Asset vulnerability management method and device, electronic equipment and storage medium
A vulnerability management and vulnerability technology, which is applied in the field of network security, can solve problems such as heavy workload of relevant personnel, low efficiency of vulnerability repair, and asset and equipment security issues, so as to improve asset security, improve repair efficiency, and reduce property losses. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
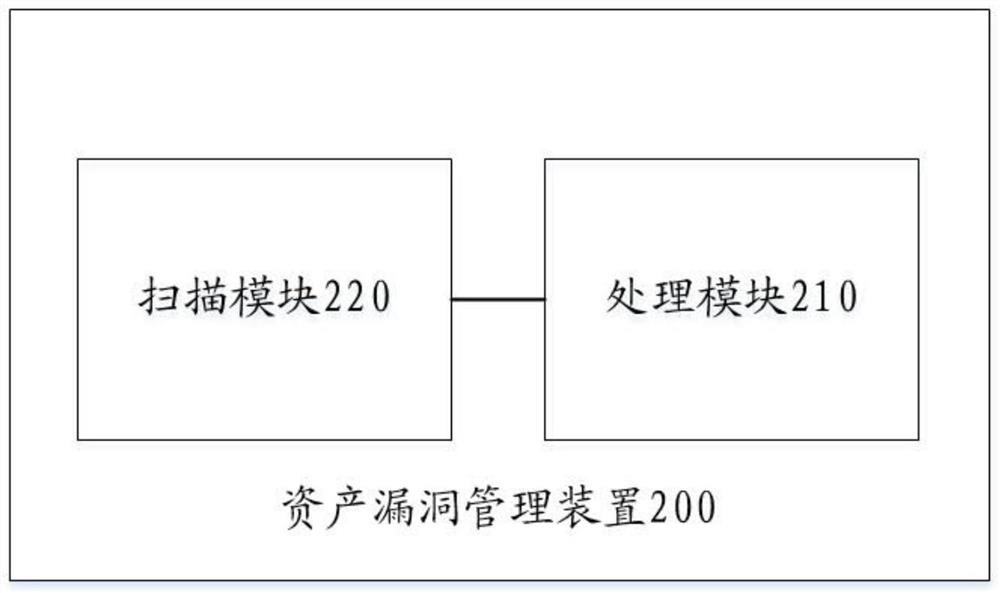
Image
Examples
Embodiment Construction
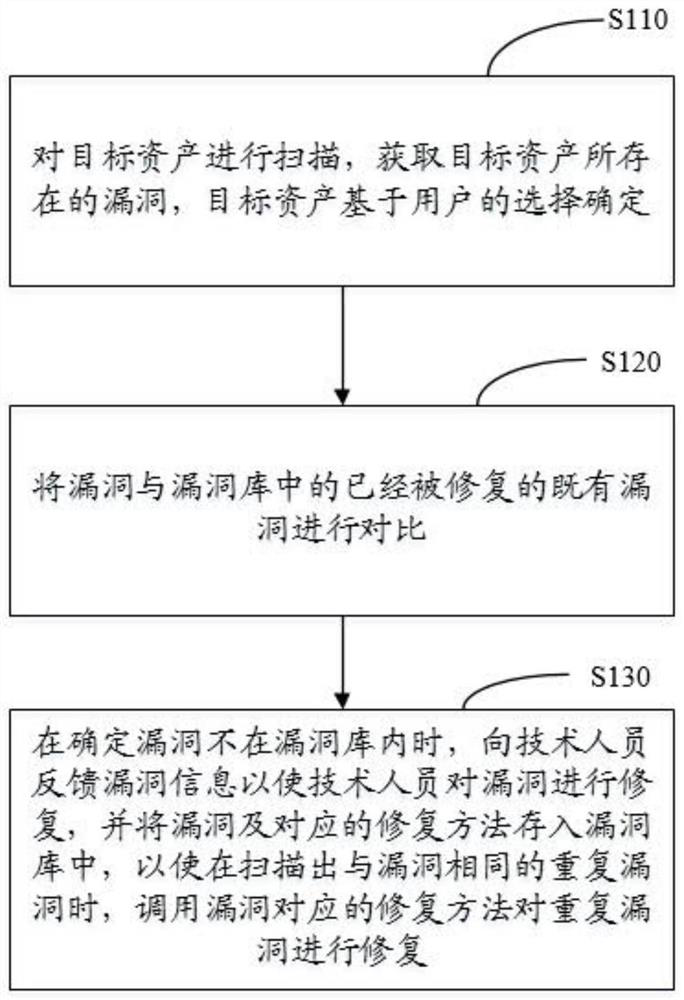
[0029] In order to make the purpose, technical solution and advantages of the present application clearer, the present application will be further described in detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present application, and are not intended to limit the present application.
[0030] Assets refer to various forms of equipment, systems, software, etc. owned by the company, such as computers, servers, operating systems, databases, etc. All kinds of assets usually store various materials, documents, etc. of the company, and when assets appear When there is a security breach, it may be invaded, resulting in the leakage of the company's data and data, and bringing property losses to the company. Therefore, it is necessary to scan the assets regularly and repair the existing loopholes.
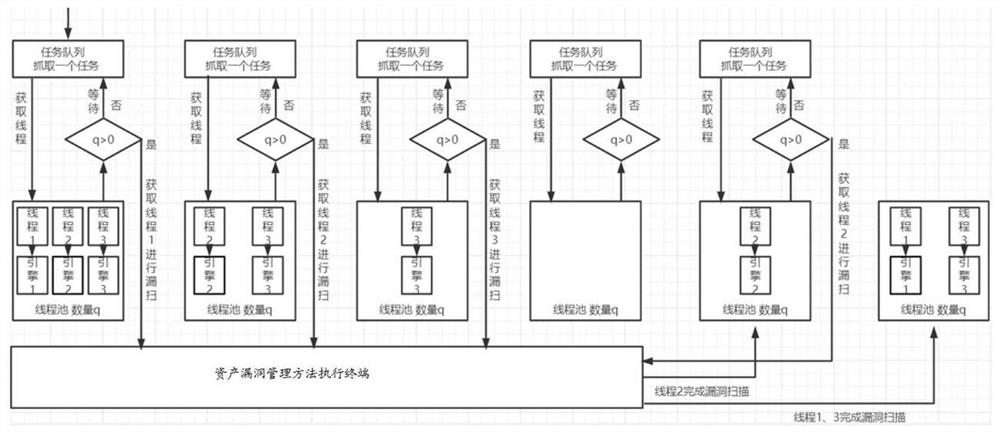
[0031] Vulnerability scanning can use some scripts to detect ope...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com