) word of the password...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com