External program calling method and system based on environment isolation mechanism
An environment isolation and external program technology, applied in the computer field, can solve the problems of single applicable scene and complex deployment method, and achieve the effect of alleviating the single applicable scene and strong versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
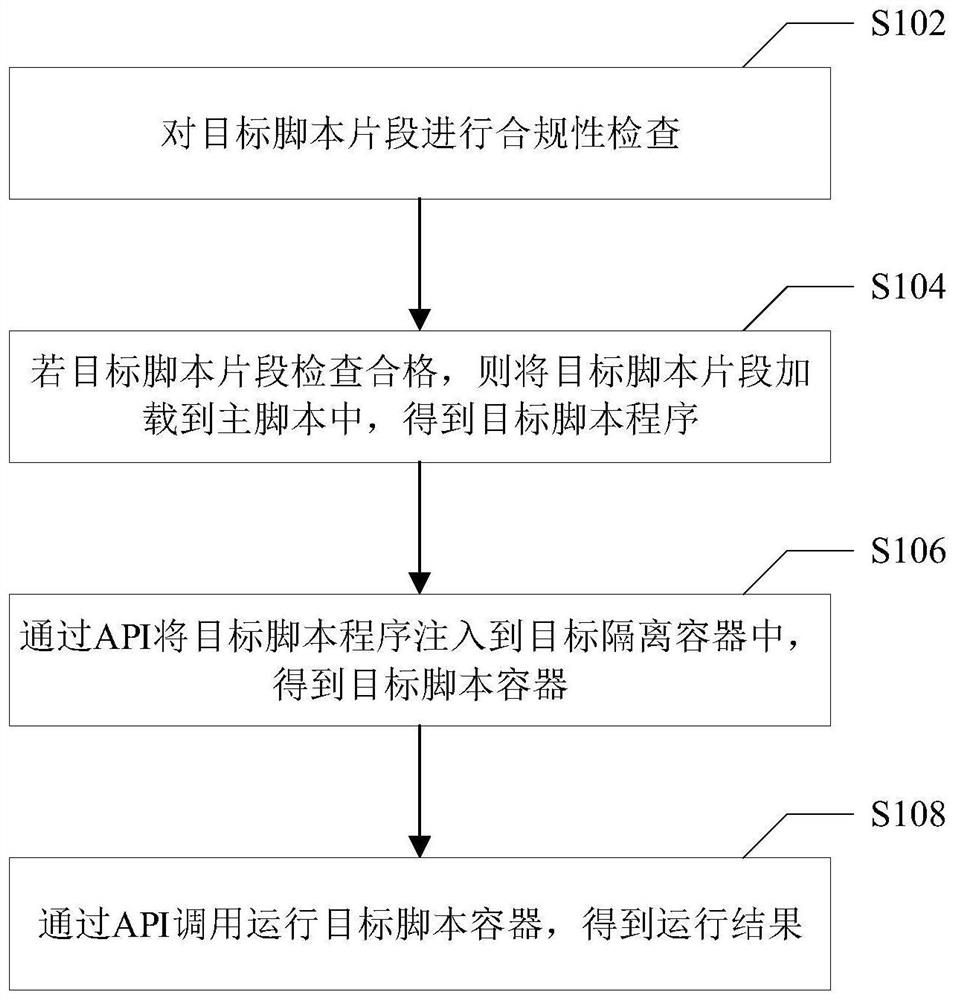
[0024] figure 1 It is a flowchart of an external program calling method based on an environment isolation mechanism provided according to an embodiment of the present invention. like figure 1 As shown, the method specifically includes the following steps:
[0025] In step S102, the target script fragment is checked for compliance.
[0026] Optionally, in this embodiment of the present invention, the compliance check includes: a security check and a rule check.
[0027] Specifically, script fragments are first written according to the established rules, and the security verification of the script fragments will be carried out after the writing is completed. After the verification is passed, the main script program will be verified, and the main script management program will verify the incoming parameters and the rules of the script fragments.
[0028] Step S104, if the target script fragment is checked, load the target script fragment into the main script to obtain the targ...
Embodiment 2
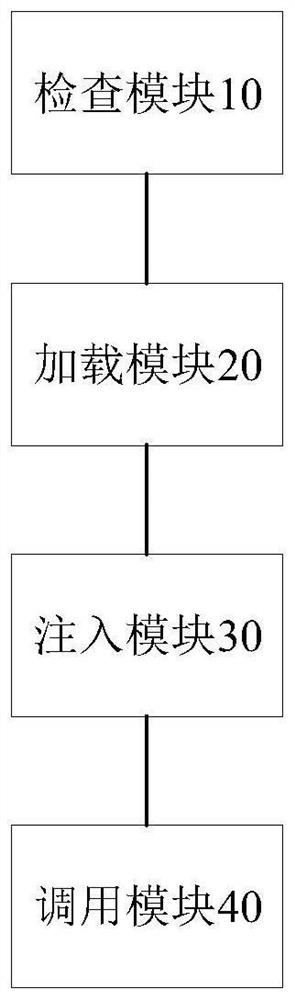
[0040] figure 2 It is a schematic diagram of an external program calling system based on an environment isolation mechanism provided according to an embodiment of the present invention. like figure 2 As shown, the system includes: a checking module 10 , a loading module 20 , an injecting module 30 and a calling module 40 .
[0041] Specifically, the checking module 10 is configured to perform compliance checking on the target script fragment. Optionally, the checking module 10 is further configured to: perform security checking and rule checking on the target script fragment.
[0042] The loading module 20 is configured to load the target script fragment into the main script to obtain the target script program if the target script fragment passes the check.
[0043] The injection module 30 is used for injecting the target script program into the target isolation container through the API to obtain the target script container. Optionally, the target isolation container is...
Embodiment 3
[0048] Figure 4It is a schematic structural diagram of a script processing program provided according to an embodiment of the present invention. like Figure 4 As shown, the script handler includes a script fragment security check, a script fragment rule check, a main run script validator, a container generator, and a main script program.
[0049] Among them, the script fragment security check is used to check whether the submitted script fragment of the main operation logic is safe, using static code scanning and security rule checking.
[0050] Script fragment rule checking is used to check the compliance of script fragments. Only script fragments that meet the rules can be run.
[0051] The main run script validator, which validates the incoming script parameters of the main script.
[0052] The container generator is used to package the main script runner after all rules are verified, and notify the container maintenance program in the form of API to generate one or mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com