Computer information security monitoring device and use method thereof
A monitoring device and information security technology, applied in the field of computer aided equipment, can solve the problems of easy impact on the monitoring device, damage to electronic components, damage to the monitoring device, etc., to avoid impact damage, reduce the frequency of vibration, and prolong the service life.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
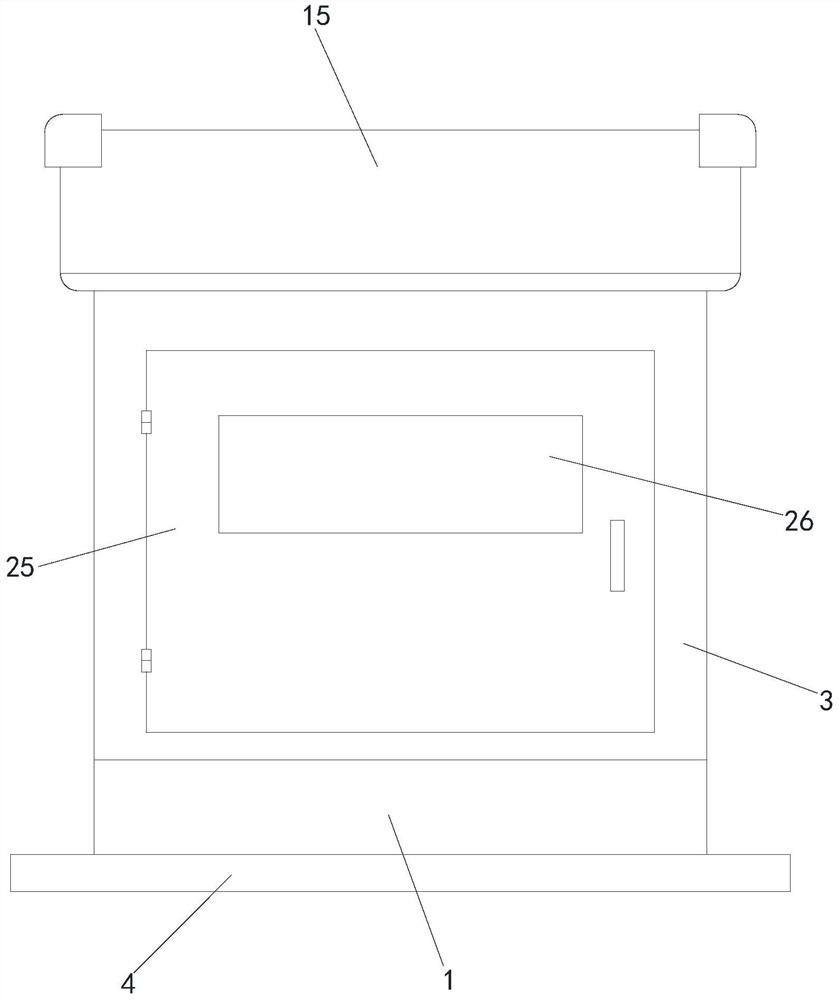
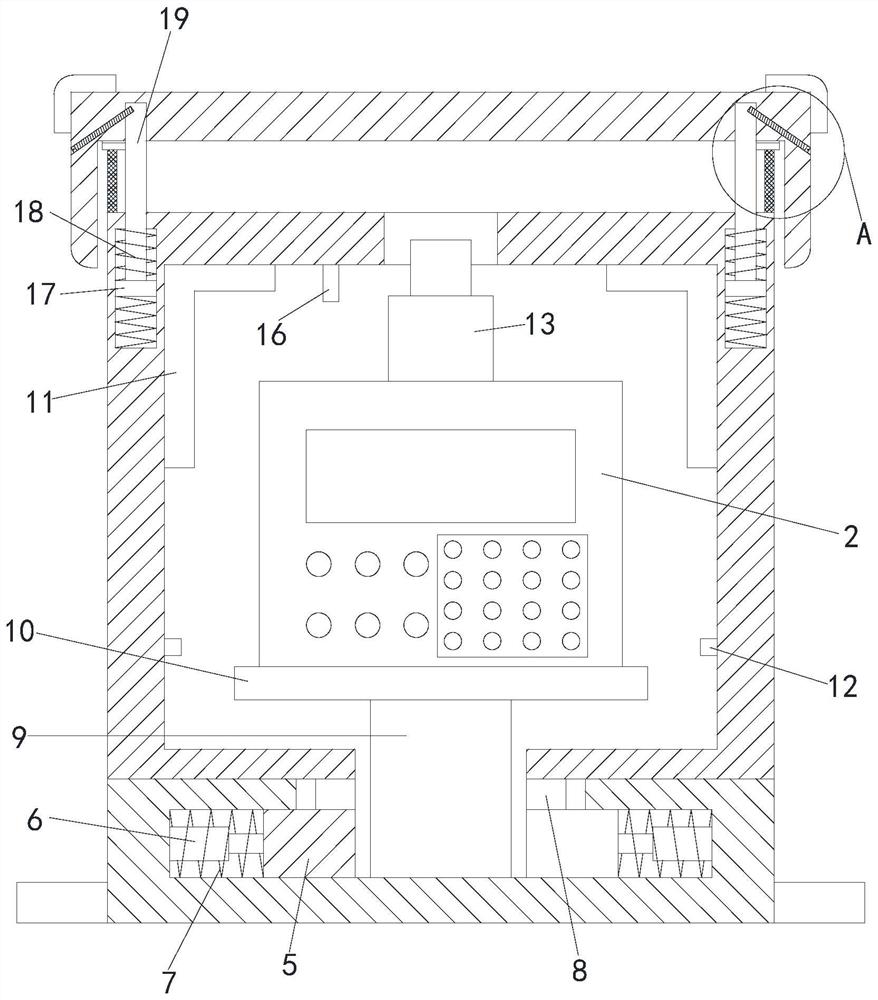
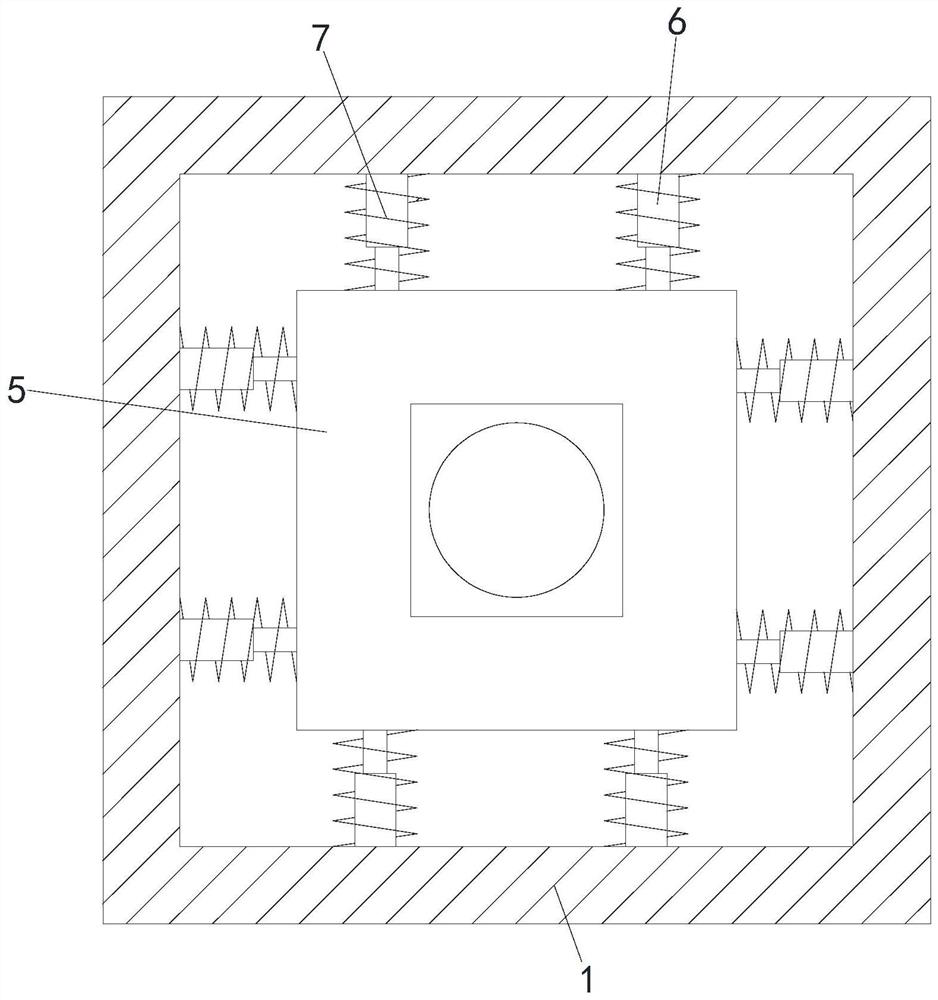
[0032] see Figure 1-4 , a computer information security monitoring device, comprising a base 1, a monitoring device body 2 and a protection box 3, characterized in that the outer bottom side of the base 1 is fixedly connected with a mounting ring 4, and the inside of the base 1 is provided with a square groove, and the square groove Slip ring 5 is installed in the inner slide of the square groove, and the slip ring 5 is set in a square structure to prevent the slip ring 5 from rotating inside the square groove. The inner side wall of the square groove is evenly connected with a plurality of dampers 6, and the plurality of dampers 6 are far away from the square groove. One end of the inner wall of the groove is evenly in contact with the outer wall of the slip ring 5, and the outer walls of a plurality of dampers 6 are provided with first damping springs 7, and the top of the base 1 is provided with a connecting groove communicating with the square groove, and the connecting gr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com