Tor website fingerprint identification method based on attention mechanism and LSTM
A technology of fingerprint identification and attention, which is applied in the field of network security, can solve the problems of low accuracy of fingerprint identification and achieve the effect of preventing over-fitting phenomenon
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] A Tor website fingerprinting method based on attention mechanism and LSTM, which specifically includes the following steps:
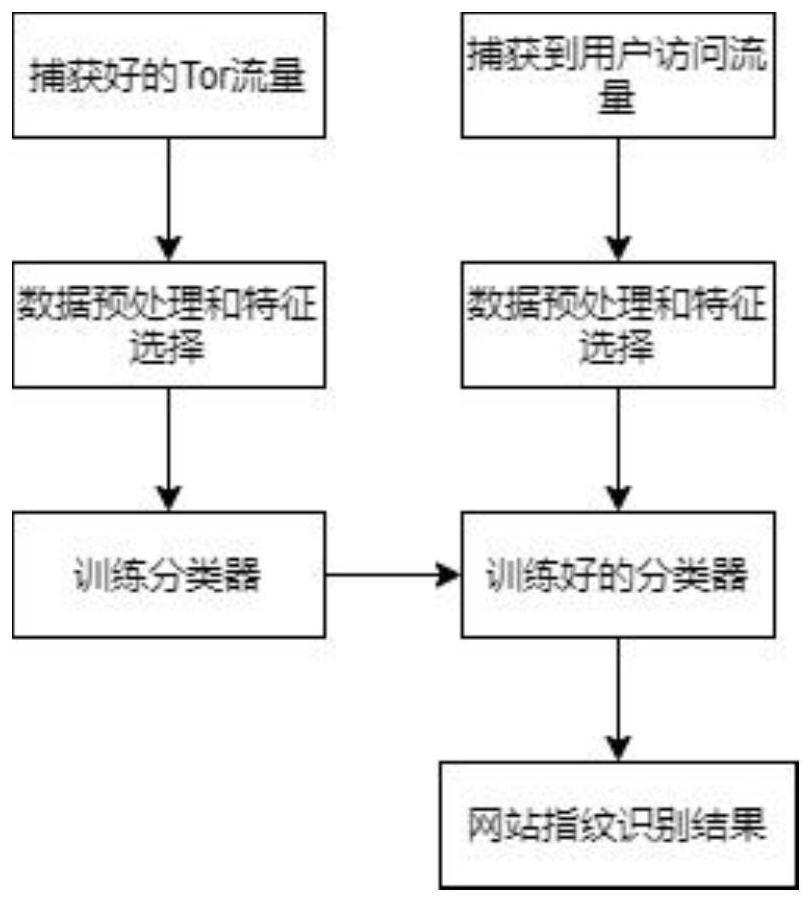
[0037] Step 1. Traffic capture: Use the tcpdump tool to collect access traffic, and label each access traffic to capture the access traffic of the monitored website;
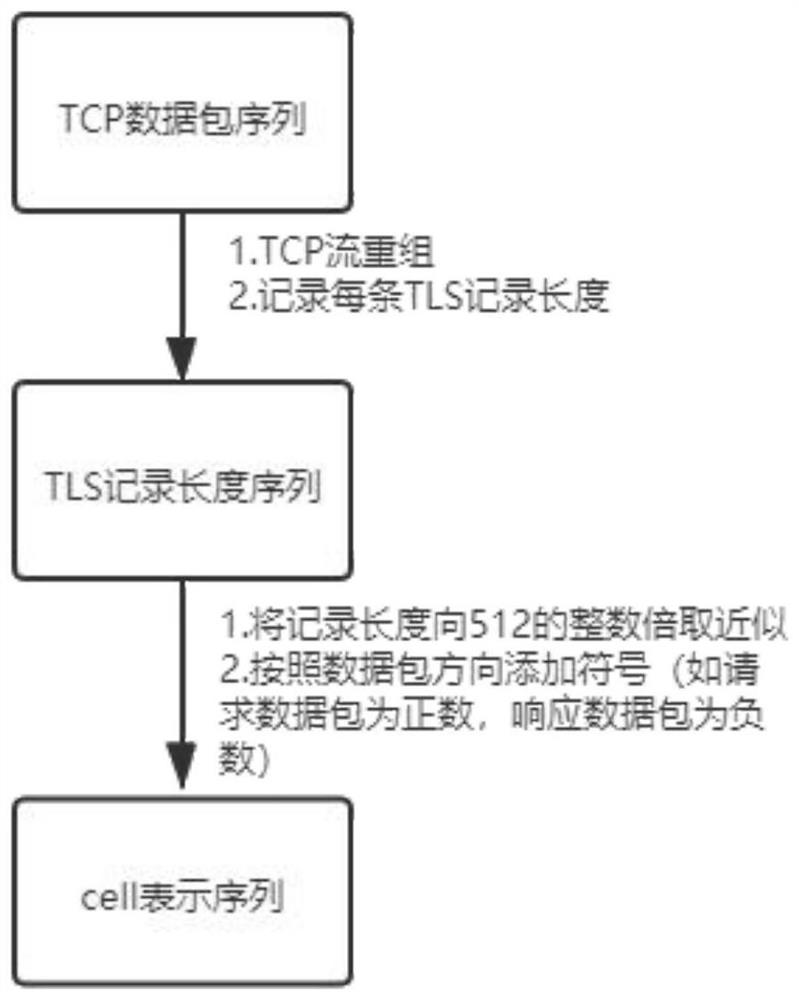
[0038] Step 2: Feature screening: Data preprocessing is performed on the captured access traffic to obtain a sequence of TLS record lengths. The TLS record length is approximated to an integer multiple of 512, symbols are added according to the direction of the data packets, and finally converted into a cell representation sequence, as Input to the website fingerprinting model;
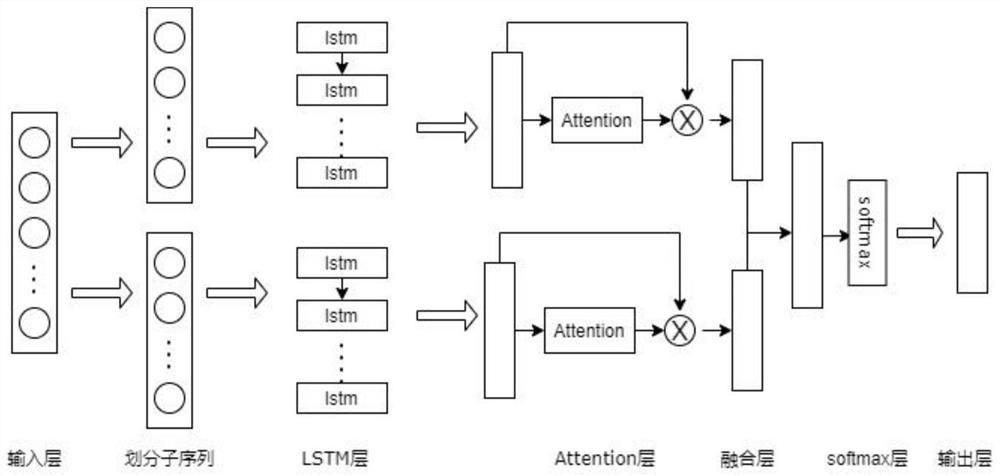
[0039]Step 3. Model construction: Build the input layer, Partition layer, LSTM layer, attention mechanism layer, fusion layer and softmax layer, build a classifier model based on attention mechanism and LSTM, and input the cell representation sequence in step 2 into In the model, the cell representation s...
Embodiment 2
[0043] This embodiment is an improvement of the previous embodiment, a method for fingerprinting Tor website based on attention mechanism and LSTM, which specifically includes the following steps:
[0044] Step 1. Traffic capture: first set the list of websites to be monitored, and obtain the addresses of the monitored websites, visit the monitored websites in sequence through Tor Browser, visit each website 1000 times, use the tcpdump tool to collect the access traffic, and analyze the Each access traffic is tagged, that is, the website category to which the access traffic belongs, and the access traffic of the monitored website is captured;
[0045] Step 2: Feature screening: perform data preprocessing on the captured access traffic, perform TCP stream reorganization on the TCP data packet sequence, record the length of each TLS record, convert it into a TLS record length sequence, and obtain a TLS record length sequence, Approximate the length of the TLS record to an intege...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com