Multi-node vulnerability scanning method and device, electronic equipment and storage medium
A vulnerability scanning and multi-node technology, applied in the field of network security, can solve the problems of inaccurate vulnerability scanning, etc., and achieve the effect of reducing the risk of network security vulnerabilities, avoiding attacks, and fast scanning speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
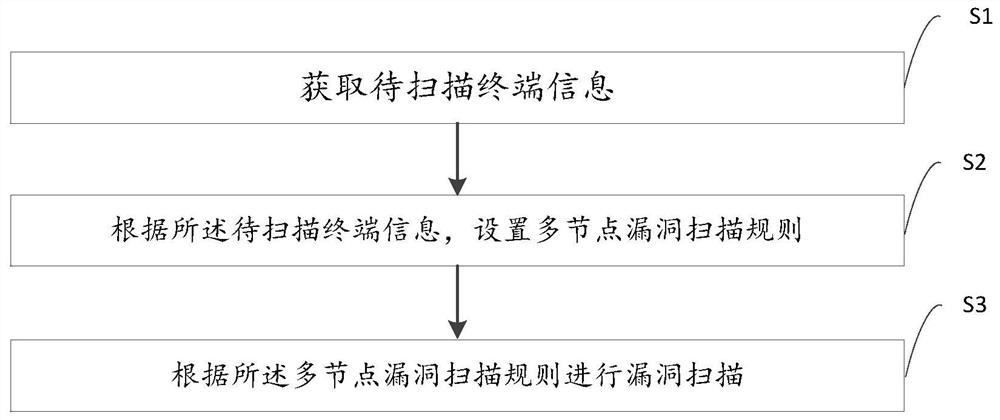
[0034] see figure 1 , is a flow chart of the multi-node vulnerability scanning method of the present invention. Such as figure 1 As shown, in the multi-node vulnerability scanning method provided in the first embodiment of the present invention, at least the steps include,
[0035] S1. Acquiring terminal information to be scanned.
[0036] Terminal information to be scanned, in general, includes services on different ports of the target host’s ICP / IP, for example, whether anonymous login is possible, whether there is a writable FTP directory, whether Telnet, httpd can be used, whether it is running as root, etc. etc., the allocation of various TCP / IP ports of the Web server, open services, Web service software versions, and the information presented by these services and software on the Internet, etc.
[0037] For example, in the scan of TCP port 80, if / cgi-bin / phf or / cgi-bin / count, cgi is found, according to the sharing and standardization of CGI programs, it can be spec...
Embodiment 2
[0088] see figure 2 , is a schematic structural diagram of a multi-node vulnerability scanning device of the present invention. Such as figure 2 As shown, in the multi-node vulnerability scanning device provided in the first embodiment of the present invention, at least include:
[0089] A multi-node vulnerability scanning device, comprising:
[0090] The terminal information acquisition module to be scanned is used to acquire terminal information to be scanned;
[0091] The multi-node vulnerability scanning rule setting module is used to set multi-node vulnerability scanning rules according to the terminal information to be scanned;
[0092] The vulnerability scanning module is used to perform vulnerability scanning according to multi-node vulnerability scanning rules.
[0093] In specific implementation, the Phytium FT-1500A / 16 core processor can be used to scan for vulnerabilities, adopt a distributed architecture, design a multi-task and multi-node vulnerability scan...
Embodiment 3
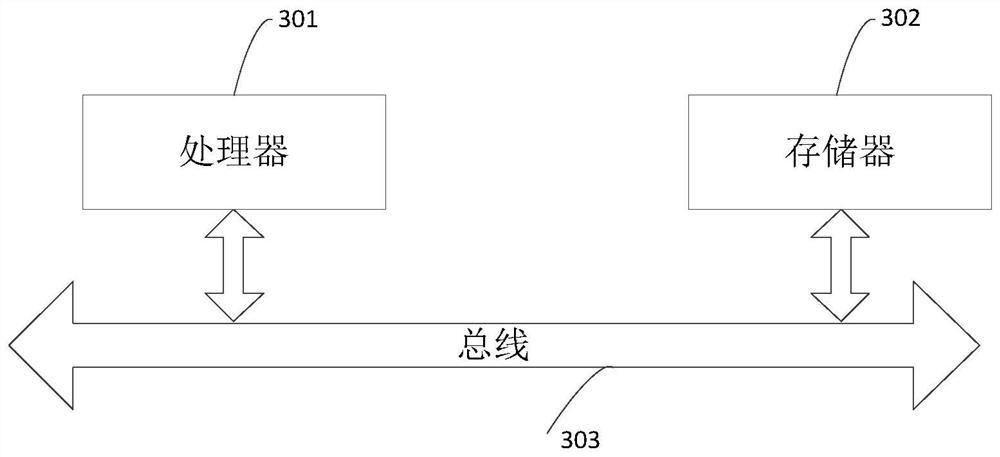
[0097] image 3 It is a schematic diagram of a physical structure of an electronic device provided according to an embodiment of the present invention. Based on the content of the above-mentioned embodiments, such as image 3 As shown, the electronic device may include: a processor (processor) 301, a memory (memory) 302 and a bus 303; wherein, the processor 301 and the memory 302 complete mutual communication through the bus 303; the processor 301 is used to call the memory stored in The computer program instructions in the memory 302 and operable on the processor 301 to execute the multi-node vulnerability scanning methods provided by the above method embodiments include, for example:
[0098] S1. Acquiring terminal information to be scanned;
[0099] S2. Set multi-node vulnerability scanning rules according to the terminal information to be scanned;
[0100] S3. Vulnerability scanning is performed according to multi-node vulnerability scanning rules.
[0101] In addition...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com